

Learning, Sharing, Creating

SPL-65 - Version 2.3.4
© 2020 Amazon Web Services, Inc. and its affiliates. All rights reserved. This work may not be reproduced or redistributed, in whole or in part, without prior written permission from Amazon Web Services, Inc. Commercial copying, lending, or selling is prohibited.
Errors or corrections? Email us at [email protected].
Other questions? Contact us at https://aws.amazon.com/contact-us/aws-training/
Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry-leading scalability, data availability, security, and performance. This means customers of all sizes and industries can use it to store and protect any amount of data for a range of use cases, such as websites, mobile applications, backup and restore, archive, enterprise applications, IoT devices, and big data analytics. Amazon S3 provides easy-to-use management features so you can organize your data and configure finely-tuned access controls to meet your specific business, organizational, and compliance requirements. Amazon S3 is designed for 99.999999999% (11 9's) of durability, and stores data for millions of applications for companies all around the world.
Visit the Amazon S3 product information page for additional details, capabilities, and a short introduction video about the service.
This lab teaches you the basics of Amazon S3 using the AWS Management Console.
When you finish the lab, you will know how to:
This will start the process of provisioning your lab resources. An estimated amount of time to provision your lab resources will be displayed. You must wait for your resources to be provisioned before continuing.
If you are prompted for a token, use the one distributed to you (or credits you have purchased).
This will automatically log you into the AWS Management Console.
Please do not change the Region unless instructed.
Error : Federated login credentials

If you see this message:
You should now be able to access the AWS Management Console.
Error: You must first log out
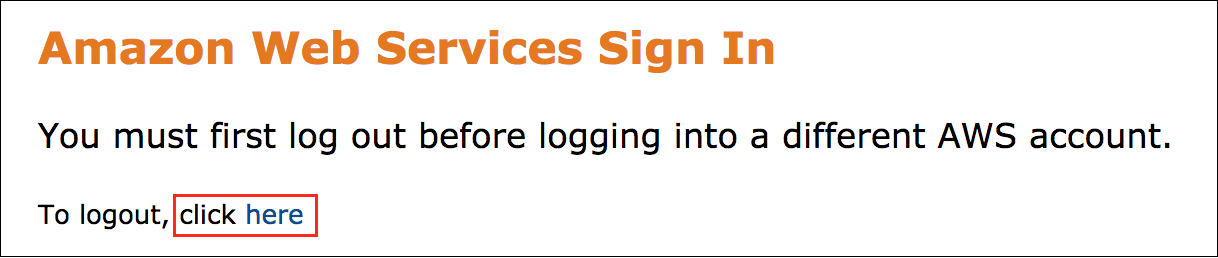
If you see the message, You must first log out before logging into a different AWS account:
Every object in Amazon S3 is stored in a bucket. In this task, you create a bucket and examine bucket configuration options.
You can also search for S3 at the top of the services menu
Bucket names must be between 3 and 63 characters long and can only contain lowercase letters, numbers, or hyphens. They must also be unique across all of Amazon S3, regardless of account or region, and cannot be changed after the bucket is created. As you enter a bucket name, a help box displays showing any violations of the naming rules. Refer to the Additional Resources section at the end of the lab for links to more information.
Selecting a particular region allows you to optimize latency, minimize costs, or address regulatory requirements. Objects stored in a region never leave that region unless you explicitly transfer them to another region.
Now that you have created a bucket, you are ready to store objects. An object can be any kind of file: a text file, a photo, a video, a zip file, and so on. When you add an object to Amazon S3, you have the option of including metadata with the object and setting permissions to control access to the object.
In this task you upload objects to your S3 bucket.
Right-click this link and download the picture to your computer: sheep.png
In the S3 Management Console, choose your bucket that starts with the name mybucket.
Choose Upload
This launches an upload wizard that assists you in uploading files. Use this wizard to upload files either by selecting them from a file chooser or by dragging them to the S3 window.
Choose Add files
Browse to and select the sheep.png file that you downloaded previously.
Choose Upload
You can watch the progress of the upload from within the Transfer panel at the bottom of the screen. Since this is a very small file, you might not see the transfer. After your file has been uploaded, it will be displayed in the bucket.
If the file does not display in the bucket within a few seconds of uploading it, you may need to choose the refresh button at the top-right.
In this task, you configure permissions on a bucket and an object to make the object publicly accessible.
First, you attempt to access the object to confirm that it is private by default.
The sheep.png overview page opens. Notice the navigation at the top-left of the screen updates with a link to return to the bucket overview page.
The link should look similar to: 
You receive an Access Denied error. This is because objects in Amazon S3 are private by default.
To resolve the access denied error, configure the object to be publicly accessible.
Keep this browser tab open, but return to the web browser tab with the S3 Management Console.
On the sheep.png overview page, choose the Permissions tab.
Under the Public access section, select Everyone. A new settings pane appears on the right-hand side of the screen.
Select Read object. Notice the warning message that displays about the object having public access.
Choose Save
An error message displays at the top of the screen because the bucket is configured not to allow public access. The bucket settings override any permissions applied to individual objects.
At the top-left of the screen, choose the link with the bucket name you created previously.
Choose the Permissions tab. The Block public access button is highlighted. If it is not, choose it.
Choose Edit to change the settings.
Deselect the Block all public access option, and then leave all other options deselected.
Notice that all of the individual options remain deselected. When deselecting all public access, you must then select the individual options that apply to your situation and security objectives. Both ACLs and bucket policies are used later in the lab, so they all remain deselected in this example. In a production environment, it is recommended to use the least permissive settings possible. Refer to the Additional Resources section at the end of the lab for links to more information.
Choose Save
A dialogue box opens asking you to confirm your changes. Type in the field, and then choose Confirm
A Public access settings updated successfully message displays.
Choose the Overview tab.
Choose the sheep.png file name.
On the sheep.png overview page, choose the Permissions tab.
Under the Public access section, select Everyone. A new settings pane appears on the right-hand side of the screen.
Select Read object. Notice the warning message that displays about the object having public access.
Choose Save
Return to the browser tab that displayed Access Denied and refresh the page.

