FortiGate is a next-generation firewall (NGFW) that delivers industry-leading enterprise security with full visibility and threat protection.
Using FortiGate, organizations can achieve:
- Ultra-fast security throughout their network
- A consistent real-time defense
- An excellent user experience
- Operational efficiency and automated workflows
Note: training course – https://training.fortinet.com/course/view.php?id=39326
1. FortiGate Overview
2. Configuring Interfaces and Routing
3. Firewall Policies
4. Authenticating Network Users
5. Inspect SSL Traffic
6. Blocking Malware
7. Control Web Access Using Web Filtering
8. Configuring the FortiGate Intrusion Prevention System
9. Controlling Application Access
10. Creating IPsec Virtual Private Networks
11. Configuring FortiGate SSL VPN
12. FortiGate System Maintenance and Monitoring
13. Configuring the Fortinet Security Fabric
FortiGate Overview
FortiGate Platform Structure

Models

Configuring Interfaces and Routing
LAN – DHCP
WAN
Default Route, static route
Includes:
- Destination
- Gateway address
- Interface
Verify the route from Dashboard – Network – Static & Dynamic Routing widget – Click to expand
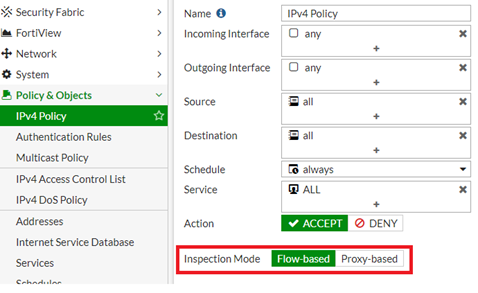
Policies
By default, the inspection mode of the new firewall policy is set to Flow Based.
Flow-based inspection

Proxy-based insepction

Change Inspection Mode:
From the CLI.
Use the below command to change the inspection mode:
config firewall policy
edit # (ID of the policy)
set inspection-mode <flow or proxy>
end
Internet Access Policy Rule example:

Show Matching logs

Firewall Authentication

Local Password Auth
Remote Password Authentication
Steps:
- Create a user account
- Configure Remote auth
- Create a user group
- add authenication to a firewall policy
- verify and monitor firewall authentication


Inspect SSL Traffic
Two types of FortiGate SSL Inspection:
– Certificate Inspection (always with Web Filtering)
– Deep Inspection (Full Inspection)


Deep Inspection:


Certificate Warning:

Solve this certificate warning issue:

Create/Edit SSL Inspection Profiles

Apply custom deep ssl inspection into a firewall rule. You will need to enable one Security profiles first , such as Antivirus as shown in the following screenshot:

To avoid certificate security warning, we can install Fortigate CA certificate from ssl inspection profile.
Exempt some websites from SSL inspection.
Blocking Malware
Antivirus Scan
Grayware Scan
Machine Learning / Artificial Intelligence Scan


verification configuration from www.eicar.com
Control Web Acess Using Web Filtering

Actions
- Allow
- Block
- Monitor
- Warning
- Authenticate
Fortiguard.com/webfilter

Authenticate

Configuring IPS (Intrusion Prevention System)
Controlling Applications Access
References
- Fortinet Training – https://training.fortinet.com/my/