Introduction
The traditional network security perimeter is changing as more companies move to either a hybrid cloud environment, with some resources located on-premises and some in the cloud, or a fully cloud-based network solution. Protection of your organization's assets, resources, and data is essential.
Threats can come from any direction: for instance, a Denial of Service attack on your organization’s services, or a hacker trying to access your network by attempting to penetrate your firewall. Azure offers a wide array of configurable security tools that can be customized to give you the security and control to meet your organization's needs.
In this lesson, you’ll explore many different services and features of Azure that can help protect your networks, assets, and resources, including network security groups, Azure Firewall, and Azure DDoS protection. You’ll also look at the different ways in which encryption is used to protect your data.
After completing this lesson, you'll be able to:
-
Describe Azure security capabilities for protecting your network.
-
Describe how Azure can protect your VMs.
-
Describe how encryption on Azure can protect your data.
Describe Azure Network Security groups
In today’s modern work environment, where more users are working remotely from home, managing access to assets and resource on your Azure virtual network (VNet) is essential.
Here, you’ll learn how Azure network security groups can automatically allow or deny traffic to your cloud-based resources and assets.
An Azure virtual network is similar to the network you’d find in your organization. It enables different Azure resources, for instance, an Azure virtual machine (VM), to securely communicate with other VNets, the internet, or your on-premises network. A VNet can be divided into multiple subnetworks (subnets), each with specific resources assigned to them. You can secure the resources within a subnet using network security groups.
Network security groups
Network security groups (NSGs) let you allow or deny network traffic to and from Azure resources that exist in your Azure virtual network; for example, a virtual machine. An NSG consists of rules that define how the traffic is filtered. You can associate zero, or one, network security group to each virtual network subnet and network interface in a virtual machine. The same network security group, however, can be associated to as many subnets and network interfaces as you choose.
NSG security rules are evaluated by priority using five information points: source, source port, destination, destination port, and protocol to either allow or deny the traffic. As a guideline, you shouldn't create two security rules with the same priority and direction.

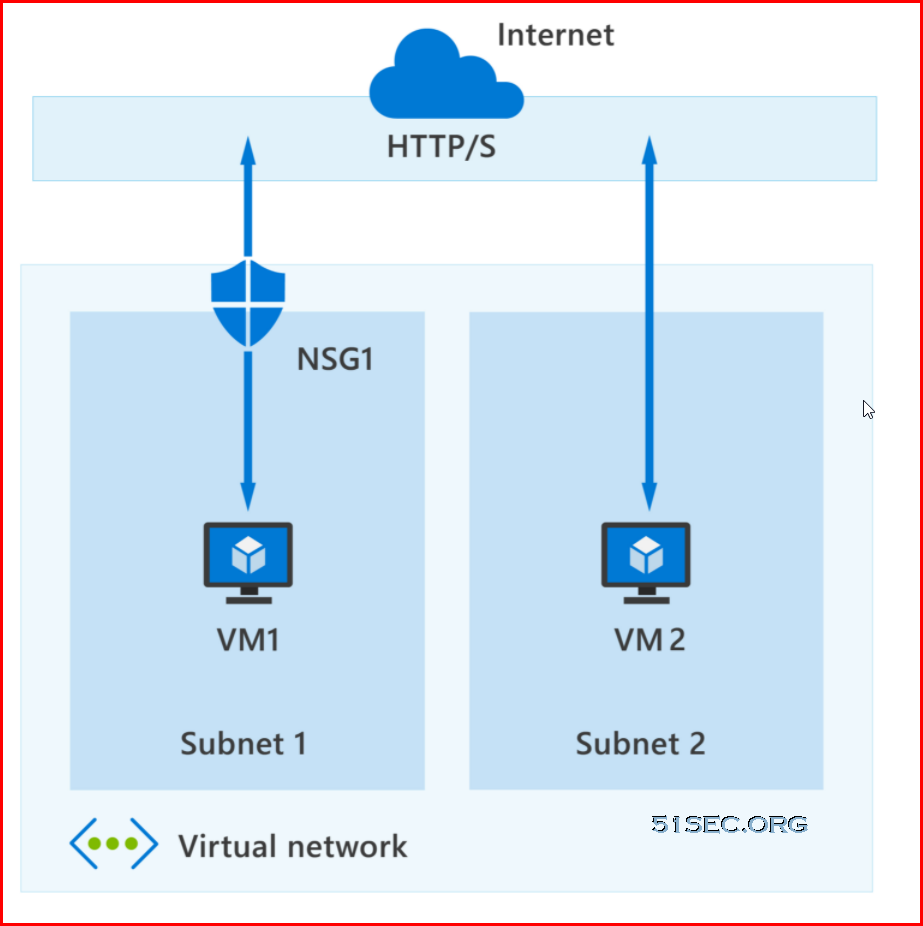
In the above, highly simplified, diagram you can see an Azure virtual network with two subnets that are connected to the internet, and each subnet has a virtual machine. Subnet 1 has an NSG assigned to it that's filtering inbound and outbound access to VM1, which needs a higher level of access. In contrast, VM2 could represent a public-facing machine that doesn't require an NSG.
