After you onboard Microsoft Sentinel into your workspace, use data connectors to start ingesting your data into Microsoft Sentinel. Microsoft Sentinel comes with many out of the box connectors for Microsoft services, which integrate in real time. For example, the Microsoft Defender XDR connector is a service-to-service connector that integrates data from Office 365, Microsoft Entra ID, Microsoft Defender for Identity, and Microsoft Defender for Cloud Apps.
Built-in connectors enable connection to the broader security ecosystem for non-Microsoft products. For example, use Syslog, Common Event Format (CEF), or REST APIs to connect your data sources with Microsoft Sentinel.
Microsoft Sentinel solutions provide packaged security content, including data connectors, workbooks, analytics rules, playbooks, and more. When you deploy a solution with a data connector, you get the data connector together with related content in the same deployment.
Architecture
Overall Architecture:
Syslog and CEF via Legacy Log Analytics Agent (Deprecate in 2024)
Rules:
- If any log contains CEF, the log will be forwarded to tcp localhost:25226.
- For other default syslog, standard rule will be apply, which is based on Facility and Severity, then will be be sent to udp localhost:25224.
- Log analytics agent will encrypt those logs then sent them up to Sentinel.
Syslog and CEF via AMA
- AMA can be on every linux host
- Or can use for syslog forwarding, which is to use a single linux host for forwarding syslog from other linux or syslog sources.
Windows Events via AMA
Two ways:
- Agent on every Windows host
- Use a Single Windows Event Collector (WEC) with the agent installed. Doesn’t require agent on all hosts.
Azure Arc – Add On-Prem Machine
Add a server with Azure Arc
Download or Copy / Paste the code into Linux or Windows machine to run.
It will download the installation package, then install the downloaded hybrid agent, eventually run the connect command to connect to ARC portal.
try {
$env:SUBSCRIPTION_ID = “d9fzzzz-zzz-zz-zzzz-zzzzzb9”;
$env:RESOURCE_GROUP = “RG-SERVERS”;
$env:TENANT_ID = “adfd-dfdfd-dfdfd-dfdfd-dfdfdf”;
$env:LOCATION = “eastus”;
$env:AUTH_TYPE = “token”;
$env:CORRELATION_ID = “yyy980-dfd-ad–fdsafd-fd-fdf-dfdfd”;
$env:CLOUD = “AzureCloud”;
[Net.ServicePointManager]::SecurityProtocol = [Net.ServicePointManager]::SecurityProtocol -bor 3072;
# Download the installation package
Invoke-WebRequest -UseBasicParsing -Uri “https://aka.ms/azcmagent-windows” -TimeoutSec 30 -OutFile “$env:TEMP\install_windows_azcmagent.ps1”;
# Install the hybrid agent
& “$env:TEMP\install_windows_azcmagent.ps1”;
if ($LASTEXITCODE -ne 0) { exit 1; }
# Run connect command
& “$env:ProgramW6432\AzureConnectedMachineAgent\azcmagent.exe” connect –resource-group “$env:RESOURCE_GROUP” –tenant-id “$env:TENANT_ID” –location “$env:LOCATION” –subscription-id “$env:SUBSCRIPTION_ID” –cloud “$env:CLOUD” –correlation-id “$env:CORRELATION_ID”;
}
catch {
$logBody = @{subscriptionId=”$env:SUBSCRIPTION_ID”;resourceGroup=”$env:RESOURCE_GROUP”;tenantId=”$env:TENANT_ID”;location=”$env:LOCATION”;correlationId=”$env:CORRELATION_ID”;authType=”$env:AUTH_TYPE”;operation=”onboarding”;messageType=$_.FullyQualifiedErrorId;message=”$_”;};
Invoke-WebRequest -UseBasicParsing -Uri “https://gbl.his.arc.azure.com/log” -Method “PUT” -Body ($logBody | ConvertTo-Json) | out-null;
Write-Host -ForegroundColor red $_.Exception;
}
Install Extenstion (AMA)
Edit Windows Security Events via AMA connector, add Data Collection Rule for your resources:
Linux Syslog
Configure / Deploy Linux Syslog Forwarder
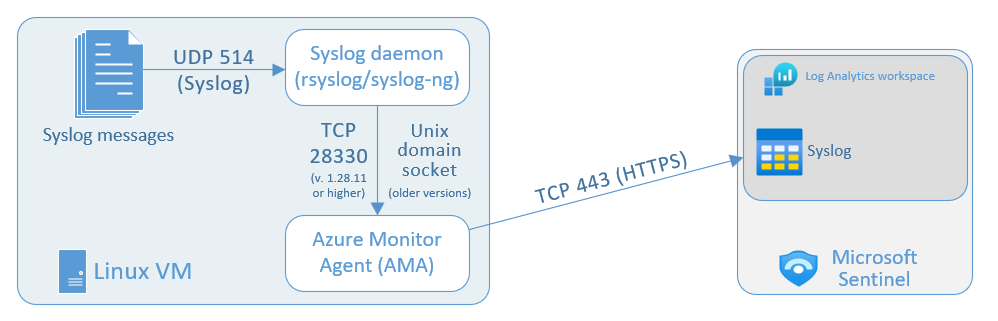
To ingest Syslog and CEF logs into Microsoft Sentinel, particularly from devices and appliances onto which you can’t install the Log Analytics agent directly, you’ll need to designate and configure a Linux machine that will collect the logs from your devices and forward them to your Microsoft Sentinel workspace. This machine can be a physical or virtual machine in your on-premises environment, an Azure VM, or a VM in another cloud.
