Governance is at the centre of effective technology risk management. Those charged with governance should work with the management team to develop and oversee the firm’s technology strategy and risk management program.
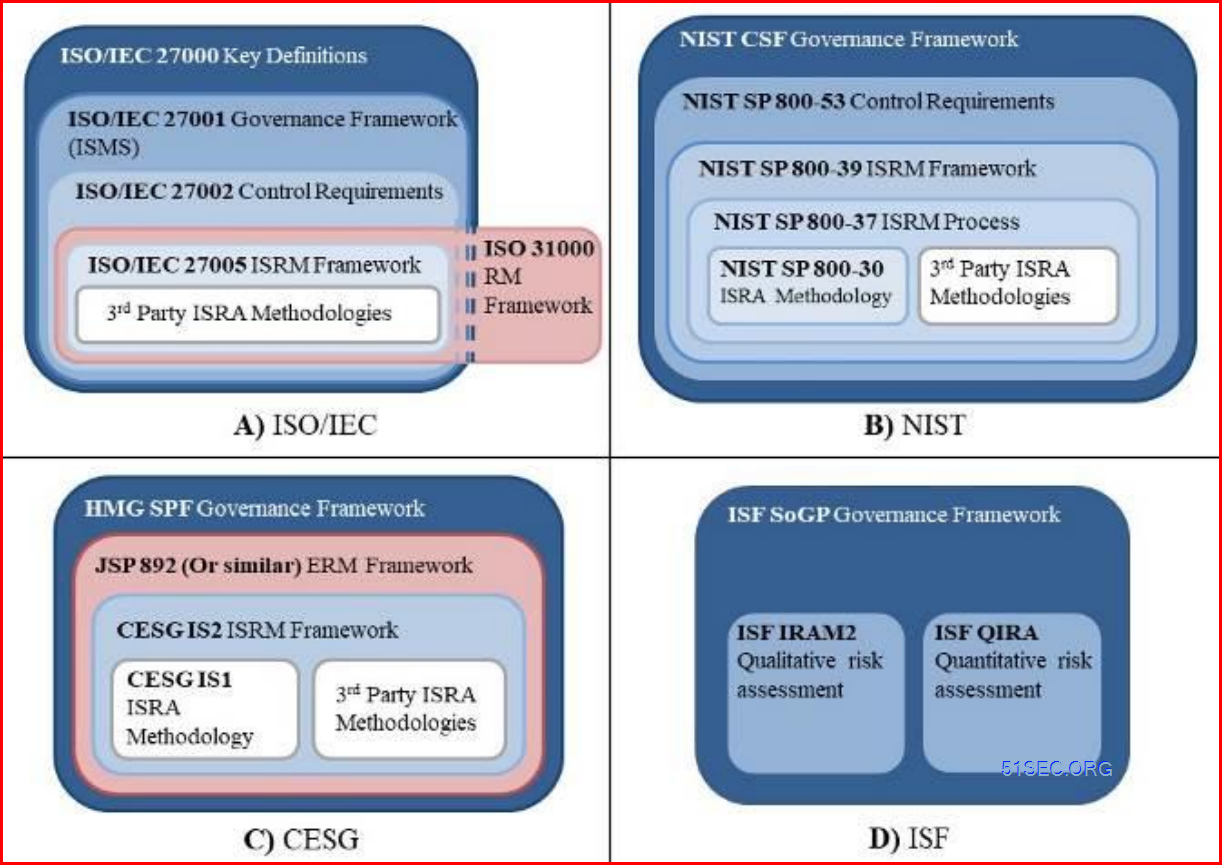
Visual Representation of artefacts underpinning key ISRM framworks
NIST RMF Framework
More than ever, organizations must balance a rapidly evolving cybersecurity and privacy threat landscape against the need to fulfill business requirements on an enterprise level. Risk management underlies everything that NIST does in cybersecurity and privacy and is part of its full suite of standards and guidelines. To help organizations to specifically measure and manage their cybersecurity risk in a larger context, NIST has teamed with stakeholders in each of these efforts. Examples include:
- Integrating Cybersecurity and Enterprise Risk Management (ERM)
- NIST Cybersecurity Framework (CSF)
- Risk Management Framework (RMF)
- Privacy Framework
- Cybersecurity Supply Chain Risk Management (C-SCRM)
- Workforce Framework for Cybersecurity (NICE Framework)
The Risk Management Framework (RMF) provides a flexible and tailorable seven-step process that integrates cybersecurity and privacy, along with supply chain risk management activities, into the system development life cycle. The NIST RMF links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal Information Security Modernization Act (FISMA), including control selection, implementation, assessment, and continuous monitoring. NIST updated the RMF to support privacy risk management and to incorporate key Cybersecurity Framework and systems engineering concepts. Originally targeted at federal agencies, today the RMF is also used widely by state and local agencies and private sector organizations.