Inbound and outbound security rules
As you’ve seen, an NSG controls access to resources on your virtual network and any subnets. An NSG is made up of inbound and outbound security rules. For each rule, you can specify a source and destination, port, protocol, and the required action if it's triggered. As previously mentioned, the rules are processed based on their priority. By default, Azure creates a series of rules, three inbound and three outbound rules, to provide a baseline level of security. You can't remove the default rules, but you can override them by creating new rules with higher priorities.
Each rule specifies one or more of the following properties:
-
Name: Every NSG rule needs to have a unique name that describes its purpose. For example, AdminAccessOnlyFilter.
-
Priority: A number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers. When traffic matches a rule, processing stops. This means that any other rules with a lower priority (higher numbers) won't be processed.
-
Source or destination: Specify either individual IP address or an IP address range, service tag (a group of IP address prefixes from a given Azure service), or application security group. Specifying a range, a service tag, or application security group, enables you to create fewer security rules.
-
Protocol: What network protocol will the rule check? The protocol can be any of: TCP, UDP, ICMP or Any.
-
Direction: Whether the rule should be applied to inbound or outbound traffic.
-
Port range: You can specify an individual or range of ports. For example, you could specify 80 or 10000-10005. Specifying ranges enables you to be more efficient when creating security rules. You can't specify multiple ports or port ranges in the same security rule in NSGs created through the classic deployment model.
-
Action: Finally, you need to decide what will happen when this rule is triggered.
There are limits to the number of security rules you can create in an NSG. Use Azure NSGs to automatically allow or deny traffic to your cloud-based resources and assets.
Describe Azure DDoS protection
Any company, large or small, can become the target of a large-scale network attack. The nature of these attacks against your network might be simply to make a statement, or simply because the attacker wanted a challenge.
Distributed Denial of Service Attacks
The aim of a Distributed Denial of Service (DDoS) attack is to overwhelm the resources on your applications and servers, making them unresponsive or slow for genuine users. A DDoS attack will usually target any public-facing endpoint that can be accessed through the Internet.
The three most popular types of Distributed Denial of Service attack are:
-
Volumetric attacks: These are volume-based attacks that flood the network with seemingly legitimate traffic, overwhelming the available bandwidth. Legitimate traffic isn't able to get through. These types of attacks are measured in bits per second.
-
Protocol attacks: Protocol attacks render a target inaccessible by exhausting server resources with false protocol requests that exploit weaknesses in layer 3 (network) and layer 4 (transport) protocols. These types of attacks are typically measured in packets per second.
-
Resource (application) layer attacks: These attacks target web application packets, to disrupt the transmission of data between hosts.
What is Azure DDoS Protection
The Azure DDoS Protection service is designed to help protect your applications and servers by analyzing network traffic and discarding anything that looks like a DDoS attack.

In the diagram above, Azure DDoS Protection identifies the attacker's attempt to overwhelm the network. It blocks traffic from the attacker, ensuring that traffic never reaches Azure resources. Legitimate traffic from customers still flows into Azure without any interruption of service.