This machine has two components that take part in this process:
- A syslog daemon, either rsyslog or syslog-ng, that collects the logs.
- The Log Analytics Agent (also known as the OMS Agent), that forwards the logs to Microsoft Sentinel.
Using the link provided below, you will run a script on the designated machine that performs the following tasks:
-
Installs the Log Analytics agent for Linux (also known as the OMS agent) and configures it for the following purposes:
- listening for CEF messages from the built-in Linux Syslog daemon on TCP port 25226
- sending the messages securely over TLS to your Microsoft Sentinel workspace, where they are parsed and enriched
-
Configures the built-in Linux Syslog daemon (rsyslog.d/syslog-ng) for the following purposes:
- listening for Syslog messages from your security solutions on TCP port 514
- forwarding only the messages it identifies as CEF to the Log Analytics agent on localhost using TCP port 25226
Pre-requisites
Each data connector has its own set of prerequisites. Prerequisites might include that you must have specific permissions on your Azure workspace, subscription, or policy. Or, you must meet other requirements for the partner data source you’re connecting to.
Prerequisites for each data connector are listed on the relevant data connector page in Microsoft Sentinel.
Install the product solution from the Content Hub in Microsoft Sentinel. If the product isn’t listed, install the solution for Common Event Format.
Note
- A single log forwarder machine with the above hardware configuration and using the rsyslog daemon has a supported capacity of up to 8500 events per second (EPS) collected.
Change Ubuntu Ip from DHCP to Static
nmcli conn modify "System eth0" ipv4.ignore-auto-dns yes nmcli conn modify "System eth0" ipv4.dns "192.168.24.7 8.8.8.8" systemctl restart NetworkManager |
Add a super user in:
Check Rsyslog service:
AMA agent
Configure AMA listen on different ports for different log sources
root@NETSEC-syslog:/etc/rsyslog.d# cat 05-filterlogs.conf
# Forward vCenter Logs to OMS
if ($inputname == 'udp_vcenter' or $inputname == 'tcp_vcenter') then @@127.0.0.1:23033;vcenter
& stop
# Forward Meraki Logs to OMS
if ($inputname == 'udp_meraki' or $inputname == 'tcp_meraki') then @@127.0.0.1:22033;meraki
& stop
- rsyslogd -v
- systemctl status rsyslog
- systemctl start rsyslog
- vi /etc/rsyslog.conf
root@NETSEC-syslog:~# cat /etc/rsyslog.conf
# /etc/rsyslog.conf configuration file for rsyslog
#
# For more information install rsyslog-doc and see
# /usr/share/doc/rsyslog-doc/html/configuration/index.html
#
# Default logging rules can be found in /etc/rsyslog.d/50-default.conf
#################
#### MODULES ####
#################
module(load=”imuxsock”) # provides support for local system logging
#module(load=”immark”) # provides –MARK– message capability
# provides UDP syslog reception
module(load=”imudp”)
input(type=”imudp” port=”514″)
# provides TCP syslog reception
module(load=”imtcp”)
input(type=”imtcp” port=”514″)
input(type=”imudp” port=”1514″ name=”udp_meraki”)
input(type=”imudp” port=”2514″ name=”udp_vcenter”)
input(type=”imtcp” port=”1514″ name=”tcp_meraki”)
input(type=”imtcp” port=”2514″ name=”tcp_vcenter”)
$template meraki,”%timestamp% %hostname% %msg%”
$template vcenter,”%timestamp% %hostname% %msg%”
# provides kernel logging support and enable non-kernel klog messages
module(load=”imklog” permitnonkernelfacility=”on”)
###########################
#### GLOBAL DIRECTIVES ####
###########################
#
# Use traditional timestamp format.
# To enable high precision timestamps, comment out the following line.
#
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# Filter duplicated messages
