Introduction
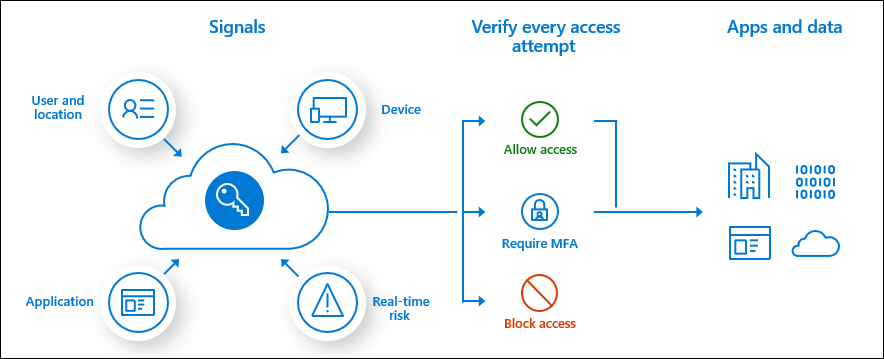
When it comes to security, your organization can no longer rely on its network boundary. To allow employees, partners, and customers to collaborate securely, identity has become the new security perimeter. Using an identity provider gives your organization the ability to manage all aspects of identity security.
This lesson introduces you to Azure Active Directory (Azure AD), Microsoft’s cloud-based identity and access management service. In this module, you'll learn about the benefits of using a cloud-based identity provider, including single sign-on for users. You'll also find out about the different Azure AD editions, the identity types supported by Azure AD, and how you can use it to support external users.
After completing this lesson, you'll be able to:
-
Describe what Azure AD does.
-
Describe the identity types that Azure AD supports.
- describing what Azure Active Directory is (Microsoft Documentation: Azure Active Directory, Explaining what is Azure Active Directory)
- describe Azure AD identities (users, devices, groups, service principals/applications) (Microsoft Documentation: Azure AD identity types)
- describing what hybrid identity is (Microsoft Documentation: concept of hybrid identities)
- describe the different external identity types (Guest Users) (Microsoft Documentation: types of external identities)
Describe the basic identity services and identity types of Azure AD
- What is Azure Active Directory?
- Explain Azure AD identity types
- Explain the concept of hybrid identities
- Types of external identities
Describe Azure Active Directory
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. Organizations use Azure AD to enable their employees, guests, and others to sign in and access the resources they need, including:
-
Internal resources, such as apps on your corporate network and intranet, and cloud apps developed by your own organization.
-
External services, such as Microsoft Office 365, the Azure portal, and any SaaS applications used by your organization.
Azure AD simplifies the way organizations manage authorization and access by providing a single identity system for their cloud and on-premises applications. Azure AD can be synchronized with your existing on-premises Active Directory, synchronized with other directory services, or used as a standalone service.
Azure AD also allows organizations to securely enable the use of personal devices, such as mobiles and tablets, and enable collaboration with business partners and customers.


Azure AD is used by IT admins to control access to corporate apps and resources, based on business requirements. It can also be set up to require multi-factor authentication when accessing important organizational resources. Azure AD can be used to automate user provisioning between an existing Windows Server AD and cloud apps, including Microsoft 365. Finally, Azure AD provides powerful tools to automatically help protect user identities and credentials and to meet an organization’s access governance requirements.
Developers use Azure AD as a standards-based approach for adding single sign-on (SSO) to their apps, so that users can sign in with their pre-existing credentials. Azure AD also provides APIs that allow developers to build personalized app experiences using existing organizational data.
Each Microsoft 365, Office 365, Azure, or Dynamics 365 Online subscription automatically uses an Azure AD tenant. Users of these services can take advantage of Azure AD services such as self-service password reset, provided it has been configured by their organization’s admins.
Azure AD is available in four editions: Free, Office 365 Apps, Premium P1, and Premium P2. For more information on what is included with each of these editions, refer to Azure Active Directory Pricing.
Describe the Azure AD identity types
Azure AD manages different types of identities: users, service principals, managed identities, and devices. In this topic, we consider each type of Azure AD identity.
User
A user identity is a representation of something that is managed by Azure AD. Employees and guests are represented as users in Azure AD. If you have several users with the same access needs, you can create a group. Groups allow you to assign access permissions to all the members of the group, instead of having to assign the access rights individually.