For more information on each RMF Step, including Resources for Implementers and Supporting NIST Publications, select the Step below.
| Prepare |
Essential activities to prepare the organization to manage security and privacy risks |
| Categorize |
Categorize the system and information processed, stored, and transmitted based on an impact analysis |
| Select |
Select the set of NIST SP 800-53 controls to protect the system based on risk assessment(s) |
| Implement |
Implement the controls and document how controls are deployed |
| Assess |
Assess to determine if the controls are in place, operating as intended, and producing the desired results |
| Authorize |
Senior official makes a risk-based decision to authorize the system (to operate) |
| Monitor |
Continuously monitor control implementation and risks to the system |
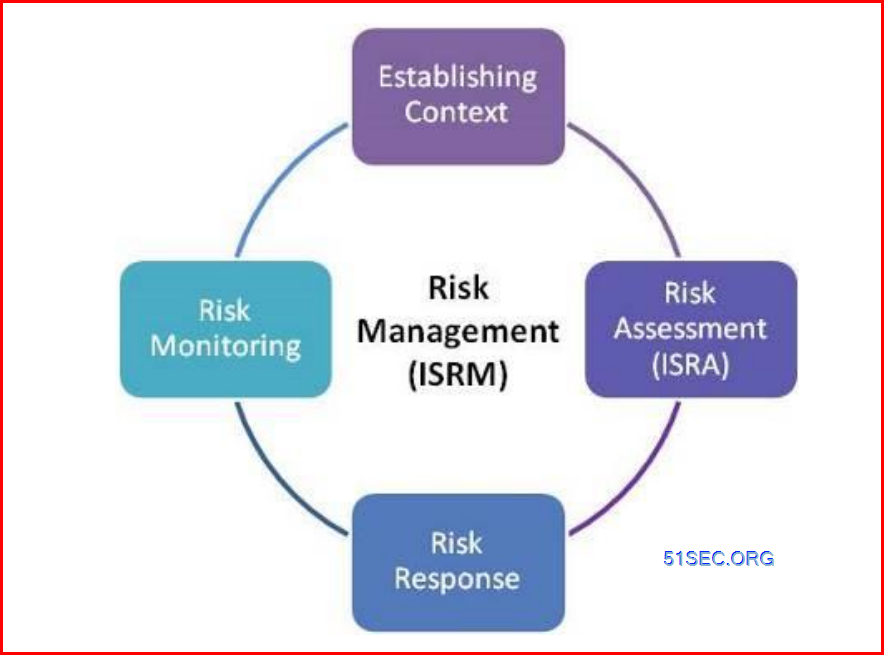
SP 800-39 outlines a flexible ISRM framework that champions a nonsequential ISRM process and highlights the need to manage infosec risks at various levels of abstraction. Whilst the ISRM process covers the basic steps of assessing, responding to and monitoring infosec risks, it also introduces the concept of framing risk. Risk framing ‘describes the environment in which risk-based decisions are made’, effectively establishing the governance processes surrounding ISRM and identifying the legal, regulatory and organisational constraints that may affect ISRM. The framework identifies the information and communication flows that hold the process together but stresses that they are bi-directional owing to the need for a dynamic ISRM process that can accommodate the realities of ‘real-life’.