$RepeatedMsgReduction on
#
# Set the default permissions for all log files.
#
$FileOwner syslog
$FileGroup adm
$FileCreateMode 0640
$DirCreateMode 0755
$Umask 0022
$PrivDropToUser syslog
$PrivDropToGroup syslog
#
# Where to place spool and state files
#
$WorkDirectory /var/spool/rsyslog
#
# Include all config files in /etc/rsyslog.d/
#
$IncludeConfig /etc/rsyslog.d/*.conf
root@NETSEC-syslog:~#
Meraki and Citrix vCenter
root@NSTEST-syslog:~# wget https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh && sh onboard_agent.sh -w fe23134c-431b-4d69-8b3e-138943bb757f -s l6Ls25g1rIskJXIeTyoMi2LfMhlm3BeoSUljmHzb86QbrBOCBYfVwEysnccbDORA0Nq3eKXEK5fLgeqQ5EVaKg== -d opinsights.azure.com
–2024-03-25 15:30:17– https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)… 185.199.111.133, 185.199.108.133, 185.199.109.133, …
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 3848 (3.8K) [text/plain]
Saving to: ‘onboard_agent.sh’
onboard_agent.sh 100%[===================>] 3.76K –.-KB/s in 0s
2024-03-25 15:30:17 (95.9 MB/s) – ‘onboard_agent.sh’ saved [3848/3848]
–2024-03-25 15:30:17– https://github.com/microsoft/OMS-Agent-for-Linux/releases/download/OMSAgent_v1.19.0-0/omsagent-1.19.0-0.universal.x64.sh
Resolving github.com (github.com)… 140.82.114.3
Connecting to github.com (github.com)|140.82.114.3|:443… connected.
HTTP request sent, awaiting response… 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/43709699/86dbf012-12fc-49da-b79e-3301ce03d004?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAVCODYLSA53PQK4ZA%2F20240325%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240325T153018Z&X-Amz-Expires=300&X-Amz-Signature=2a97a2aa8938b47de1e179bd20a74fe323ff6183397ca581374aa863182ebfcf&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=43709699&response-content-disposition=attachment%3B%20filename%3Domsagent-1.19.0-0.universal.x64.sh&response-content-type=application%2Foctet-stream [following]
–2024-03-25 15:30:18– https://objects.githubusercontent.com/github-production-release-asset-2e65be/43709699/86dbf012-12fc-49da-b79e-3301ce03d004?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAVCODYLSA53PQK4ZA%2F20240325%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240325T153018Z&X-Amz-Expires=300&X-Amz-Signature=2a97a2aa8938b47de1e179bd20a74fe323ff6183397ca581374aa863182ebfcf&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=43709699&response-content-disposition=attachment%3B%20filename%3Domsagent-1.19.0-0.universal.x64.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)… 185.199.110.133, 185.199.111.133, 185.199.108.133, …
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.110.133|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 250004251 (238M) [application/octet-stream]
Saving to: ‘omsagent-1.19.0-0.universal.x64.sh’
omsagent-1.19.0-0.u 100%[===================>] 238.42M 104MB/s in 2.3s
2024-03-25 15:30:20 (104 MB/s) – ‘omsagent-1.19.0-0.universal.x64.sh’ saved [250004251/250004251]
Extracting OMS agent install bundle…
—– Upgrading package omi to version (omi-1.8.1-0.ulinux.s.x64) —–
Detected OpenSSL version 3.0.2 set as system default.
Install/Upgrade will use package(s) from OMS bundle installer’s 300 openssl directtory.
Selecting previously unselected package omi.
(Reading database … 74617 files and directories currently installed.)
Preparing to unpack …/omi-1.8.1-0.ulinux.s.x64.deb …
Creating omiusers group …
Creating omi group …
Creating omi service account …
Unpacking omi (1.8.1.0) …
Setting up omi (1.8.1.0) …
…….+…..+…+.+…+……+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*…+..+…+………+…+.+………..+…+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*………+….+……+…+..+……+…….+……..+…….+..+………+…………+………+………+….+…+……………+…+…………..+……+….+…+..+……+.+……………+……..+.+……+…+..+……+….+…+..+……+……….+…..+…….+……………+…..+.+…..+.+…..+……………….+…..+……+………….+…+…+…………+..+…+…….+..+…+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
..+..+………….+…..+…+.+………………+……+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*….+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+…+…..+………………….+..+.+………+…..+…+…+.+…+..+….+…………+…+..+….+…+..+…+…+…+.+……+..+.+………+..+….+…………+…+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
—–
2024-03-25 15:30:22 : Crontab not configured to update omi keytab automatically. Skip unconfigure
ktutil not found
Checking if cron is installed…
Checking if cron/crond service is started…
Set up a cron job to OMI logrotate every 15 minutes
Configuring OMI service …
Created symlink /etc/systemd/system/multi-user.target.wants/omid.service → /lib/systemd/system/omid.service.
Trying to start omi with systemctl
omi is started.
Trying to stop omi with systemctl
omi is stopped.
Trying to start omi with systemctl
omi is started.
—– Upgrading package scx to version (scx-1.8.1-0.universal.s.x64) —–
Detected OpenSSL version 3.0.2 set as system default.
Install/Upgrade will use package(s) from OMS bundle installer’s 300 openssl directtory.
Selecting previously unselected package scx.
(Reading database … 74680 files and directories currently installed.)