Azure AD business-to-business (B2B) collaboration, a feature within External Identities, includes the capability to add guest users. With B2B collaboration, an organization can securely share applications and services with guest users from another organization.
Interactive guide
In the following interactive guide, you will add a new user to Azure Active Directory. Select the link below to get started.
Interactive guide - Add a new user to Azure Active Directory
Service Principal
A service principal is a security identity used by applications or services to access specific Azure resources. You can think of it as an identity for an application.
For an application to delegate its identity and access functions to Azure AD, the application must first be registered with Azure AD. The process of registering the application creates a globally unique app object which is stored in your home tenant or directory. A service principal is created in each tenant where the application is used and references the globally unique app object. The service principal defines what the app can do in the tenant, such as who can access the app, and what resources the app can access.
Managed Identity
A managed identity is an identity in Azure Active Directory that is automatically managed by Azure. Managed identities are typically used to manage the credentials for authenticating a cloud application with an Azure service.
There are several benefits to using managed identities, including:
-
Application developers can authenticate to services that support managed identities for Azure resources. For a complete list of services, refer to Azure Services that support managed identities.
-
Any Azure service that supports Azure AD authentication can use managed identities to authenticate to another Azure service, for example accessing Azure Key Vault.
-
Managed identities can be used without any additional cost.
There are two types of managed identities: system-assigned and user-assigned.
System-assigned. Some Azure services allow you to enable a managed identity directly on a service instance. When you enable a system-assigned managed identity, an identity is created in Azure AD that is tied to the lifecycle of that service instance. When the resource is deleted, Azure automatically deletes the identity for you. By design, only that Azure resource can use this identity to request tokens from Azure AD.
User-assigned. You may also create a managed identity as a standalone Azure resource. A user-assigned managed identity is assigned to one or more instances of an Azure service. You can create a user-assigned managed identity and assign it to one or more instances of an Azure service. In the case of user-assigned managed identities, the identity is managed separately from the resources that use it.
The following table summarizes the differences between system-assigned and user-assigned managed identities:
|
Property |
System-assigned managed identity |
User-assigned managed identity |
|
Creation |
Created as part of an Azure resource, such as an Azure virtual machine or Azure App Service. |
Created as a stand-alone Azure resource. |
|
Life cycle |
Shared life cycle with the Azure resource. When the parent resource is deleted, the managed identity is also deleted. |
Independent life cycle. Must be explicitly deleted. |
|
Sharing across Azure resources |
Cannot be shared. Associated with a single Azure resource. |
Can be shared. A user-assigned managed identity can be associated with more than one Azure resource. |
|
Common use cases |
Workloads that are contained within a single Azure resource. Workloads for which you need independent identities, such as an application that runs on a single virtual machine. |
Workloads that run on multiple resources and which can share a single identity. Workloads that need pre-authorization to a secure resource as part of a provisioning flow. Workloads where resources are recycled frequently, but permissions should stay consistent. For example, a workload where multiple virtual machines need to access the same resource. |
Device
A device is a piece of hardware, such as a mobile device, laptop, server, or printer. Device identities can be set up in different ways in Azure AD, which determine properties such as who owns the device. Managing devices in Azure AD allows an organization to protect its assets by using tools such as Microsoft Intune to ensure standards for security and compliance. Azure AD also enables single sign-on to devices, apps, and services from anywhere through these devices.
There are multiple options for getting devices into Azure AD:
-
Azure AD registered devices can be Windows 10, iOS, Android, or macOS devices. Devices that are Azure AD registered are typically owned personally, rather than by the organization. They are signed in with a personal Microsoft account or another local account.
-
Azure AD joined devices exist only in the cloud. Azure AD joined devices are owned by an organization and signed in with an organization Azure AD account. Users sign in to their devices with their Azure AD or synced Active Directory work or school accounts. You can configure Azure AD joined devices for all Windows 10 devices (except Windows 10 Home).
-
Hybrid Azure AD joined devices can be Windows 7, 8.1, or 10 or Windows Server 2008 or newer. Devices that are hybrid Azure AD joined are owned by an organization and are signed in with an Active Directory Domain Services account belonging to that organization. They exist in the cloud and on-premises.
IT admins can use tools like Microsoft Intune, a mobile device management (MDM) solution, to manage devices. Refer to Microsoft Intune for more information.