NIST ISRM Process
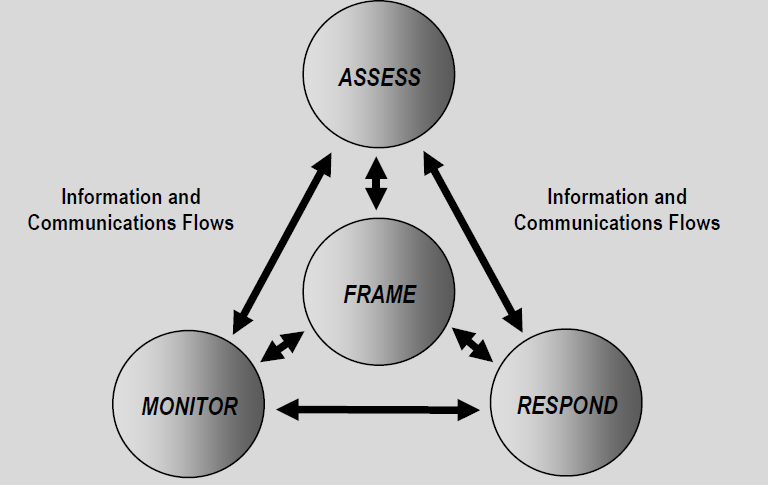 |
| NIST: Risk Assessment within The Risk Management Process |
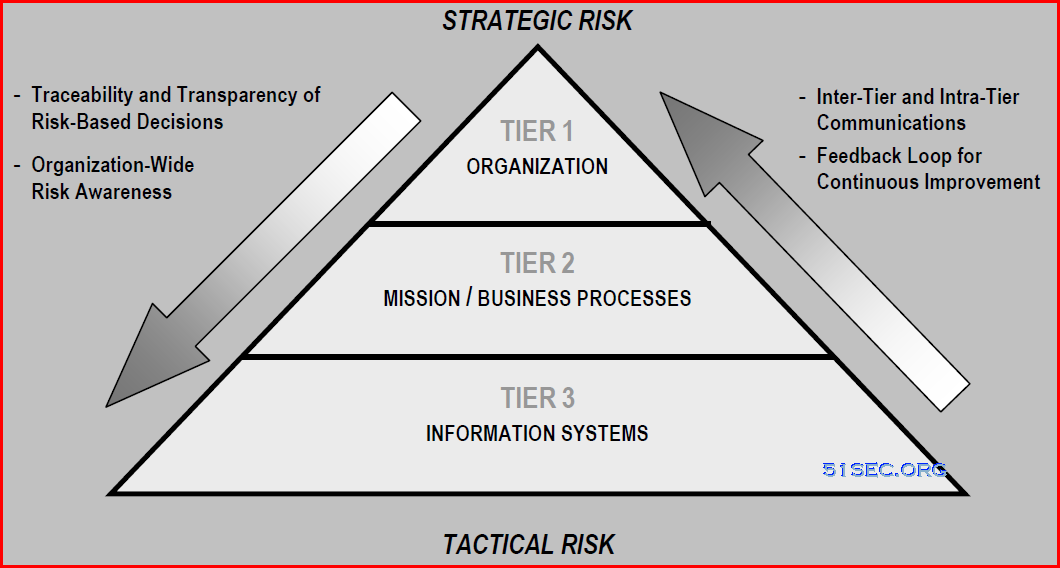 |
| NIST Multitiered ISRM Model: Risk Management Hierarchy |
ISF IRAM2
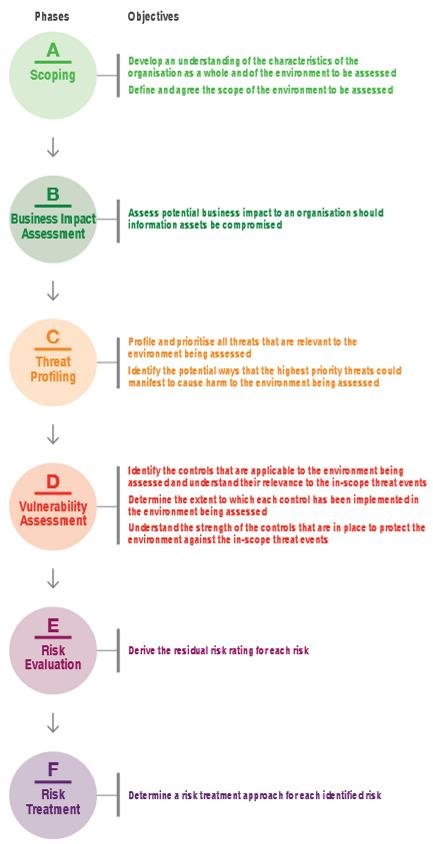
IRAM2 is a unique methodology for assessing and treating information risk. It includes guidance for risk practitioners to implement the six-phase process, consisting of Scoping, Business Impact Assessment, Threat Profiling, Vulnerability Assessment, Risk Evaluation, and Risk Treatment.
IRAM2 is supported by four IRAM2 Assistants, each accompanied by a practitioner guide, that help automate one or more phases of the methodology. Additionally, IRAM2 is supported by the IRAM2 WebApp, which is an online assessment tool for performing information risk assessments using the ISF IRAM2 information risk assessment methodology.
Challenge
– Isolated and ad hoc
assessments
– Inconsistent approaches
– Business impact not
assessed
– Lack of effective
communication
– Ambiguous accountability
Solution
– Structured and repeatable process utilised
and customised templates