Preparing to unpack …/scx-1.8.1-0.universal.s.x64.deb …
Unpacking scx (1.8.1.0) …
Setting up scx (1.8.1.0) …
Generating certificate with hostname=”NSTEST-syslog”
Trying to stop omi with systemctl
omi is stopped.
Trying to start omi with systemctl
omi is started.
—– Upgrading package omsagent to version (omsagent-1.19.0-0.universal.x64) —–
Detected OpenSSL version 3.0.2 set as system default.
Install/Upgrade will use package(s) from OMS bundle installer’s 300 openssl directtory.
Selecting previously unselected package omsagent.
(Reading database … 74725 files and directories currently installed.)
Preparing to unpack …/omsagent-1.19.0-0.universal.x64.deb …
Creating omsagent group …
Creating omsagent service account …
Creating nxautomation group …
Creating nxautomation service account …
Unpacking omsagent (1.19.0.0) …
Setting up omsagent (1.19.0.0) …
-e info Reading onboarding params from: /etc/omsagent-onboard.conf
Workspace 000000-1111-222222222-3333333333 already onboarded and agent is running.
Symbolic links have not been created; re-onboarding to create them
info Generating certificate …
-e info Agent GUID is 8a69e647-7047-434f-b3ad-79707c5945c4
-e info Onboarding success
Configure syslog…
Configuring rsyslog for OMS logging
Restarting service: rsyslog
Configure heartbeat monitoring agent…
Configure log rotate for workspace 000000-1111-222222222-3333333333…
INFO: Configuring OMS agent service 000000-1111-222222222-3333333333 …
-e error MetaConfig generation script not available at /opt/microsoft/omsconfig/Scripts/python3/OMS_MetaConfigHelper.py. For more details check logs in /var/opt/microsoft/omsconfig/omsconfig.log
Trying to stop omi with systemctl
omi is stopped.
Trying to start omi with systemctl
omi is started.
Configure log rotate for workspace 000000-1111-222222222-3333333333…
Applying Syslog conf hotfix…
Removing omsconfig package as part of upgrade
—– Removing package: omsconfig —–
dpkg: warning: ignoring request to remove omsconfig which isn’t installed
—– Upgrading package omsconfig to version (omsconfig-1.3.0-0.x64) —–
Detected OpenSSL version 3.0.2 set as system default.
Install/Upgrade will use package(s) from OMS bundle installer’s 300 openssl directtory.
Selecting previously unselected package omsconfig.
(Reading database … 84211 files and directories currently installed.)
Preparing to unpack 300/omsconfig-1.3.0-0.x64.deb …
Using python3
Cleanning up existing dsc_hosts…
chmod: cannot access ‘/opt/dsc’: No such file or directory
Deployment operation type : install
Cleanning directory /opt/dsc…
Cleaned up existing dsc_hosts…
Unpacking omsconfig (1.3.0.0) …
Setting up omsconfig (1.3.0.0) …
Using python3
Running python3, python version is , python3
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nx_1.5.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxGroupResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxGroupResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxGroupResource/libMSFT_nxGroupResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxGroupResource.reg to 0o644
VERBOSE from InstallModule.py: Installing resource MSFT_nxAvailableUpdatesResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxAvailableUpdatesResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxAvailableUpdatesResource/libMSFT_nxAvailableUpdatesResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxAvailableUpdatesResource.reg to 0o644
VERBOSE from InstallModule.py: Installing resource MSFT_nxPackageResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxPackageResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxPackageResource/libMSFT_nxPackageResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxPackageResource.reg to 0o644
VERBOSE from InstallModule.py: Installing resource MSFT_nxUserResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxUserResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxUserResource/libMSFT_nxUserResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxUserResource.reg to 0o644
VERBOSE from InstallModule.py: Installing resource MSFT_nxServiceResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxServiceResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxServiceResource/libMSFT_nxServiceResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxServiceResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxOMSPerfCounter_2.3.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxOMSPerfCounterResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxOMSPerfCounterResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxOMSPerfCounterResource/libMSFT_nxOMSPerfCounterResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxOMSPerfCounterResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxOMSSyslog_2.5.