The picture is displayed because it is now publicly accessible.
In this example, you granted read access only to a specific object. If you wish to grant access to an entire bucket, use a bucket policy.
A bucket policy is a set of permissions associated with an S3 bucket. It can be used to control access to an entire bucket or to specific directories within a bucket. In this task, you upload a new file to the bucket and verify it is not publicly accessible. You then use the AWS Policy Generator to create a bucket policy that enables public read access to all objects within the bucket.
Right-click this link and download the text file to your computer: sample-file.txt
In the S3 Management Console tab, choose the name of your bucket at the top-left of the window.
Choose Upload and use the same upload process as in the previous task to upload the sample-file.txt file you downloaded.
Choose the sample-file.txt file name. The sample-file.txt overview page opens.
Copy the Object URL link displayed at the bottom of the window.
In a new browser tab, paste the link into the address field, and then press Enter.
Once again, Access Denied will be displayed. You need to configure a bucket policy to grant access to all objects in the bucket without having to specify permissions on each object individually.
Keep this browser tab open, but return to the tab with the S3 Management Console.
Choose the name of your bucket at the top-left of the window.
You should see a list of the objects in your bucket. If not, navigate back to your bucket so that you see the list of objects you have uploaded.
Choose the Permissions tab.
In the Permissions tab, choose Bucket Policy
A blank Bucket policy editor is displayed. Bucket policies can be created manually, or they can be created with the assistance of the AWS Policy generator.
Before creating the policy, you will need to copy the ARN (Amazon Resource Name) of your bucket.
ARNs uniquely identify AWS resources across all of AWS. Each section of the ARN is separated by a ":" and represents a specific piece of the path to the specified resource. The sections can vary slightly depending on the service being referenced, but generally follows this format:
arn:partition:service:region:account-id:resource
Amazon S3 does not require region or account-id parameters in ARNs, so those sections are left blank. However, the ":" to separate the sections is still used, so it looks similar to arn:aws:s3:::mybucket45647467
Refer to the Additional Resources section at the end of the lab for links to more information.
Copy the ARN of your bucket to the clipboard. It is displayed at the top of the policy editor.
Choose the Policy generator link at the bottom of the page.
A new web browser tab will open with the AWS Policy Generator.
AWS policies use the JSON format, and are used to configure granular permissions for AWS services. While you can write the policy in JSON manually, the AWS Policy Generator allows you to create it using a friendly web interface.
Using the * with Principal means that anyone will be able to perform the actions in the policy. Refer to the Additional Resources section at the end of the lab for links to more information about AWS JSON policy elements.
The get GetObject action grants permission for objects to be retrieved from Amazon S3. Refer to the Additional Resources section at the end of the lab for links to more information about the actions available for use in Amazon S3 policies.