– Business Impact Assessment (BIA) ensured engagement
and alignment with business priorities
– Summary pages produced for reporting
– Scoping and profiling steps assisted in the identification
of asset ownership and classification
Member recommendations
– Well structured, customised IRAM2 templates made for easy
update and engagement from business stakeholders
– Capture organisational risk appetite at the outset to achieve
full benefits of using IRAM2
– Involve stakeholders to ensure understanding of the key
terms, concepts and objectives
– Group individual assets and associated components and
complete the BIA on the overall scope, to result in a more
manageable number of risks being identified
– Leverage the summary pages in the tool to show a high-level
risk profile to senior stakeholders
ISF IRAM2 ISRA process
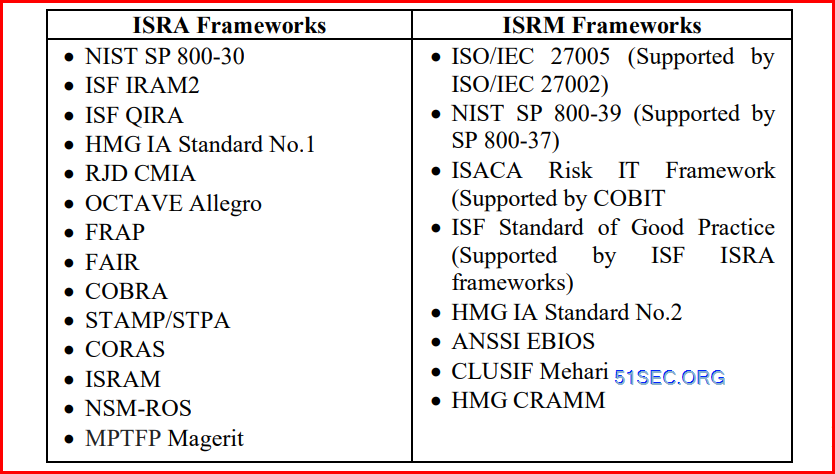
Relationship between ISRA (Information Security Risk Assessment) and ISRM (Information Security Risk Management) frameworks
ISRA frameworks provide organisations with qualitative
or quantitative methods that could be used to identify
infosec risks posed towards a target system or process [5].