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxOMSSyslogResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxOMSSyslogResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxOMSSyslogResource/libMSFT_nxOMSSyslogResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxOMSSyslogResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxOMSSudoCustomLog_2.8.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxOMSSudoCustomLogResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxOMSSudoCustomLogResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxOMSSudoCustomLogResource/libMSFT_nxOMSSudoCustomLogResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxOMSSudoCustomLogResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxOMSKeyMgmt_1.0.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxOMSKeyMgmtResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxOMSKeyMgmtResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxOMSKeyMgmtResource/libMSFT_nxOMSKeyMgmtResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxOMSKeyMgmtResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxFileInventory_1.4.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxFileInventoryResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxFileInventoryResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxFileInventoryResource/libMSFT_nxFileInventoryResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxFileInventoryResource.reg to 0o644
The result code is 0
VERBOSE from InstallModule.py: Extracting module zip file from /opt/microsoft/omsconfig/module_packages/nxOMSGenerateInventoryMof_1.5.zip to /opt/microsoft/omsconfig/modules
VERBOSE from InstallModule.py: Installing resource MSFT_nxOMSGenerateInventoryMofResource
VERBOSE from InstallModule.py: Updated permissions of file: /opt/omi/lib/libMSFT_nxOMSGenerateInventoryMofResource_root-oms.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /opt/dsc/lib/MSFT_nxOMSGenerateInventoryMofResource/libMSFT_nxOMSGenerateInventoryMofResource.so to 0o644
VERBOSE from InstallModule.py: Updated permissions of file: /etc/opt/omi/conf/omiregister/root-oms/MSFT_nxOMSGenerateInventoryMofResource.reg to 0o644
The result code is 0
gpg: keybox ‘/etc/opt/omi/conf/omsconfig/keymgmtring.gpg’ created
gpg: directory ‘/etc/opt/omi/conf/omsconfig/.gnupg’ created
gpg: /etc/opt/omi/conf/omsconfig/.gnupg/trustdb.gpg: trustdb created
gpg: key C4EC49E544BC4178: public key “Microsoft (Release Signing) <[email protected]>” imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: keybox ‘/etc/opt/omi/conf/omsconfig/keyring.gpg’ created
gpg: key 20541A3DDE321294: public key “Microsoft (Release Signing) <[email protected]>” imported
gpg: Total number processed: 1
gpg: imported: 1
Reset ownership of files defined in /etc/sudoers.d/omsagent
Trying to stop omi with systemctl
omi is stopped.
Trying to start omi with systemctl
omi is started.
Using python3
Running python3
VERBOSE from OMS_MetaConfigHelper.py: OMS config path being read: /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/conf/omsadmin.conf
VERBOSE from OMS_MetaConfigHelper.py: Output from3: /opt/microsoft/omsconfig/Scripts/python3/SetDscLocalConfigurationManager.py -configurationmof /etc/opt/omi/conf/omsconfig/generated_meta_config.mof: Opened the dsc host lock file at the path ‘/opt/dsc/dsc_host_lock’
[2024/03/25 15:30:28] [11122] [INFO] [0] [/opt/microsoft/omsconfig/Scripts/python3/SetDscLocalConfigurationManager.py:0] dsc_host lock file is acquired by : SendMetaConfigurationApply
Operation SendMetaConfigurationApply completed successfully.
Operation was successful.
Operation SendMetaConfigurationApply completed successfully.
Operation was successful.
VERBOSE from OMS_MetaConfigHelper.py: Successfully configured omsconfig.
Applying DSC nxOMSSyslog hotfix…
Trying to stop omi with systemctl
omi is stopped.
Trying to start omi with systemctl
omi is started.
—– Updating bundled provider packages —–
Checking if Apache is installed …
Apache not found, will not install
Checking if Docker is installed…
Docker not found. Docker agent will not be installed.
Checking if MySQL is installed …
MySQL not found, will not install
Extracting…
Updating auoms …
—– Updating package: auoms (auoms-2.5.2-52.universal.x64) —–
Selecting previously unselected package auoms.
(Reading database … 84316 files and directories currently installed.)
Preparing to unpack auoms-2.5.2-52.universal.x64.deb …
Unpacking auoms (2.5.2.52) …
Setting up auoms (2.5.2.52) …
OMS Troubleshooter is installed.
You can run the Troubleshooter with the following command:
$ sudo /opt/microsoft/omsagent/bin/troubleshooter
OMS agent shell bundle exiting with status code 0
-e The Log Analytics agent is on a deprecation path and won’t be supported after August 31, 2024. If you use the Log Analytics agent to ingest data to Azure Monitor, make sure to migrate to the new Azure Monitor agent (https://docs.microsoft.com/en-us/azure/azure-monitor/agents/azure-monitor-agent-migration) prior to that date.