Azure DDoS Protection uses the scale and elasticity of Microsoft's global network to bring DDoS mitigation capacity to every Azure region. During a DDoS attack, Azure can scale your computing needs to meet demand. DDoS Protection can manage your cloud consumption by ensuring that your network load only reflects actual customer usage.
Azure DDoS Protection comes in two tiers:
-
Basic: The Basic service tier is automatically enabled, for every property in Azure, at no extra cost. as part of the Azure platform. Always-on traffic monitoring and real-time mitigation of common network-level attacks provide the same defenses that Microsoft’s online services use. Azure’s global network is used to distribute and mitigate attack traffic across regions.
-
Standard: The Standard service tier provides extra mitigation capabilities that are tuned specifically to Microsoft Azure Virtual Network resources. DDoS Protection Standard is simple to enable and requires no application changes. Protection policies are tuned through dedicated traffic monitoring and machine learning algorithms. Policies are applied to public IP addresses, which are associated with resources deployed in virtual networks, such as Azure Load Balancer and Application Gateway.
Azure DDoS pricing
The DDoS Standard Protection service will have a fixed monthly charge. The fixed monthly charge includes protection for 100 resources. Protection for additional resources will be charged on a monthly per-resource basis.
For more information on pricing, visit the Azure DDoS Protection pricing page.
Use Azure DDoS to enable you to protect your devices and applications by analyzing traffic across your network, and taking appropriate action on suspicious traffic.
Describe what is Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure virtual network (VNet) resources from attackers. You can deploy Azure Firewall on any virtual network but the best approach is to use it on a centralized virtual network. All your other virtual and on-premises networks will then route through it. The advantage of this model is the ability to centrally exert control of network traffic for all your VNets across different subscriptions.

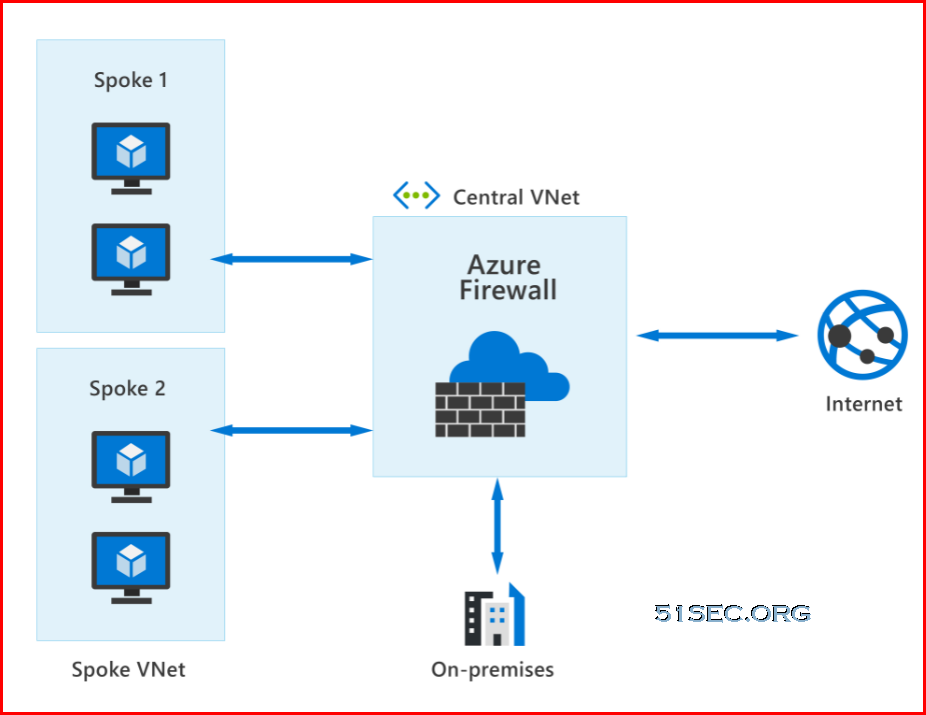
With Azure Firewall, you can scale up the usage to accommodate changing network traffic flows, so you don't need to budget for peak traffic. Network traffic is subjected to the configured firewall rules when you route it to the firewall as the subnet default gateway.