In contrast, ISRM frameworks may discuss techniques for
ISRA but they also encompass methods for setting the
context for risk identification, and subsequently responding
to and monitoring infosec risks; covering the end to end
management of infosec risks.
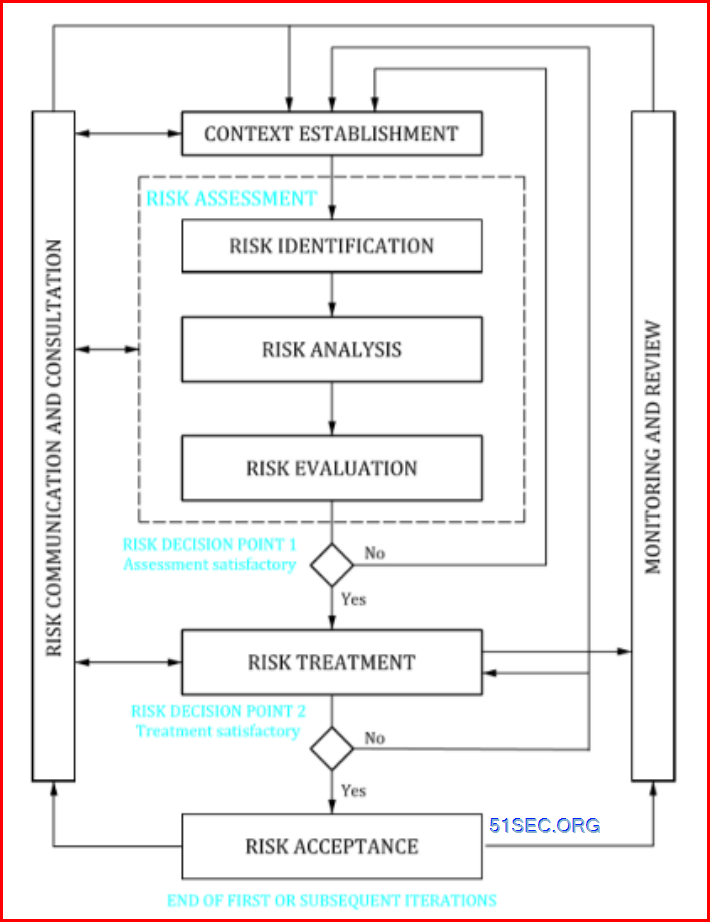
ISO/IEC 27005 ISRM Process
There are two Risk Decision Points, one for sessment satisfactory, another is for Treatment satisfactory.
At the end of diatram, it says end of first or susequent iteration.
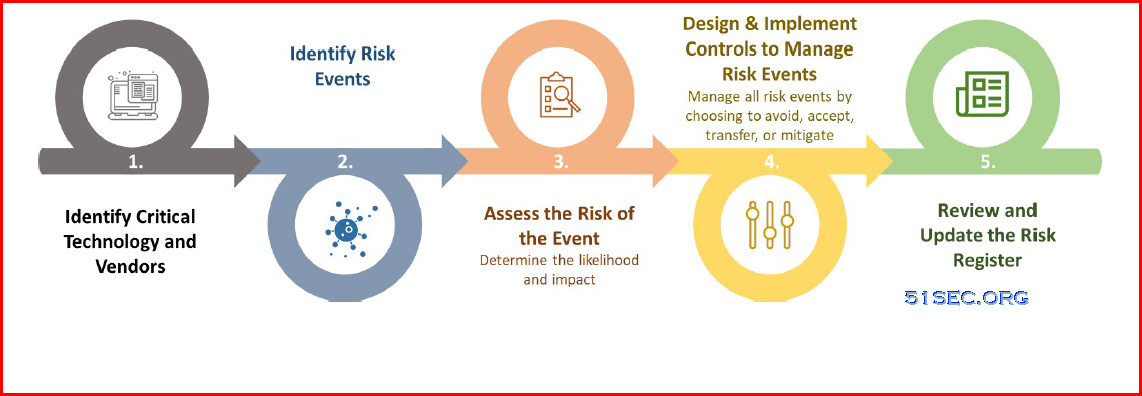
Process of Manging Risk (Technology)
Generally, firms should consider developing a process to manage risk:
This process can also be used to manage all other types of risks at the firm.