Other commands:
- apt
install python2 - sudo su omsagent -c ‘python2 /opt/microsoft/omsconfig/Scripts/OMS_MetaConfigHelper.py –disable’
root@NSTEST-syslog:~# cat /etc/rsyslog.d/95-omsagent.conf
# OMS Syslog collection for workspace 000000-1111-222222222-3333333333
root@NSTEST-syslog:~# netstat
Active Internet connections (w/o servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 240 NSTEST-syslog.communit:ssh ECOR-ITLT-17.comm:64202 ESTABLISHED
tcp 0 0 NSTEST-syslog.commun:56794 40.71.12.254:https TIME_WAIT
Active UNIX domain sockets (w/o servers)
Proto RefCnt Flags Type State I-Node Path
unix 2 [ ] DGRAM 646443 /run/user/1000/systemd/notify
unix 3 [ ] DGRAM CONNECTED 19355 /run/systemd/notify
root@NSTEST-syslog:~# sudo netstat -tulnp | grep ruby
udp 0 0 127.0.0.1:25224 0.0.0.0:* 10643/ruby
root@NSTEST-syslog:~# wget -v https://aka.ms/sentinel-ciscomerakioms-conf -O meraki.conf
–2024-03-25 15:35:24– https://aka.ms/sentinel-ciscomerakioms-conf
Resolving aka.ms (aka.ms)… 23.46.202.180
Connecting to aka.ms (aka.ms)|23.46.202.180|:443… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Solutions/CiscoMeraki/Data%20Connectors/la_agent_configs/meraki.conf [following]
–2024-03-25 15:35:25– https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Solutions/CiscoMeraki/Data%20Connectors/la_agent_configs/meraki.conf
Resolving raw.githubusercontent.com (raw.githubusercontent.com)… 185.199.108.133, 185.199.111.133, 185.199.109.133, …
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 688 [text/plain]
Saving to: ‘meraki.conf’
meraki.conf 100%[========================================================================================================================================>] 688 –.-KB/s in 0s
2024-03-25 15:35:25 (93.0 MB/s) – ‘meraki.conf’ saved [688/688]
root@NSTEST-syslog:~# ls
meraki.conf omsagent-1.19.0-0.universal.x64.sh onboard_agent.sh snap
root@NSTEST-syslog:~# vi meraki.conf
root@NSTEST-syslog:~# cat meraki.conf
<source>
type tcp
format none
port 22033
bind 0.0.0.0
delimiter “\n”
tag oms.api.meraki
</source>
<match oms.api.meraki>
type out_oms_api
log_level info
num_threads 5
omsadmin_conf_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/conf/omsadmin.conf
cert_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/certs/oms.crt
key_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/certs/oms.key
buffer_chunk_limit 10m
buffer_type file
buffer_path /var/opt/microsoft/omsagent/000000-1111-222222222-3333333333/state/out_oms_api_meraki*.buffer
buffer_queue_limit 10
buffer_queue_full_action drop_oldest_chunk
flush_interval 30s
retry_limit 10
retry_wait 30s
max_retry_wait 9m
</match>
root@NSTEST-syslog:~# sudo wget -v https://aka.ms/sentinel-vcenteroms-conf -O vcenter.conf
–2024-03-25 15:37:29– https://aka.ms/sentinel-vcenteroms-conf
Resolving aka.ms (aka.ms)… 23.197.182.37
Connecting to aka.ms (aka.ms)|23.197.182.37|:443… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Solutions/VMware%20vCenter/Data%20Connectors/la_agent_configs/vcenter.conf [following]
–2024-03-25 15:37:29– https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Solutions/VMware%20vCenter/Data%20Connectors/la_agent_configs/vcenter.conf
Resolving raw.githubusercontent.com (raw.githubusercontent.com)… 185.199.108.133, 185.199.110.133, 185.199.111.133, …
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 690 [text/plain]
Saving to: ‘vcenter.conf’
vcenter.conf 100%[========================================================================================================================================>] 690 –.-KB/s in 0s
2024-03-25 15:37:30 (82.8 MB/s) – ‘vcenter.conf’ saved [690/690]
root@NSTEST-syslog:~# ls
meraki.conf omsagent-1.19.0-0.universal.x64.sh onboard_agent.sh snap vcenter.conf
root@NSTEST-syslog:~# vi vcenter.conf
root@NSTEST-syslog:~# cat vcenter.conf
<source>
type tcp
format none
port 23033
bind 0.0.0.0
delimiter “\n”
tag oms.api.vcenter
</source>
<match oms.api.vcenter>
type out_oms_api
log_level info
num_threads 5
omsadmin_conf_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/conf/omsadmin.conf
cert_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/certs/oms.crt
key_path /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/certs/oms.key
buffer_chunk_limit 10m
buffer_type file
buffer_path /var/opt/microsoft/omsagent/000000-1111-222222222-3333333333/state/out_oms_api_vcenter*.buffer
buffer_queue_limit 10
buffer_queue_full_action drop_oldest_chunk
flush_interval 30s
retry_limit 10
retry_wait 30s
max_retry_wait 9m
</match>
root@NSTEST-syslog:~# sudo cp *.conf /etc/opt/microsoft/omsagent/000000-1111-222222222-3333333333/conf/omsagent.d/
root@NSTEST-syslog:~# sudo /opt/microsoft/omsagent/bin/service_control restart
3 Change rsyslog conf file
root@NSTEST-syslog:~# sudo netstat -tulnp | grep ruby
tcp 0 0 0.0.0.0:22033 0.0.0.0:* LISTEN 12080/ruby
tcp 0 0 0.0.0.0:23033 0.0.0.0:* LISTEN 12080/ruby
udp 0 0 127.0.0.1:25224 0.0.0.0:* 12080/ruby
root@NSTEST-syslog:~# vi /etc/rsyslog.conf
root@NSTEST-syslog:~# vi /etc/rsyslog.conf
root@NSTEST-syslog:~# cat /etc/rsyslog.conf
# /etc/rsyslog.conf configuration file for rsyslog
#
# For more information install rsyslog-doc and see
# /usr/share/doc/rsyslog-doc/html/configuration/index.html
#
# Default logging rules can be found in /etc/rsyslog.d/50-default.conf
#################
#### MODULES ####
#################
module(load=”imuxsock”) # provides support for local system logging
#module(load=”immark”) # provides –MARK– message capability
# provides UDP syslog reception
module(load=”imudp”)
input(type=”imudp” port=”514″)
# provides TCP syslog reception
module(load=”imtcp”)
input(type=”imtcp” port=”514″)
input(type=”imudp” port=”1514″ name=”udp_meraki”)
input(type=”imudp” port=”2514″ name=”udp_vcenter”)
input(type=”imtcp” port=”1514″ name=”tcp_meraki”)
input(type=”imtcp” port=”2514″ name=”tcp_vcenter”)
$template meraki,”%timestamp% %hostname% %msg%”
$template vcenter,”%timestamp% %hostname% %msg%”
# provides kernel logging support and enable non-kernel klog messages
module(load=”imklog” permitnonkernelfacility=”on”)
###########################
#### GLOBAL DIRECTIVES ####
###########################
#
# Use traditional timestamp format.
# To enable high precision timestamps, comment out the following line.
#
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# Filter duplicated messages
$RepeatedMsgReduction on
#
# Set the default permissions for all log files.
#
$FileOwner syslog
$FileGroup adm
$FileCreateMode 0640
$DirCreateMode 0755
$Umask 0022
$PrivDropToUser syslog
$PrivDropToGroup syslog
#
# Where to place spool and state files
#
$WorkDirectory /var/spool/rsyslog
#
# Include all config files in /etc/rsyslog.d/
#
$IncludeConfig /etc/rsyslog.d/*.conf
root@NSTEST-syslog:~# cd /etc/rsyslog.d/
root@NSTEST-syslog:/etc/rsyslog.d# ls
20-ufw.conf 21-cloudinit.conf 50-default.conf 95-omsagent.conf
root@NSTEST-syslog:/etc/rsyslog.d# vi 10-vcenter.conf
root@NSTEST-syslog:/etc/rsyslog.d# cat 10-vcenter.conf
#vCenter Logs
if ($inputname == ‘udp_vcenter’ or $inputname == ‘tcp_vcenter’) then @@127.0.0.1:23033;vcenter
4 Restart services and verify ports
root@NSTEST-syslog:/etc/rsyslog.d# systemctl restart rsyslog
root@NSTEST-syslog:/etc/rsyslog.d# systemctl status resyslog
Unit resyslog.service could not be found.
root@NSTEST-syslog:/etc/rsyslog.d# systemctl status rsyslog
● rsyslog.service – System Logging Service
Loaded: loaded (/lib/systemd/system/rsyslog.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2024-03-25 15:50:40 UTC; 12s ago
TriggeredBy: ● syslog.socket
Docs: man:rsyslogd(8)
man:rsyslog.conf(5)
https://www.rsyslog.com/doc/
Main PID: 12586 (rsyslogd)
Tasks: 12 (limit: 9388)
Memory: 1.8M
CPU: 4ms
CGroup: /system.slice/rsyslog.service
└─12586 /usr/sbin/rsyslogd -n -iNONE
Mar 25 15:50:40 NSTEST-syslog systemd[1]: Starting System Logging Service…
Mar 25 15:50:40 NSTEST-syslog rsyslogd[12586]: imuxsock: Acquired UNIX socket ‘/run/systemd/journal/syslog’ (fd 3) from systemd. [v8.2112.0]
Mar 25 15:50:40 NSTEST-syslog systemd[1]: Started System Logging Service.