Describe the types external identities
Today’s world is about collaboration, working with people both inside and outside of your organization. That means that you sometimes need to provide access to your organization’s applications or data to external users.
Azure AD External Identities is a set of capabilities that enable organizations to allow access to external users, such as customers or partners. Your customers, partners, and other guest users can “bring their own identities” to sign in.
The ability for external users to “bring their own identities” to sign in is enabled through Azure AD support of external identity providers like other Azure AD tenants, Facebook, Google, or enterprise identity providers. Admins can set up federation with identity providers so your external users can sign in with their existing social or enterprise accounts instead of creating a new account just for your application.
There are two different Azure AD External Identities: B2B or B2C.
-
B2B collaboration allows you to share your apps and resources with external users.
-
B2C is an identity management solution for consumer/customer facing apps.
B2B collaboration
B2B collaboration allows you to share your organization’s applications and services with guest users from other organizations, while maintaining control over your own data. B2B collaboration uses an invitation and redemption process, allowing external users to access your resources with their credentials. Developers can customize the invitation and redemption process using Azure AD business-to-business APIs.
With B2B collaboration, external users are managed in the same directory as employees but are typically annotated as guest users. Guest users can be managed the same way as employees, added to the same groups, and so on. With B2B, SSO to all Azure AD-connected apps is supported.
B2C access management
Azure AD B2C is a customer identity access management (CIAM) solution. Azure AD B2C allows external users to sign in with their preferred social, enterprise, or local account identities to get single sign-on to your applications. Azure AD B2C can support millions of users and billions of authentications per day. It takes care of the scaling and safety of the authentication platform, monitoring, and automatically handling threats like denial-of-service, password spray, or brute force attacks.
With Azure AD B2C, external users are managed in the Azure AD B2C directory, separately from the organization's employee and partner directory. With Azure AD B2C, SSO to customer owned apps within the Azure AD B2C tenant is supported.
Azure AD B2C is an authentication solution that you can customize with your brand so that it blends seamlessly with your web and mobile applications.

Azure AD External Identities is a feature of Premium P1 and P2 Azure AD editions, and pricing is based on Monthly Active Users. Refer to Azure AD pricing for more details.
Describe the concept of hybrid identities