Key features of Azure Firewall
Azure Firewall comes with many features, including but not limited to:
-
Built-in high availability and availability zones: High availability is built in so there's nothing to configure. Also, Azure Firewall can be configured to span multiple availability zones for increased availability.
-
Network and application level filtering: Use IP address, port, and protocol to support fully qualified domain name filtering for outbound HTTP(s) traffic and network filtering controls.
-
Outbound SNAT and inbound DNAT to communicate with internet resources: Translate the private IP address of network resources to an Azure public IP address (source network address translation) to identify and allow traffic originating from the virtual network to internet destinations. Similarly, inbound internet traffic to the firewall public IP address is translated (Destination Network Address Translation) and filtered to the private IP addresses of resources on the virtual network.
-
Multiple public IP addresses: Multiple public IP addresses (up to 250) can be associated wtih your firewall.
-
Threat intelligence: Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains.
-
Integration with Azure Monitor: Integrated with Azure Monitor to enable collecting, analyzing, and acting on telemetry from Azure Firewall logs.
Use Azure Firewall to help protect the Azure resources you've connected to Azure Virtual Networks.
Describe what is Azure Bastion
Let’s assume you’ve set up multiple virtual networks that use a combination of NSGs and Azure Firewalls to protect and filter access to the assets and resources, including virtual machines (VMs). You're now protected from external threats, but need to allow your developers and data scientist, who are working remotely, direct access to those VMs.
In a traditional model, you’d need to expose the Remote Desktop Protocol (RDP) and Secure Shell (SSH) ports to the internet. These protocols can be used to gain remote access to your VMs. This process creates a significant surface threat that can be exploited by attackers.

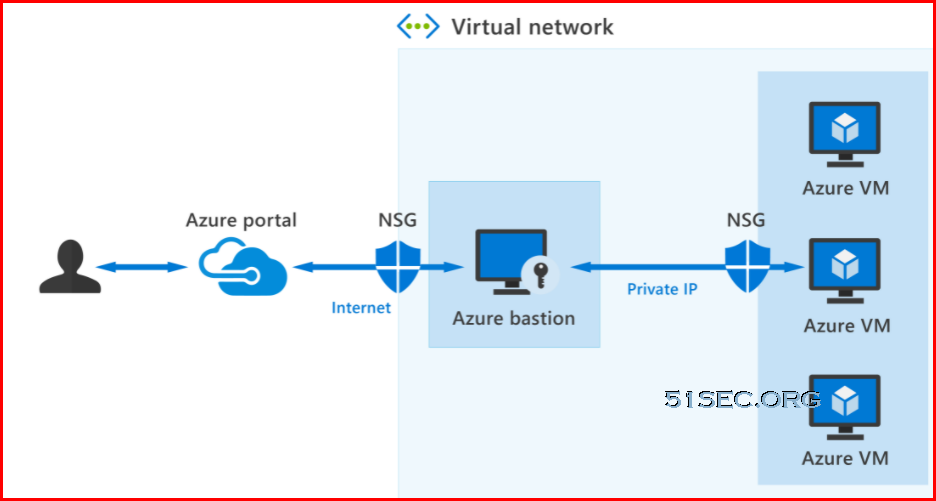
Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal using Transport Layer Security (TLS). When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software.
Bastion provides secure RDP and SSH connectivity to all VMs in the virtual network in which it's provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
Azure Bastion deployment is per virtual network, not per subscription/account or virtual machine. When you provision an Azure Bastion service in your virtual network, the RDP/SSH experience is available to all your VMs in the same virtual network.
Key features of Azure Bastion
The following features are available:
-
RDP and SSH directly in Azure portal: You get to the RDP and SSH session directly in the Azure portal, using a single-click experience.
