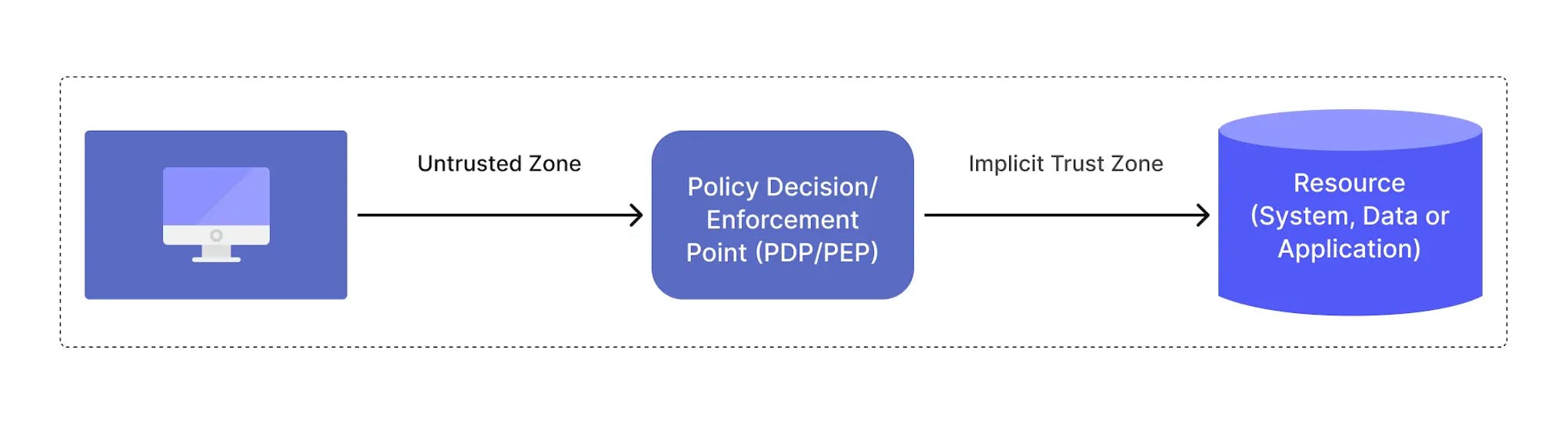
Zero trust architectures are constructed on the basis that there is no secure perimeter. Instead, every event and connection is considered untrusted and potentially malicious.
The goal of zero trust architectures is to keep networks protected despite increasingly sophisticated threats and complex perimeters. This is why zero trust architecture is also called zero trust network, or in general — zero trust security.
From Microsoft: https://learn.microsoft.com/en-us/security/zero-trust/zero-trust-overview
Definitions
- Zero trust (ZT) provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
- Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.
What is zero trust?
A zero trust model implements data security that prioritizes access and restrictions. This is particularly relevant in today’s business environment, as organizations increasingly need to secure a remote workforce.
In a zero trust architecture, users, devices, and services receive the least possible privileges until proven trustworthy. Sometimes, when implementing zero trust network access, privilege restrictions extend even after authentication and authorization.
In particular, zero threat architectures are designed to reduce the vulnerabilities associated with cloud resources, ephemeral endpoints, dynamic attacks and internet of things (IoT) devices. These architectures are often adopted by organizations with highly sensitive data and systems.
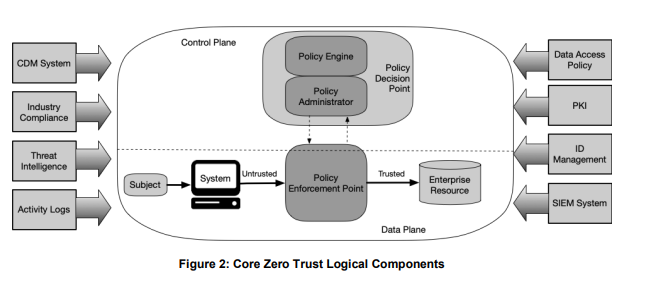
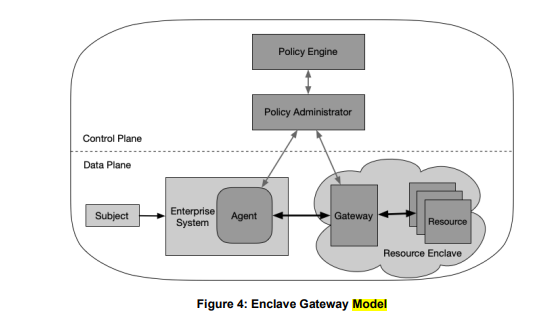
NIST document, page 18. Zero trust model components.
- Policy engine (PE) – the PE makes decisions as to whether to grant access based on policy and input from CDM systems and threat intelligence services.
- Policy administrator (PA) – the PA creates or shuts down a communication based on decisions from the PE.
- Policy enforcement point (PEP) – the PEP grants, monitors, and terminates connections.
NIST developed ZT guidelines recommending agencies design and deploy a ZTA with adherence to seven basic tenets, which we will expand on further in this section.
The Department of Defense (DoD) and the National Security Agency (NSA) guidelines offer a more operational and micro-level approach to ZT than the guidance from NIST. NSA’s ZTA is very similar to DoD’s ZTA and includes the same seven pillars. These two differ in their focus. DoD’s ZTA was developed with a defence-specific mission and requirements in mind and uses the Department of Defense Architecture Framework (DoDAF) while the NSA ZTA was developed for the NSA and defence industrial base organizations.
CISA drafted a ZT maturity model and draws upon the pillar concept from the DoD and NSA ZTA. CISA’s ZT model focuses on five distinct pillars supported by overarching capabilities for visibility and analytics, automation and orchestration, and governance. It was created to help all types of federal agencies in the development of their ZTA.
The United Kingdom (UK) NCSC guidance is based on eight principles that represent the main building blocks and architectural considerations needed to develop a ZTA. Every organization will have a somewhat different approach to achieving ZT depending on their business requirements, the technologies they use, and their threat landscape. The NCSC ZT guidance was developed with that in mind and believes that most ZT approaches can be linked to these eight core principles.
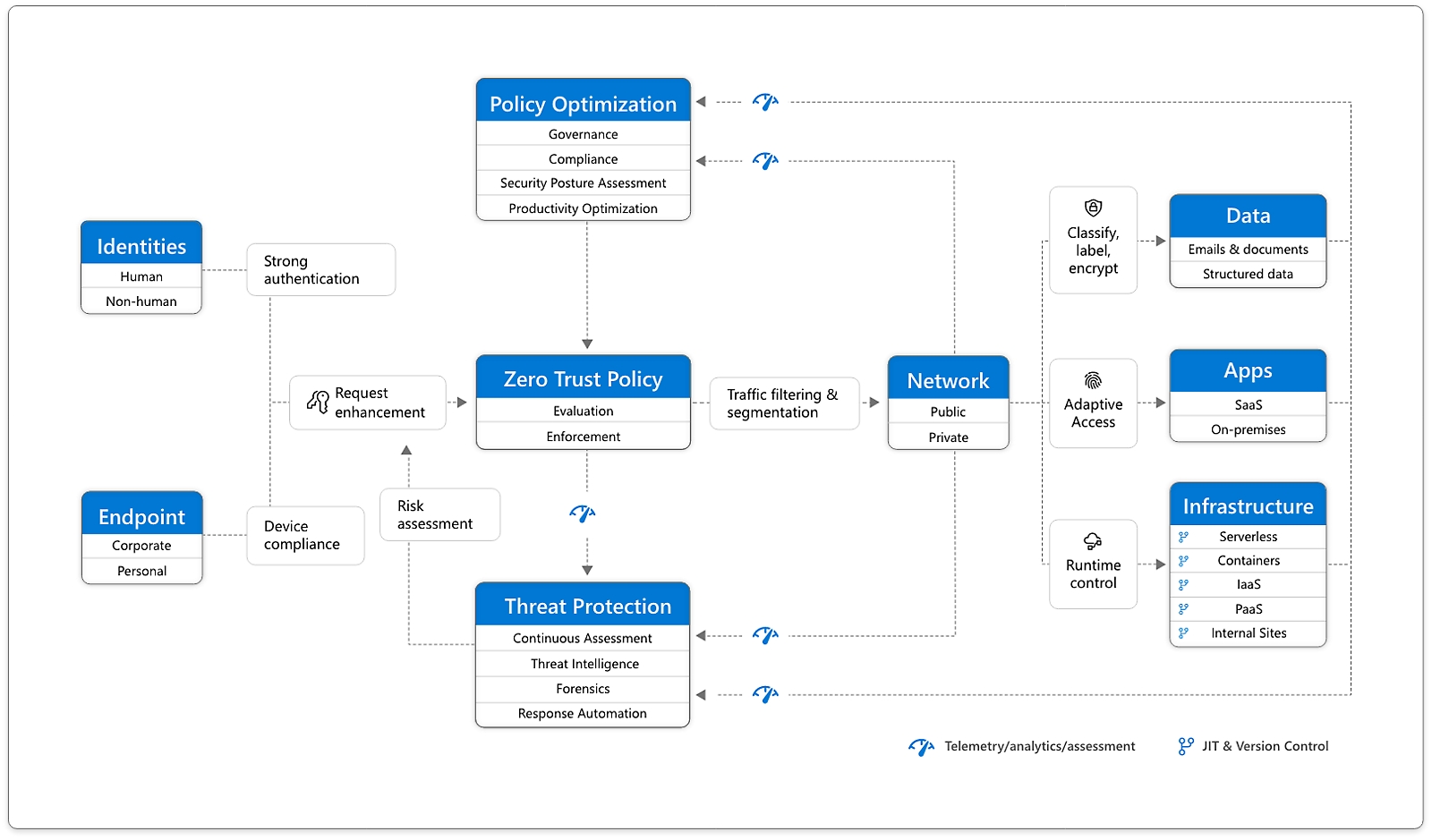
Zero trust architecture diagram
Note: https://www.trendmicro.com/en_za/what-is/what-is-zero-trust/zero-trust-architecture.html#:~:text=Zero%20trust%20frameworks&text=For%20example%2C%20Gartner%20uses%20the,Zero%20Trust%20Edge%20(ZTE).
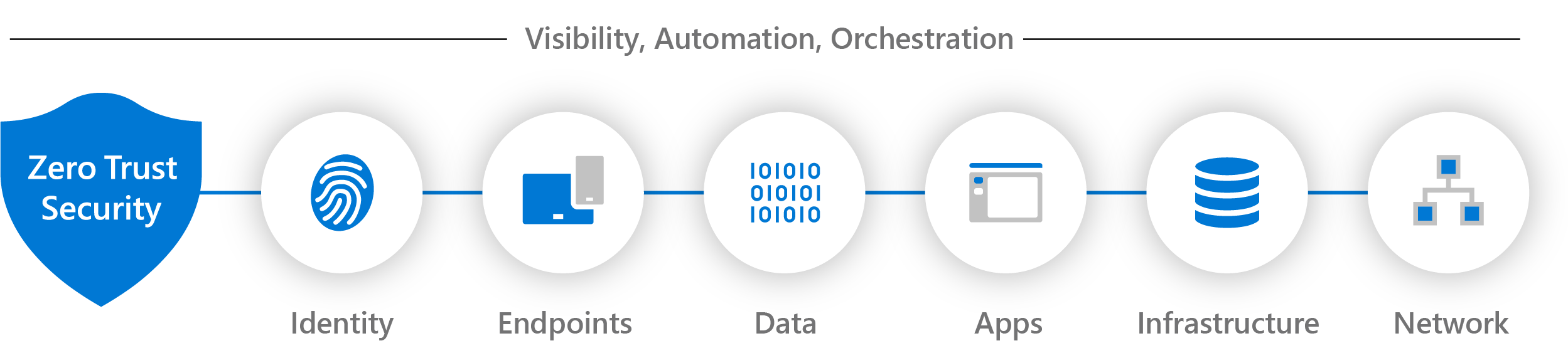
A holistic approach to Zero Trust from Microsoft
Principle
Microsoft
- Verify explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least-privilege access: Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Pillars
Microsoft
1 Identities
Verify and secure each identity with strong authentication across your entire digital estate.
2 Endpoints
Gain visibility into devices accessing the network. Ensure compliance and health status before granting access.
3 Apps
Discover shadow IT, ensure appropriate in-app permissions, gate access based on real-time analytics, and monitor and control user actions.
4 Data
Move from perimeter-based data protection to data-driven protection. Use intelligence to classify and label data. Encrypt and restrict access based on organizational policies.
5 Infrastructure
Use telemetry to detect attacks and anomalies, automatically block and flag risky behavior, and employ least-privilege access principles.
6 Network
CISA’s depiction of the foundation of Zero Trust
- Idnetity
- Network/Environment
- Device
- Application workload
- Data
- Vibility and analytics
- Automation and Orchestration
- Governance
Other Vendor’s Pillars:
- Identy verify constantly (people, application, SSO (MFA, Passwordless, no legacy auth), ,
- Least privilege, (RBAC, JIT, PAM)
- Assume breach
- Endpoint (TPM, Device Certs, Mgmt, Compliance)
- Network (end 2 end encryption (TLS, IPSec), DiD (Layers, tiers), Micro-Segmentation (NSG, ASG, AZ FW))
- Administration
- Monitoring session
- Policy, Conditional Access,
- Infra
- App
- Data
Maturity Model
To facilitate transitioning to ZT across the five different pillars, CISA outlined a ZT Maturity Model gradient using three stages, with increasing levels of commitment. CISA provided the following descriptions for each stage to identify the maturity for each ZT technology pillar and to provide consistency across the maturity model:
- Traditional: Manual configurations and assignment of attributes, static security policies, pillar-level solutions with coarse dependencies on external systems, least-function established at provisioning, proprietary and inflexible pillars of policy enforcement, manual incident response and mitigation deployment.
- Advanced: Some cross-pillar coordination, centralized visibility, centralized identity control, policy enforcement based on cross-pillar inputs and outputs, some incident response to pre-defined mitigations, increased detail in dependencies with external systems, some least-privilege changes based on posture assessments.
- Optimal: Fully automated assigning of attributes to assets and resources, dynamic policies based on automated and observed triggers, assets have self-enumerating dependencies for dynamic least-privilege access (within thresholds), alignment with open standards for cross-pillar interoperability, centralized visibility with historian functionality for point-in-time recollection of state.
CISA’s high-level ZT maturity model
Traditional – Maturity level
Identity
- Password or multi-factor authentication (MFA)
- Limited risk assessment
Device
- Limited visibility into compliance
- Simple inventory
Network/Environment
- Large macro-segmentation
- Minimal internal or external traffic encryption
Application workload
- Access based on local authorization
- Minimal integration with workflow
- Some cloud accessibility
Data
- Not well inventoried
- Static control
- Unencrypted
Advanced – Maturity level
Identity
- MFA
- Some identity federation with cloud and on- premises systems
Device
- Compliance enforcement employed
- Data access depends on device posture on first access
Network/Environment
- Defined by ingress/egress micro-perimeters
- Basic analytics
Application workload
- Access based on centralized authentication
- Basic integration into application workflow
Data
- Least privilege controls
- Data stored in cloud or remote environments are encrypted at rest
Optimal – Maturity level
Identity
- Continuous validation
- Real time machine learning analysis
Device
- Constant device security monitor and validation
- Data access depends on real-time risk analytics
Network/Environment
- Fully distributed ingress/egress micro-perimeters
- Machine learning-based threat protection
- All traffic is encrypted
Application workload
- Access is authorized continuously
- Strong integration into application workflow
Data
- Dynamic support
- All data is encrypted
Major Principles – Zero Trust
Zero Trust (Assume-Breach)
The key tenets of a modern defense-in-depth strategy include:
- Protect privileged access – use privileged access management solutions to monitor and secure access to privileged accounts (superuser accounts, local and domain administrator accounts, application administrative accounts, etc.) by both human and non-human identities (applications, scripts, bots, etc.).
- Lockdown critical endpoints – use advanced endpoint privilege management solutions to lock down privilege across all endpoints, prevent lateral movement, and defend against ransomware and other forms of malware.
- Enable adaptive multifactor authentication – use contextual information (location, time of day, IP address, device type, etc.) and business rules to determine which authentication factors to apply to a particular user in a particular situation.
- Secure developer tools – use secrets management solutions to secure, manage, rotate and monitor secrets and other credentials used by applications, automation scripts, and other non-human identities.
Zero Trust vs Defense in Depth
5 Steps to Create a Zero Trust Network
Use Cases. Best Practices, Solutions
Use Cases:
- Replacing or augmenting a VPN: Many organizations rely on VPNs to protect their data, but as described above, VPNs are often not ideal for defending against today’s risks.
- Securely supporting remote work: While VPNs create bottlenecks and can slow productivity for remote workers, Zero Trust can extend secure access control to connections from anywhere.
- Access control for cloud and multi-cloud: A Zero Trust network verifies any request, no matter its source or destination. It can also help reduce the use of unauthorized cloud-based services (a situation called “shadow IT”) by controlling or blocking the use of unsanctioned apps.
- Onboarding third parties and contractors: Zero Trust can quickly extend restricted, least-privilege access to external parties, who typically use computers that are not managed by internal IT teams.
- Rapidly onboarding new employees: Zero Trust networks can also facilitate quickly onboarding new internal users, making them a good fit for fast-growing organizations. In contrast, a VPN may need to add more capacity to accommodate large numbers of new users.
Best Practices:
- Always Verify the User with Multi-factor Authentication (MFA)
- Always Validate the Device
- Ensure the Device Measures Up to Your Security Standards
- Least Access and Least Privilege for IT and Everybody Else
- Use a Solution that Learns and Adapts
- Monitor network traffic and connected devices: Visibility is crucial in order for users and machines to be verified and authenticated.
- Keep devices updated: Vulnerabilities need to be patched as quickly as possible. Zero Trust networks should be able to restrict access to vulnerable devices (another reason why monitoring and validation are key).
- Apply the principle of least privilege for everyone in the organization: From executives to IT teams, everyone should have the least amount of access they need. This minimizes the damage if an end user account becomes compromised.
- Partition the network: Breaking up the network into smaller chunks helps ensure breaches are contained early, before they can spread. Microsegmentation is an effective way to do this.
- Act as if the network perimeter did not exist: Unless a network is completely air-gapped (a rarity), the points where it touches the Internet or the cloud are probably too numerous to eliminate.
- Use security keys for MFA: Hardware-based security tokens are demonstrably more secure than soft tokens like one-time passcodes (OTPs) sent via SMS or email.
- Incorporate threat intelligence: Since attackers are constantly updating and refining their tactics, subscribing to the latest threat intelligence data feeds is critical for identifying threats before they spread.
- Avoid motivating end users to circumvent security measures: Just as overly strict password requirements incentivize users to recycle the same passwords over and over, forcing users to re-authenticate once an hour via multiple identity factors may be too much, ironically decreasing security. Always keep the end user’s needs in mind.
Solutions:
- Threat detection and response solutions
- Identity and privileged access management
- Endpoint and data protection
- Security services
Implementation
Fortinet:
- Defining the attack surface: Defining your attack surface should be the first item on your zero trust checklist. To do this, you want to hone in on the areas you need to protect. This way, you will not be overwhelmed with implementing policies and deploying tools across your entire network. Focus on your most valuable digital assets.
- Sensitive Data: This includes the data of customers and employees, as well as proprietary information you do not want to fall into the hands of a thief.
- Critical Applications: These are the applications that play a central role in your most crucial business processes.
- Physical Assets: Physical assets can range from point-of-sale (PoS) terminals to Internet-of-Things (IoT) devices to medical equipment.
- Corporate Services: These include the elements of your infrastructure used to support the day-to-day work of employees and executives, as well as those that facilitate customer sales and interactions.
- Implementing controls around network traffic : The way traffic flows through your network will often pivot on the dependencies each system uses. For example, many systems need to access a database holding customer, product, or service information.
- Requests, therefore, do not simply “go into the system.” Rather, they have to be routed through a database containing sensitive and delicate information and architecture. Understanding these kinds of details will help you decide which network controls to implement and where to position them.
- Architecting your zero trust network: A zero trust network is designed around your specific protect surface—there is never a one-size-fits-all solution. In most situations, your architecture may begin with a next-generation firewall (NGFW), which can act as a tool for segmenting an area of your network. Also at some point, you will want to implement multi-factor authentication (MFA) to ensure users are thoroughly vetted before being granted access.
- Creating a zero trust policy structured around asking who, what, when, where, why, and how when it comes to people and systems that want to connect to areas of your network.
- After you have architected the network, you will want to design your zero trust policies. This is most effectively done using what is known as the Kipling Method. This involves asking who, what, when, where, why, and how for every user, device, and network that wants to gain access.
- Monitor Your Network: Monitoring activity on your network can alert you to potential issues sooner and provide valuable insights for optimizing network performance—without compromising security.
- Reports: Reports produced on a regular or ongoing basis can be used to flag abnormal behavior. You can also analyze them to assess how your zero trust system impacts employee or system performance and ways you may be able to improve it.
- Analytics: Analytics takes data generated by your system and provides insights regarding how well it functions. Insights are valuable when you need to monitor network traffic, the performance of components of the network, and patterns of user behavior.
- Logs: The logs produced by your system provide you with a permanent, time-stamped record of activity. These can be analyzed manually or using analytical tools, such as machine-learning algorithms that can recognize patterns and anomalies.

References
- Knowledge Overview (Principles, CIA, DiD, PPT, Zero Trust)
- The National Institute of Standards and Technology (NIST): Special publication 800-207: Zero Trust Architecture (PDF)
- Cybersecurity and Infrastructure Security Agency (CISA): Zero Trust Maturity Model (PDF)
- National Cyber Security Center (NCSC): Zero trust architecture design principles
- A zero trust approach to security architecture – ITSM.10.008
- Cloudflare Zero Trust Tunnels (Previously Argo) for Home Internal Application Access