1 Identify critical technology and vendors
The first step is to itemize a list of all the technology being used at the firm, who and which business area uses it, and for what purpose. This will help determine the critical technology that the firm uses and relies on, which is a key first step. The following are potential areas for firms to consider:
a. The list should be filled out by the business line staff and technology staff to inventory alltechnology being used at the firm. Refer to Appendix B for a high-level summary of areas wheretechnology is generally used in the investment industry.
b. In order to effectively manage the risk, the identification should also incorporate
i. How the firm is accessing the technology. For example, is the firm developing it, is itwhite-labeled/licensed directly, or does the firm access it through a vendor, and
ii. What the underlying technology is.
2 Identify risk events
The next step is to identify the high risk events, i.e. things that could go wrong, and how they could go wrong by listing threats and threat vectors (refer to section 5)
a.What could go wrong (i.e., identify threats) – This is a list of the potential incidents that couldmake the technology, the vendor or its output unreliable, unavailable, unsecure or ineffective.
b. How could it go wrong (i.e., identify threat vectors and actors) – This a list of the ways in whichthe potential incidents could occur. It may be helpful to categorize them based on whether they are internal and external threats, and further by accidental or intentional. Any controls designed will then depend on the source of the threat.
Firms that are starting out with this process may find it helpful to brainstorm a list of possible threats with the business line users and technology staff. This may help to identify those risk events that have a higher impact and likelihood.
3 Assess the risk of the event
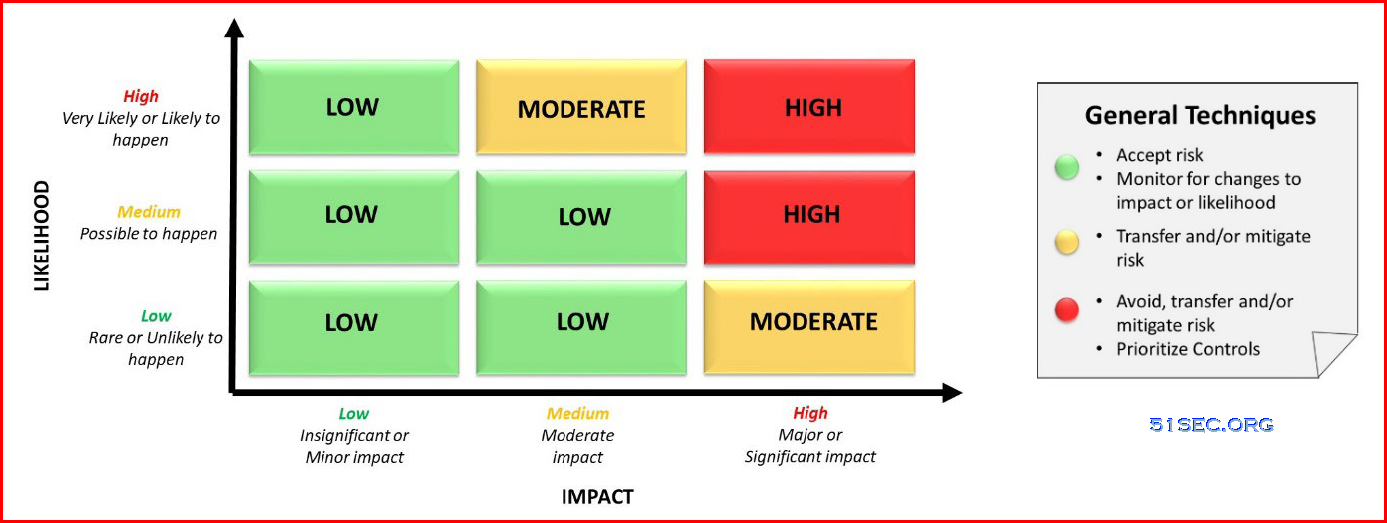
Firms should consider assessing the seriousness of risk events based on a combination of its likelihood and impact. This helps identify those risk events that need the most urgent attention. Note that this assessment will differ for each firm based on how they are structured, their business model, their stakeholders and their strategic goals.