-
Remote session over TLS and firewall traversal for RDP/SSH: Use an HTML5-based web client that's automatically streamed to your local device. You'll get your Remote Desktop Protocol (RDP) and Secure Shell (SSH) to traverse the corporate firewalls securely.
-
No Public IP required on the Azure VM: Azure Bastion opens the RDP/SSH connection to your Azure virtual machine using private IP on your VM. You don't need a public IP.
-
No hassle of managing NSGs: A fully managed platform PaaS service from Azure that's hardened internally to provide secure RDP/SSH connectivity. You don't need to apply any NSGs on an Azure Bastion subnet.
-
Protection against port scanning: Because you don't need to expose your virtual machines to the internet, your VMs are protected against port scanning by rogue and malicious users located outside your virtual network.
-
Protect against zero-day exploits: A fully platform-managed PaaS service. Because it sits at the perimeter of your virtual network, you don’t need to worry about hardening each virtual machine in the virtual network. The Azure platform protects against zero-day exploits by keeping the Azure Bastion hardened and always up to date for you.
Use Azure Bastion to establish secure RDP and SSH connectivity to your virtual machines in Azure.
Describe what is Web Application Firewall
So far, we’ve looked at the traditional security concerns for the protection of your assets, resources, and data from external attack by using firewalls and network security groups. But there's another threat surface now being exploited by hackers: web applications.
Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities, like SQL injection and cross-site scripting. Preventing such attacks in application code is challenging. It can require rigorous maintenance, patching, and monitoring.
Web Application Firewall (WAF) provides centralized protection of your web applications from common exploits and vulnerabilities. A centralized WAF helps make security management simpler, improves the response time to a security threat, and allows patching a known vulnerability in one place, instead of securing each web application. A WAF also gives application administrators better assurance of protection against threats and intrusions.

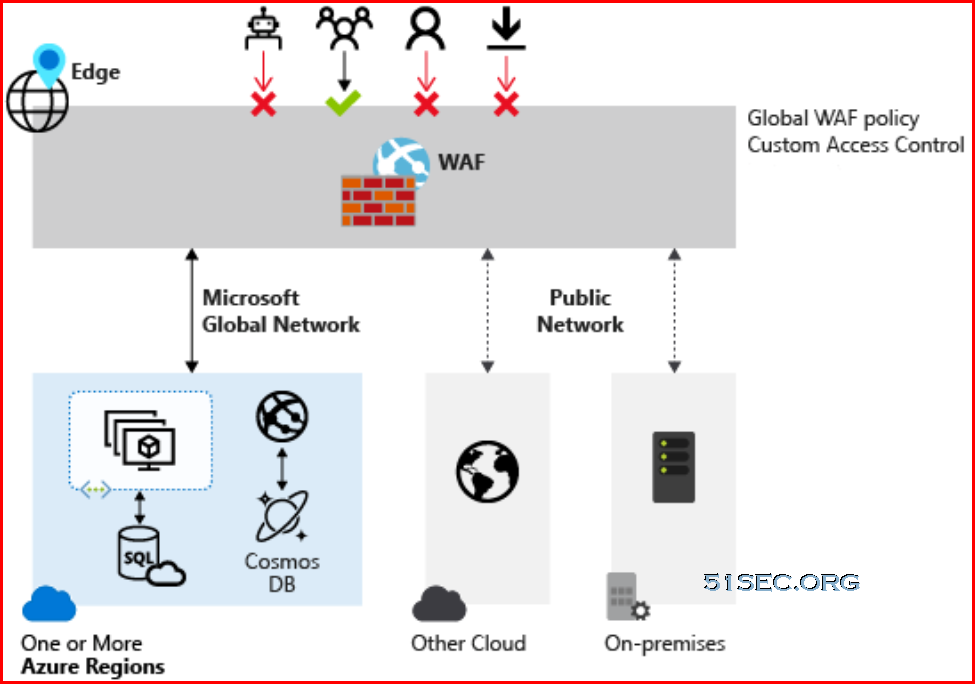
Supported services
WAF can be deployed with Azure Application Gateway, Azure Front Door, and Azure Content Delivery Network (CDN) services from Microsoft. WAF has features that are customized for each specific service.