Mar 25 15:50:40 NSTEST-syslog rsyslogd[12586]: rsyslogd’s groupid changed to 113
Mar 25 15:50:40 NSTEST-syslog rsyslogd[12586]: rsyslogd’s userid changed to 107
Mar 25 15:50:40 NSTEST-syslog rsyslogd[12586]: [origin software=”rsyslogd” swVersion=”8.2112.0″ x-pid=”12586″ x-info=”https://www.rsyslog.com”] start
root@NSTEST-syslog:/etc/rsyslog.d#
root@NSTEST-syslog:/etc/rsyslog.d#
root@NSTEST-syslog:/etc/rsyslog.d# netstat -tulnp | grep 514
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 12586/rsyslogd
tcp 0 0 0.0.0.0:1514 0.0.0.0:* LISTEN 12586/rsyslogd
tcp 0 0 0.0.0.0:2514 0.0.0.0:* LISTEN 12586/rsyslogd
tcp6 0 0 :::514 :::* LISTEN 12586/rsyslogd
tcp6 0 0 :::1514 :::* LISTEN 12586/rsyslogd
tcp6 0 0 :::2514 :::* LISTEN 12586/rsyslogd
udp 0 0 0.0.0.0:1514 0.0.0.0:* 12586/rsyslogd
udp 0 0 0.0.0.0:2514 0.0.0.0:* 12586/rsyslogd
udp 0 0 0.0.0.0:514 0.0.0.0:* 12586/rsyslogd
udp6 0 0 :::1514 :::* 12586/rsyslogd
udp6 0 0 :::2514 :::* 12586/rsyslogd
udp6 0 0 :::514 :::* 12586/rsyslogd
root@NSTEST-syslog:/etc/rsyslog.d#
root@NSTEST-syslog:~#
Install SOC Handbook Solution
Fortinet Devices (FortiGate)
Local Facility: Changed to Local 7
- sudo tcpdump -i any dst port 28330 -Ann | grep “traffic:forward accept”
SonicWall
Local Facility: Changed to Local 7
Nutanix
- ncli
- rsyslog-config set-status enable=false
- rsyslog-config add-server name=ns-syslog ip-address=10.1.1.135 port=-514 network-protocol=udp relp-enabled=false
- rsyslog-config list-modules server-name=ns-syslog
- rsyslog-conbfig add-module server-name=ns-syslog module-name=audit level=info
- rsyslog-config set-status enable=true
SentinelOne
NOTE: This connector uses Azure Functions to connect to the SentinelOne API to pull its logs into Microsoft Sentinel. This might result in additional data ingestion costs. Check the Azure Functions pricing page for details.
(Optional Step) Securely store workspace and API authorization key(s) or token(s) in Azure Key Vault. Azure Key Vault provides a secure mechanism to store and retrieve key values. Follow these instructions to use Azure Key Vault with an Azure Function App.
NOTE: This data connector depends on a parser based on a Kusto Function to work as expected which is deployed as part of the solution. To view the function code in Log Analytics, open Log Analytics/Microsoft Sentinel Logs blade, click Functions and search for the alias SentinelOne and load the function code or click here. The function usually takes 10-15 minutes to activate after solution installation/update.
STEP 1 – Configuration steps for the SentinelOne API
Follow the instructions to obtain the credentials.
- Log in to the SentinelOne Management Console with Admin user credentials.
- In the Management Console, click Settings.
- In the SETTINGS view, click USERS
- Click New User.
- Enter the information for the new console user.
- In Role, select Admin.
- Click SAVE
- Save credentials of the new user for using in the data connector.
STEP 2 – Choose ONE from the following two deployment options to deploy the connector and the associated Azure Function
IMPORTANT: Before deploying the SentinelOne data connector, have the Workspace ID and Workspace Primary Key
Use the following step-by-step instructions to deploy the SentinelOne Reports data connector manually with Azure Functions (Deployment via Visual Studio Code).
1. Deploy a Function App
NOTE: You will need to prepare VS code for Azure function development.
-
Download the Azure Function App file. Extract archive to your local development computer.
-
Start VS Code. Choose File in the main menu and select Open Folder.
-
Select the top level folder from extracted files.
-
Choose the Azure icon in the Activity bar, then in the Azure: Functions area, choose the Deploy to function app button.
If you aren’t already signed in, choose the Azure icon in the Activity bar, then in the Azure: Functions area, choose Sign in to Azure
If you’re already signed in, go to the next step. -
Provide the following information at the prompts:
a. Select folder: Choose a folder from your workspace or browse to one that contains your function app.
b. Select Subscription: Choose the subscription to use.
c. Select Create new Function App in Azure (Don’t choose the Advanced option)
d. Enter a globally unique name for the function app: Type a name that is valid in a URL path. The name you type is validated to make sure that it’s unique in Azure Functions. (e.g. SOneXXXXX).
e. Select a runtime: Choose Python 3.8.
f. Select a location for new resources. For better performance and lower costs choose the same region where Microsoft Sentinel is located.
-
Deployment will begin. A notification is displayed after your function app is created and the deployment package is applied.
-
Go to Azure Portal for the Function App configuration.
2. Configure the Function App
-
In the Function App, select the Function App Name and select Configuration.
-
In the Application settings tab, select ** New application setting**.
-
Add each of the following application settings individually, with their respective string values (case-sensitive):
SentinelOneAPIToken
SentinelOneUrl
WorkspaceID
WorkspaceKey
logAnalyticsUri (optional)
- Use logAnalyticsUri to override the log analytics API endpoint for dedicated cloud. For example, for public cloud, leave the value empty; for Azure GovUS cloud environment, specify the value in the following format:
https://<CustomerId>.ods.opinsights.azure.us.
- Once all application settings have been entered, click Save.
















