In this post, I am going to show you an easy way to execute Penertration testing in your network for free in 30 days.
Just using one command auto-generated from https://www.horizon3.ai/ ‘s Nodezero platform, you will be able to execute a professional pen testing to reveal some proven attack paths in your network, and find out weakness imapct to your organizaiton.
Introduction
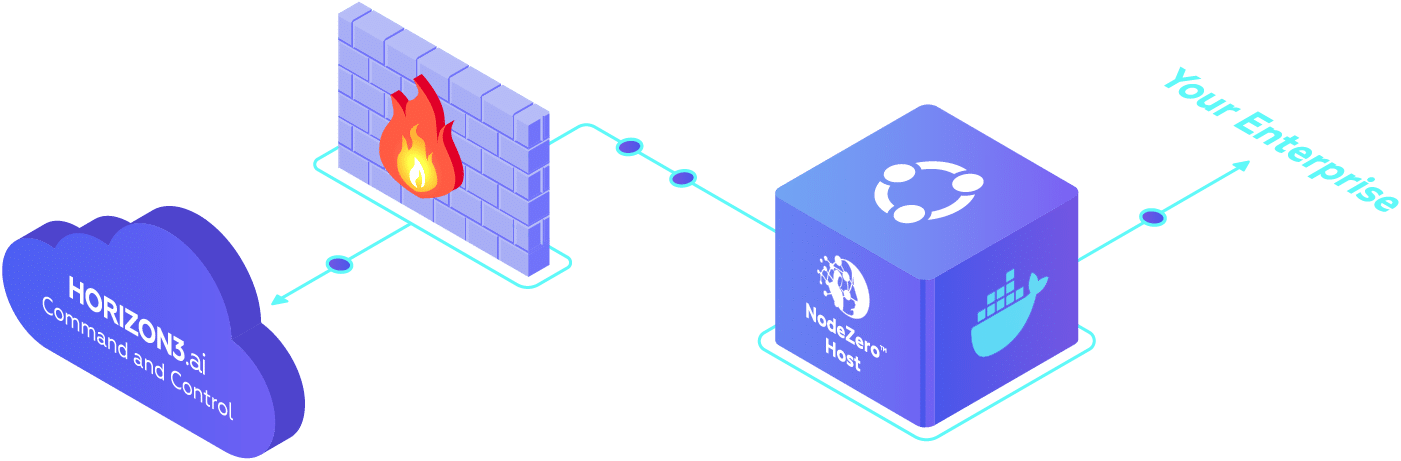
NodeZero is a Docker container that acts as a beachhead inside your network. It receives and executes pentesting instructions from Horizon3’s Command and Control Server running in the Horizon3 cloud.
After configuring a pentest using this wizard, you’ll receive a custom NodeZero Launch Script command that must be executed on your NodeZero Host. The launch script deploys NodeZero and begins the pentest.
What do I do after configuring my pentest?
After configuring your pentest, copy the NodeZero Launch Script and deploy on your Docker Host.
NodeZero acts as a ‘beachhead’ within your network. It receives instructions from Horizon3’s Command and Control Server and scans your network for weaknesses, using the same tools and tactics as a real-world attacker.
Prepare Your Nodezero node (Linux VM)
- 2 vCPU
- 4GB RAM
- 20 GB Free hard drive space
- apt update -y && apt upgrade -y
- apt install docker
Steps to generate one line command to launch Pen Testing
1 Run Pentest and select Internal Pentest
2 Enter your network infomation for Pentest Scope
3 Customize your Attack Configuration
Review custom pentest settings before get the code:
4 Deploy the code:
Launch NodeZero Copy and run this one-time command on your Docker Host to install and run NodeZero.
curl "https://h3ai-pre-scripts-prod.s3.amazonaws.com/1d866a69-1fa1-453b-9495-819ca2f096b5-pre-script.sh?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIARYGGS7XWWNF6CWWX%2F20240126%2Fus-east-2%2Fs3%2Faws4_request&X-Amz-Date=20240126T023903Z&X-Amz-Expires=43200&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEOL%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJGMEQCIF0%2BvP4Pg%2Bvq9GOpMZSE1qje80uikkAT0g%2F03ipVGI2DAiAcEp18Y3VGMCRudQDzqZI6BjWb9ibB5zBWE2Q8K9VsoyqDAwib%2F%2F%2F%2F%2F%2F%2F%2F%2F%2F8BEAIaDDEyMDY3NTU2NTAzNyIM8M26kdKvM5ePw7%2BxKtcCy1kOkVIgKBP3ZTBz%2B22tgcZr0M2ttZf4gBsR9%2BZJK2qqXhJuXJ5LPGN1KxyAIPxYXaBxzOzUhJGX7o88N%2FUEIKjLsnPDxZYqBtwVn692XGwk0TZ3TWfE89me36aFk%2Fcin19fwPF%2FXOPutUHFshYdzqHwbKeyDjtbaxb5u75uunX1vE9dedK2tllBKyz17yqxy2XcdpoZ7f%2FUMowSoKghUnngdM1ze%2B2SSFJxr4BzDWBJOenFodn0o6ImzChmmk8l6WgZZhqTnSDhW57sFeaW04djcUdaxtbWr3qqCeX8xN2uAn2V7H8%2BSaXpJtdNs306felw4Ay8Bv7P%2FTOLqIcIZJOxsFb6kjh%2Fds%2FMz97lDvbFzOWfqy%2B3kwqk%2FuvO%2BcJwIvn2gH%2B1yb8c2Hwaa9jyV%2FQjyX3tgDipgmjWUgECb1T6oZcotboer9uwitOCyVcnqqnEUft06TDzpcytBjqfAeRlSXuzKQQYL5MrK1VajoTQVYzP%2BPgd8YXQabina8O599MhXEy33ZF1tWTfSVHsMDuE%2FQj9yITDPNbiL7CiG4J9fCvSp3szpDhKr6GFHY0td8qljmGfbgYt9Ou1E1w5DCyjB87DYfCiJl65nU9cjlUkjD%2FPPRZ3Msl6wuR68xgAKgBykvyMSHmJPj0elOy%2F6LQNpWmbOl1AJzZvSSkz2g%3D%3D&X-Amz-Signature=aaa8acf2e68bfd88ff2c95b157c9be332bdb417638ea9f49583e1e30f26b1106" | bash
root@u20svr:~# curl “https://h3ai-pre-scripts-prod.s3.amazonaws.com/1d866a69-1fa1-453b-9495-819ca2f096b5-pre-script.sh?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIARYGGS7XWWNF6CWWX%2F20240126%2Fus-east-2%2Fs3%2Faws4_request&X-Amz-Date=20240126T023903Z&X-Amz-Expires=43200&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEOL%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJGMEQCIF0%2BvP4Pg%2Bvq9GOpMZSE1qje80uikkAT0g%2F03ipVGI2DAiAcEp18Y3VGMCRudQDzqZI6BjWb9ibB5zBWE2Q8K9VsoyqDAwib%2F%2F%2F%2F%2F%2F%2F%2F%2F%2F8BEAIaDDEyMDY3NTU2NTAzNyIM8M26kdKvM5ePw7%2BxKtcCy1kOkVIgKBP3ZTBz%2B22tgcZr0M2ttZf4gBsR9%2BZJK2qqXhJuXJ5LPGN1KxyAIPxYXaBxzOzUhJGX7o88N%2FUEIKjLsnPDxZYqBtwVn692XGwk0TZ3TWfE89me36aFk%2Fcin19fwPF%2FXOPutUHFshYdzqHwbKeyDjtbaxb5u75uunX1vE9dedK2tllBKyz17yqxy2XcdpoZ7f%2FUMowSoKghUnngdM1ze%2B2SSFJxr4BzDWBJOenFodn0o6ImzChmmk8l6WgZZhqTnSDhW57sFeaW04djcUdaxtbWr3qqCeX8xN2uAn2V7H8%2BSaXpJtdNs306felw4Ay8Bv7P%2FTOLqIcIZJOxsFb6kjh%2Fds%2FMz97lDvbFzOWfqy%2B3kwqk%2FuvO%2BcJwIvn2gH%2B1yb8c2Hwaa9jyV%2FQjyX3tgDipgmjWUgECb1T6oZcotboer9uwitOCyVcnqqnEUft06TDzpcytBjqfAeRlSXuzKQQYL5MrK1VajoTQVYzP%2BPgd8YXQabina8O599MhXEy33ZF1tWTfSVHsMDuE%2FQj9yITDPNbiL7CiG4J9fCvSp3szpDhKr6GFHY0td8qljmGfbgYt9Ou1E1w5DCyjB87DYfCiJl65nU9cjlUkjD%2FPPRZ3Msl6wuR68xgAKgBykvyMSHmJPj0elOy%2F6LQNpWmbOl1AJzZvSSkz2g%3D%3D&X-Amz-Signature=aaa8acf2e68bfd88ff2c95b157c9be332bdb417638ea9f49583e1e30f26b1106” | bash
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 15903 100 15903 0 0 41199 0 –:–:– –:–:– –:–:– 41199
[#] Conducting pre-checks to validate the environment is NodeZero ready:
[#] Checking Docker functionality by running the hello-world test container:
[+] PASSED: Docker version installed meets the minimum required version 20.10.
[+] PASSED: Docker is installed and functioning properly.
[#] Checking Docker permissions to volume mount files from /root directory:
[+] PASSED: Docker permissions are correct for the /root directory location.
[#] Checking Operating System:
[+] PASSED: Linux is a supported Operating System.
[#] Gathering environmental variables to conduct further checks:
[+] PASSED: All environmental variables set and proceeding with next checks.
[#] Checking host time against current UTC time:
[+] PASSED: System time is within 5 minutes of UTC time.
[#] Checking HDD space requirements (20GB Recommended, 10GB Required):
[!] WARNING: 10GB is less than the recommended 20GB free space on this disk, please ensure to prune old images before running Node Zero again.
[#] Checking 8GB RAM requirement:
[+] PASSED: This system meets the recommended minimum RAM to support NodeZero.
[#] Checking compute resource requirements:
[+] PASSED: This system has 4 CPUs which meets the minimum logical CPU requirements to run NodeZero.
[#] Pre-check validation completed successfully.
[#] Downloading NodeZero configuration …
[#] Checking for previous NodeZero configuration file artifacts:
ls: cannot access ‘/root/.nodezero/n0*.conf’: No such file or directory
[+] No previous NodeZero configuration files identified.
[#] Checking for previous NodeZero container artifacts to remove and reclaim space:
[+] Current state of containers is as follows:
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[+] PASSED: No previous NodeZero containers identified.
[#] Checking for previous NodeZero image artifacts to remove and reclaim space:
[+] Current state of images is as follows:
REPOSITORY TAG IMAGE ID CREATED SIZE
[+] PASSED: No previous NodeZero images identified.
[#] Authenticating to Amazon ECR to pull down the NodeZero Docker container.
[+] Authentication successful.
[#] Creating the Operation specific configuration file and retrieving the latest NodeZero container, it will take a few minutes:
2024.01.10.4: Pulling from h3/n0
3bb57870a639: Pull complete
ae1edd5d9b04: Pull complete
Digest: sha256:acdb92924286dfde034065c92009940072c70204b5d7fa0d60e27c11d690e708
Status: Downloaded newer image for 120675565037.dkr.ecr.us-east-2.amazonaws.com/h3/n0:2024.01.10.4
120675565037.dkr.ecr.us-east-2.amazonaws.com/h3/n0:2024.01.10.4
[+] PASSED: Successfully pulled the latest NodeZero container.
[#] Checking if this Operation has been started already:
ea584f0cb7341f738a1d04c24ba61399615785ff7f76c5a95ba58790ffb8a66d
[#] Success! Your NodeZero Operation has been launched. The NodeZero container will automatically shut itself down after the operation is complete. To view the logs, run ‘docker logs -f n0-904b’.
root@u20svr:~#
Videos
References
- Download
- NodeZero Host Virtual Machine (OVA/VHD)
- Blue Team Toolkit