3.1 Likelihood
When assessing the likelihood of an event occurring, it helps to base the assessment on the range of probable outcomes. For example, the likelihood of the event occurring could be:
- Rare,
- Unlikely,
- Possible,
- Likely, or
- Very Likely.
3.2 Impact
When assessing the impact of an event occurring, it is again helpful to base the assessment on the range of significance. For example, if the event were to occur, its impact could be:
- Insignificant,
- Minor,
- Moderate,
- Major, or
- Significant or Material.
Accordingly, the firm should consider who will be impacted and the nature and amount of impact:
- Who would be impacted? Who are the stakeholders that rely on the technology or its output – for example, which staff, departments or business functions, clients, regulators, service relationships, etc. would be impacted if the risk event were to occur?
- What would be the business impact?
- What would the risk event cost the firm if it were to occur? Some examples include:
- Lost revenues / customers
- Business downtime
- Financial costs to recover / respond / replace / remediate / redress
- Lost reputation
- Legal or contractual liability (e.g., because of missed deadlines or inability to meet service delivery obligations)
- Compliance and regulatory liability
4 Design and implement controls to manage risk events
Once the likelihood and impact of a risk event have been determined, the next step would be to sort them in descending order, from those events that have the highest likelihood and highest impact to those assessed as having the lowest likelihood and lowest impact. Accordingly, controls to manage the risk events would be prioritized such that:
a.Risk events with a combined assessment of high likelihood and high impact, which are the high technology risks to the firm, would be the key area of focus to design and implement sufficient and appropriate controls to manage these risk events.
b.Those risk events with a combined assessment of low likelihood and low impact are given the least attention and resources. There may be no need to focus on controls other than to ensure that their assessment of likelihood and impact is accurate and does not increase.
For each of these events, the general technique that firms should consider applying to manage risks is to avoid, accept, transfer or mitigate risk.
Avoid This technique advocates avoiding or getting rid of the technology if the likelihood of an event is high or possible and its impact is significant or material. Keep in mind that eliminating technology that has been fully implemented or has been in use for a while may be difficult and expensive. In such cases, “Accept” may be a better alternative..
Accept This technique advises firms to leave it alone or do nothing. This is a viable option where the firm’s assessment of the risk of the event is determined to be rare or unlikely to occur, and of insignificant or minor impact.
Transfer This technique involves sharing, transferring or offsetting the risk to another party. Examples of methods used to transfer risk are through insurance and outsourcing relationships. Note that
10
there are costs associated with transferring the risk and which, by itself, may not be sufficient. Certain risks like regulatory, compliance, legal and reputational risk may not be transferrable.
Mitigate This technique involves the firm designing and implementing general and specific controls to reduce the likelihood and impact of a risk event occurring. For areas where acceptance, avoidance and transference of risks is not sufficient or possible, controls need to be implemented to manage the specific higher risk event.
4.1 Risk Management Matrix
While there are several methods available depending on the size of the organization and number of business lines, in general, the following matrix demonstrates how a specific risk event can be managed.
5 Review and update the risk register
Firms should consider compiling the list of all risk events, the risk assessment, and the controls in a document or a “risk register” and making sure that the risk register is regularly reviewed and updated. The frequency of the review would depend on the firm’s business model, characteristics and whether significant changes to IT have been introduced.
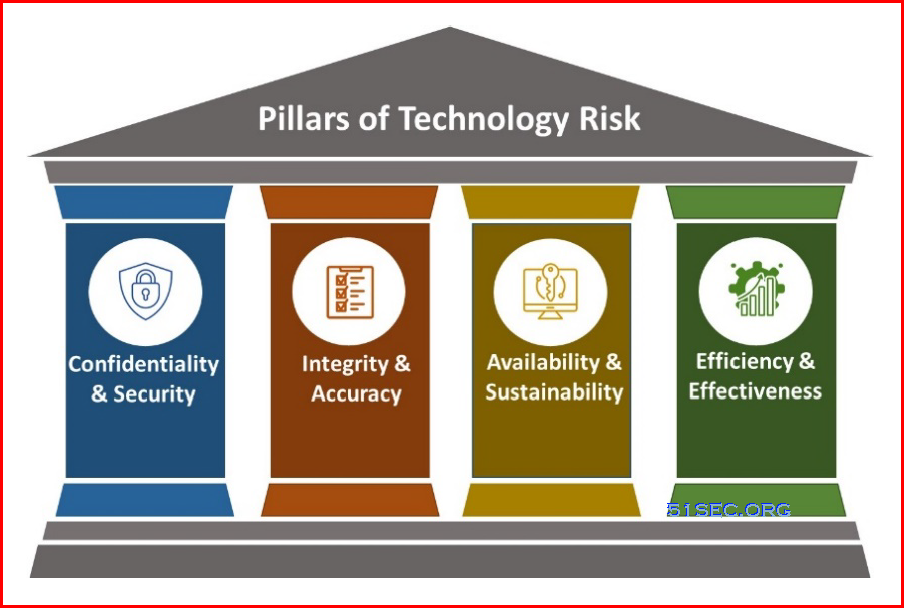
Principles of Technology Risk
When implementing a technology risk management plan and thinking about risk events, it is important to understand the principles of technology risk.
Accordingly, the four pillars of technology risk to consider are confidentiality and security, integrity and accuracy, availability and sustainability, and efficiency and effectiveness.
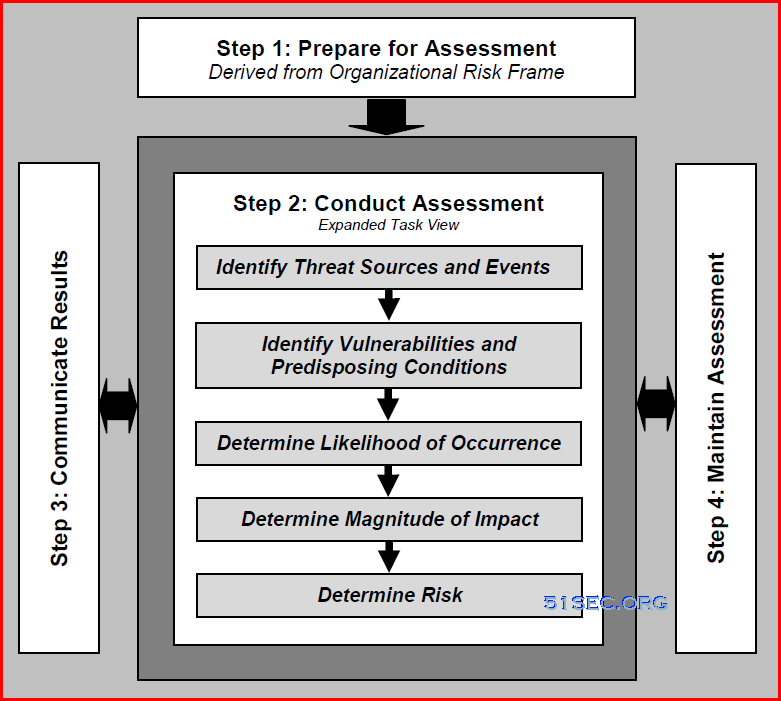 |
| NIST 800-30: Risk Assessment Process |
NIST Introductory Course: https://csrc.nist.gov/Projects/risk-management/rmf-course