The ARN should look similar to: arn:aws:s3:::mybucket45647467/*
An Amazon Resource Name (ARN) is a standard way to refer to resources within AWS. In this case, the ARN is referring to your S3 bucket. Adding /* to the end of the bucket name allows the policy to apply to all objects within the bucket.
Choose Add Statement. The details of the statement you configured are added to a table below the button. You can add multiple statements to a policy.
Choose Generate Policy.
A new window is displayed showing the generated policy in JSON format. It should look similar to:
{
"Id": "Policy1557511288767",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1557511286634",
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": "arn:aws:s3:::mybucket45647467/*",
"Principal": "*"
}
]
}
Confirm that appears after your bucket name as shown in the Resource line in the sample above.
Copy the policy you created to your clipboard.
Close the web browser tab and return to the tab with the Bucket policy editor.
Paste the bucket policy you created into the Bucket policy editor.
Choose Save
You have just applied a bucket policy to your bucket. With this policy, all objects in your bucket are now publicly accessible.
Notice the warning message banner at the top of the screen that this bucket now has public access. The Bucket Policy button and Permissions tab are both marked with a Public label as well.
The page now displays text contained in the file you uploaded. This is because the bucket policy applies to the bucket as a whole, without having to grant individual permissions to each object individually.
Versioning is a means of keeping multiple variants of an object in the same bucket. You can use versioning to preserve, retrieve, and restore every version of every object stored in your Amazon S3 bucket. With versioning, you can easily recover from both unintended user actions and application failures.
In this task, you turn on versioning for the bucket, and then upload a modified version of the text file you used in the previous task.
You should be on the S3 bucket Permissions tab from the previous task. If you are not, choose the link to the bucket at the top-left of the screen to return to the bucket Overview page.
Choose the Properties tab.
Choose Versioning.
Select Enable versioning and then choose Save
You will notice the circle at the bottom-left of the Versioning box is now highlighted with a checkmark and says Enabled.
Versioning is enabled for an entire bucket and all objects within the bucket. It cannot be enabled for individual objects.
There are also cost considerations when enabling versioning. Refer to the Additional Resources section at the end of the lab for links to more information.
While this file has the same name as the previous file, it contains new text.
You should notice a new Versions HideShow button is shown above the list of objects.
Choose Upload and use the same upload process in the previous task to upload the new sample-file.txt file.
Go to the browser tab that has the contents of the sample-file.txt file.
Make a note of the contents on the page, then refresh the page.
Notice a new line of text has been added.
Amazon S3 always returns the latest version of an object if a version is not otherwise specified.
You can also obtain a list of available versions in the S3 Management Console.
Close the web browser tab with the contents of the text file.
In the S3 Management Console, choose the sample-file.txt file name. The sample-file.txt overview page opens.
Choose Latest version to the right of the object name, and then select the bottom version (which is not the latest version).
Choose Open
You should now see the first version of the file using the S3 Management Console.
However, if you try to access the older version of the sample-file.txt file using the object URL link, you will receive an access denied message. This is expected because the bucket policy you created in the previous task only allows permission to access the latest version of the object. In order to access a previous version of the object, you need to update your bucket policy to include the "s3:GetObjectVersion" permission. Below is an example bucket policy with the additional "s3:GetObjectVersion" action added that allows you to access the older version using the link. You do not need to update your bucket policy with this example.
{
"Id": "Policy1557511288767",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1557511286634",
"Action": [
"s3:GetObject",
"s3:GetObjectVersion"
],
"Effect": "Allow",
"Resource": "arn:aws:s3:::mybucket45647467/*",
"Principal": "*"
}
]
}
Choose the link for the bucket name at the top-left to return to the bucket Overview tab.
Above the list of objects, choose Show on the HideShow button next to Versions.
The view changes to show the available versions of each object, and which version is the latest. Notice the sheep.png object only has one version, and the version ID is null. This is because the object was uploaded before versioning was enabled for this bucket.
Also notice that you can now choose the version name link to navigate directly to that version of the object in the console.
Choose Hide on the HideShow button to return to the default object view.
Select the checkbox to the left of the sample-file.txt file.
With the object selected, choose the Actions button, and then choose Delete
The Delete objects window appears. Choose the Delete button.
The sample-file.txt object is no longer displayed in the bucket. However, if the object is deleted by mistake, versioning can be used to recover it.
Notice that the sample-file.txt object is displayed again, but the most recent version is a Delete marker. The two previous versions are listed as well. If versioning has been enabled on the bucket, objects are not immediately deleted. Instead, Amazon S3 inserts a delete marker, which becomes the current object version. The previous versions of the object are not removed. Refer to the Additional Resources section at the end of the lab for links to more information about versioning.
Select the checkbox to the left of the version of the sample-file.txt object with (Delete marker)
With the object selected, choose the Actions button, and then choose Delete
The Delete objects window appears. Choose the Delete button.
Choose Hide on the HideShow button.
Notice that the sample-file.txt object has been restored to the bucket. Removing the delete marker has effectively restored the object to its previous state. Refer to the Additional Resources section at the end of the lab for links to more information about undeleting S3 objects.
You can also delete a specific version of an object.
You should see two versions of the sample.txt object.
Select the checkbox to the left of the latest version of the sample-file.txt object.
With the object selected, choose the Actions button, and then choose Delete
The Delete objects window appears. Choose the Delete button.
Notice that there is now only one version of the sample-file.txt file. When deleting a specific version of an object no delete marker is created. The object is permanently deleted. Refer to the Additional Resources section at the end of the lab for links to more information about deleting object versions in Amazon S3.
Choose Hide on the HideShow button.
Choose the sample-file.txt file name. The sample-file.txt overview page opens.
Copy the Object URL link displayed at the bottom of the window.
In a new browser tab, paste the link into the address field, and then press Enter.
The text of the original version of the sample-file.txt object is displayed.
Congratulations! You have successfully learned how to:
Follow these steps to close the console, end your lab, and evaluate the experience.
Return to the AWS Management Console.
On the navigation bar, click awsstudent@<AccountNumber>, and then click Sign Out.
Click End Lab
Click OK
(Optional):
Click Submit
You may close the dialog if you don't want to provide feedback.
For more information about AWS Training and Certification, see http://aws.amazon.com/training/ .
For more AWS Self-Paced Labs, see http://amazon.qwiklabs.com .
For feedback, suggestions, or corrections, please email us at [email protected].
Here's another lab we think you'll like.