Organizations may use the hybrid identity model, or the cloud only identity model. In the hybrid model, identities are created in Windows Active Directory or another identity provider, and then synchronized to Azure AD. In the cloud-only model, identities are created and wholly managed in Azure AD. Whether identities are created on-premises or in the cloud, users can access both cloud and on-premises resources.
With the hybrid model, users accessing both on-premise and cloud apps are hybrid users managed in the on-premise Active Directory. When you make an update in your on-premises AD DS, all updates to user accounts, groups, and contacts are synchronized to your Azure AD. The synchronization is managed with Azure AD Connect.

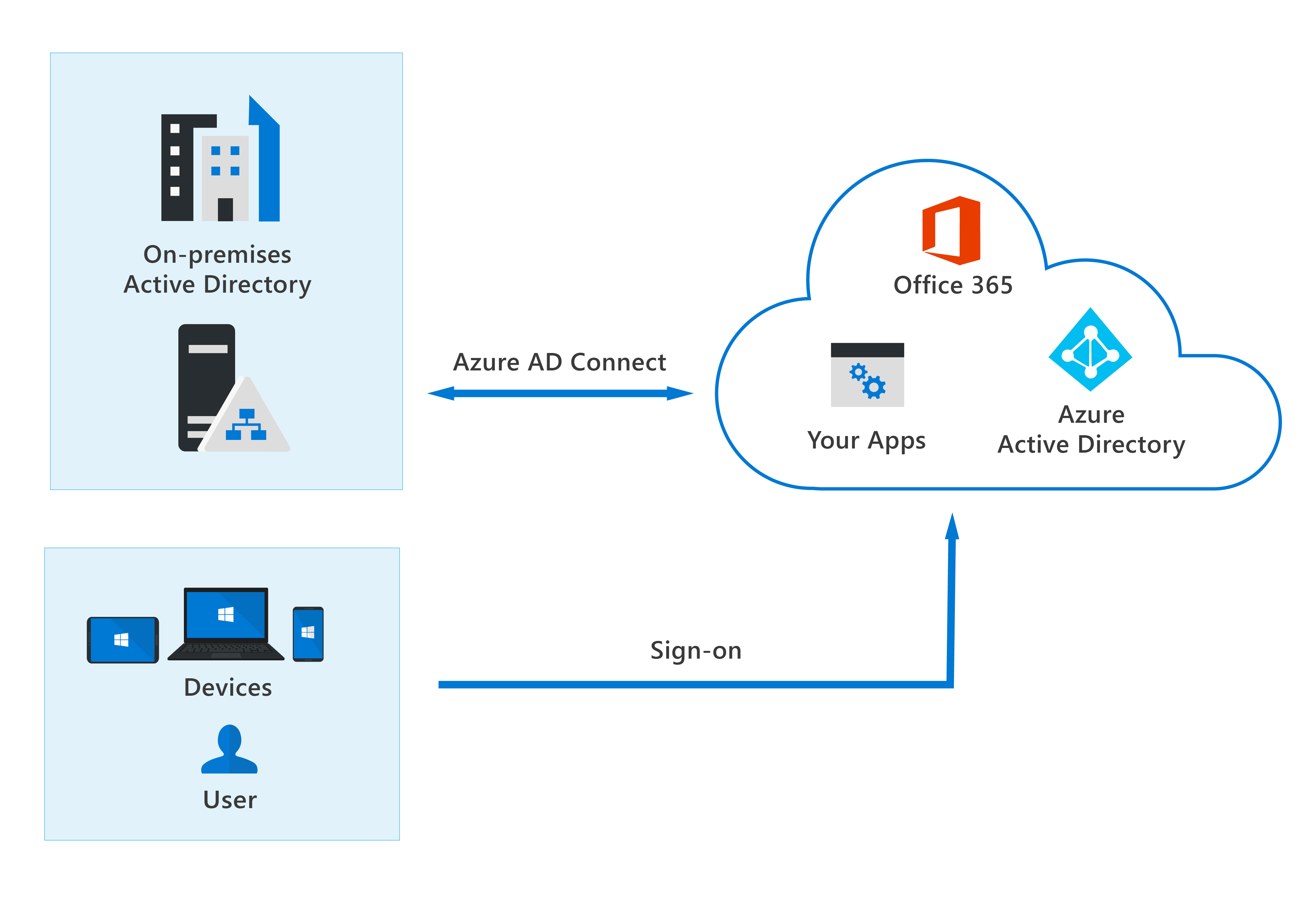
When using the hybrid model, authentication can either be done by Azure AD, which is known as managed authentication. Or Azure AD redirects the client requesting authentication to another identity provider, which is known as federated authentication.
One of three authentication methods can be used (they are listed in order of resilience):
-
Password hash synchronization. This is the simplest way to enable authentication for on-premises directory objects in Azure AD. Users can use the same username and password that they use on-premises without any additional infrastructure being needed. Password hash synchronization is a type of managed authentication.
-
Pass-through authentication (PTA). Provides a simple password validation for Azure AD authentication services by using a software agent that runs on one or more on-premises servers. The servers validate the users directly with an on-premises Active Directory, which ensures that the password validation doesn't happen in the cloud. PTA is a type of managed authentication.
-
Federated authentication. Azure AD hands off the authentication process to a separate trusted authentication system, such as on-premises Active Directory Federation Services (AD FS), to validate the user’s password.
-
Knowledge check
Multiple choice
Item 1. Your organization is launching a new app for customers. You want your customers to use a sign-in screen that is customized with your brand identity. Which type of Azure External identity authentication solution should you use?
Multiple choice
Item 2. Within your organization, all your users have Microsoft 365 cloud identities. Which identity model should you use?
Multiple choice
Item 3. You have developed an app and want users to be able to sign in with their Facebook, Google, or Twitter credentials. What type of authentication will you use?
-
Summary and resources
In this lesson, you've gained an insight into the features and capabilities of Azure Active Directory. You've learned about the different Azure AD editions, the identity types supported by Azure AD, and how you can use it to support external users. Finally, you learned about the hybrid model, where all user identities are managed in your on-premises Active Directory Domain Services (AD DS) directory, and changes are synchronized to your Azure AD.
Now that you’ve completed this lesson, you should be able to:
-
Describe what Azure AD does.
-
Describe the identity types that Azure AD supports.
Learn more
For more information on the topics covered in this lesson, see:
-