Use Azure WAF to achieve centralized protection for your web applications from common exploits and vulnerabilities.
Describe ways Azure encrypts data
Espionage, data theft, and data exfiltration are a real threat to any company. The loss of sensitive data can be crippling and have legal implications. For most organizations, data is their most valuable asset. In a layered security strategy, the use of encryption serves as the last and strongest line of defense.
Encryption on Azure
Microsoft Azure provides many different ways to secure your data, each depending on the service or usage required.
-
Azure Storage Service Encryption helps to protect data at rest by automatically encrypting before persisting it to Azure-managed disks, Azure Blob Storage, Azure Files, or Azure Queue Storage, and decrypts the data before retrieval.
-
Azure Disk Encryption helps you encrypt Windows and Linux IaaS virtual machine disks. Azure Disk Encryption uses the industry-standard BitLocker feature of Windows and the dm-crypt feature of Linux to provide volume encryption for the OS and data disks.
-
Transparent data encryption (TDE) helps protect Azure SQL Database and Azure Data Warehouse against the threat of malicious activity. It performs real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
What is Azure Key Vault?
Azure Key Vault is a centralized cloud service for storing your application secrets. Key Vault helps you control your applications' secrets by keeping them in a single, central location and by providing secure access, permissions control, and access logging capabilities. It's useful for different kinds of scenarios:
-
Secrets management. You can use Key Vault to store securely and tightly control access to tokens, passwords, certificates, Application Programming Interface (API) keys, and other secrets.
-
Key management. You can use Key Vault as a key management solution. Key Vault makes it easier to create and control the encryption keys used to encrypt your data.
-
Certificate management. Key Vault lets you provision, manage, and deploy your public and private Secure Sockets Layer/ Transport Layer Security (SSL/ TLS) certificates for Azure, and internally connected, resources more easily.
-
Store secrets backed by hardware security modules (HSMs). The secrets and keys can be protected either by software or by FIPS 140-2 Level 2 validated HSMs.
Use the various ways in which Azure can encrypt your data to help you secure it, whatever the location or state.
Knowledge check
Multiple choice
Item 1. The security admin has created an Azure Network Security Group (NSG) to filter network traffic to a virtual machine. The admin wants to allow inbound traffic using the Remote Desktop Protocol (RDP), but the default NSG rules are currently blocking all inbound traffic that is not from another virtual network or an Azure load balancer. What does the security admin have to do to allow inbound traffic using RDP?
Multiple choice
Item 2. The security admin wants to protect Azure resources from DDoS attacks, which Azure DDoS Protection tier will the admin use to target Azure Virtual Network resources?
Multiple choice
Item 3. Your organization has several virtual machines in Azure. The security admin wants to deploy Azure Bastion to get secure access to the virtual machines in Azure. What should the admin keep in mind?
Multiple choice
Item 4. Much of your organization’s application data is in Azure. The security admin wants to take advantage of the encryption capabilities in Azure, which service would the admin use to store the application’s secrets?
Summary and resources
The traditional network security perimeter protects your organization's assets, resources, where data is essential. Azure offers a wide range of configurable security tools that are customized to give the security and control to meet your organization's needs.
You’ve explored the different service offerings provided by Microsoft Azure, including network security groups, using Web Application, and regular Azure Firewalls to protect access to your systems. You now understand the importance and use of encryption of data not only when stored, but also when in transit.
You've explored the nature of DDoS and how Azure helps protect your systems against that form of attack. Finally, you saw how Azure Bastion helps secure connections to any virtual machine in your estate.
Without these security tools, your organization would be vulnerable to data theft, unable to respond swiftly to malicious attacks on your web and data services, and wouldn't meet your security obligations.
Now that you've completed this lesson, you should be able to:
-
Describe Azure’s security capabilities for protecting your network.
-
Describe how Azure can protect your VMs.
-
Describe how encryption on Azure can protect your data.
Learn more
To find out more about any of the topics covered in this lesson, go to: