This post is a continuous post from previous one Barracuda CloudGen Firewall F12 Initial Configuration Lab.
In this post, I am gonna show you how to configure WAN / LAN interfaces, how to create your own forwarding access rule, plus Destination NAT rule.
Related post:
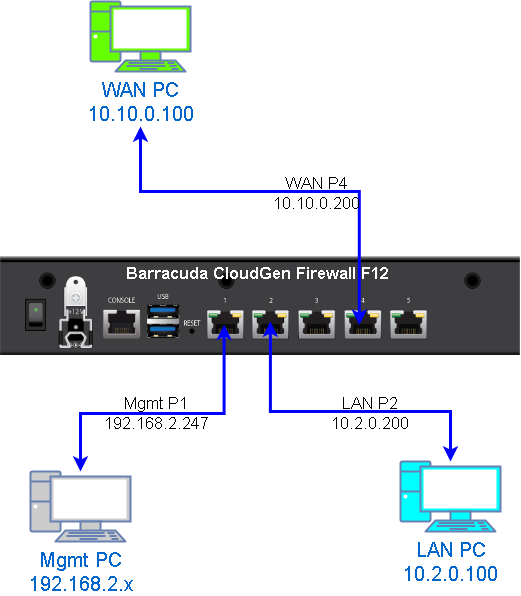
Topology
Configure Interfaces
- LAN – Port 2
- WAN – Port 4
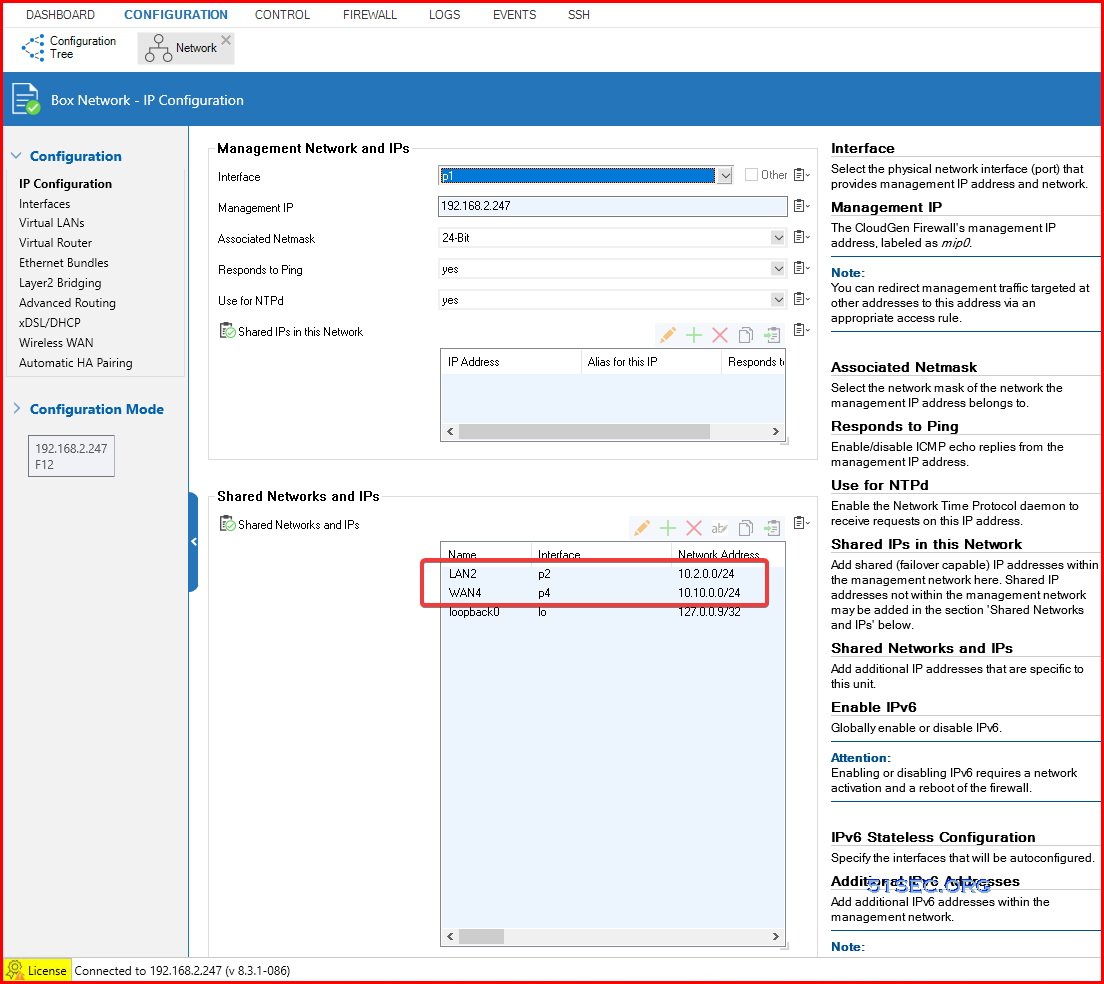
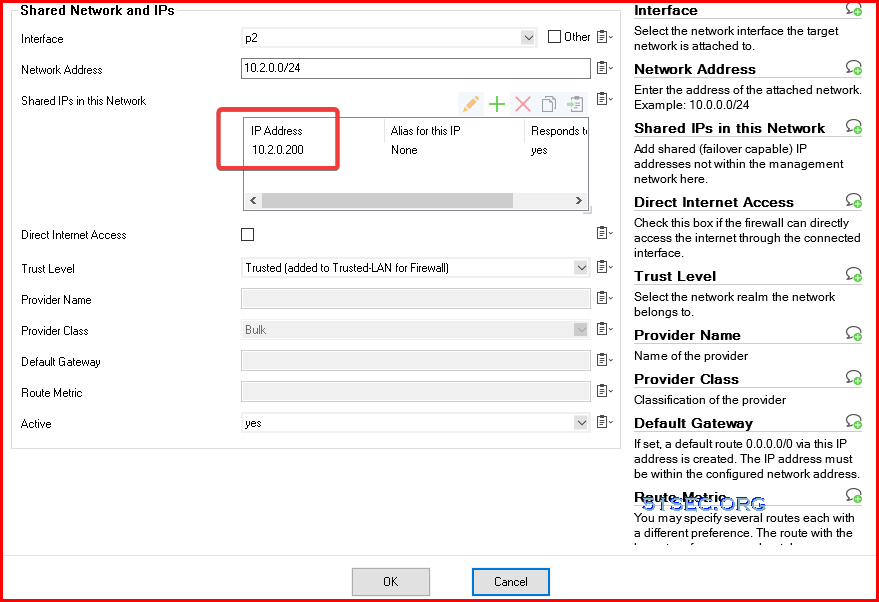
Go to Configuration – IP Configuration – Shared Networks and IPs:
Firewall Rule Settings
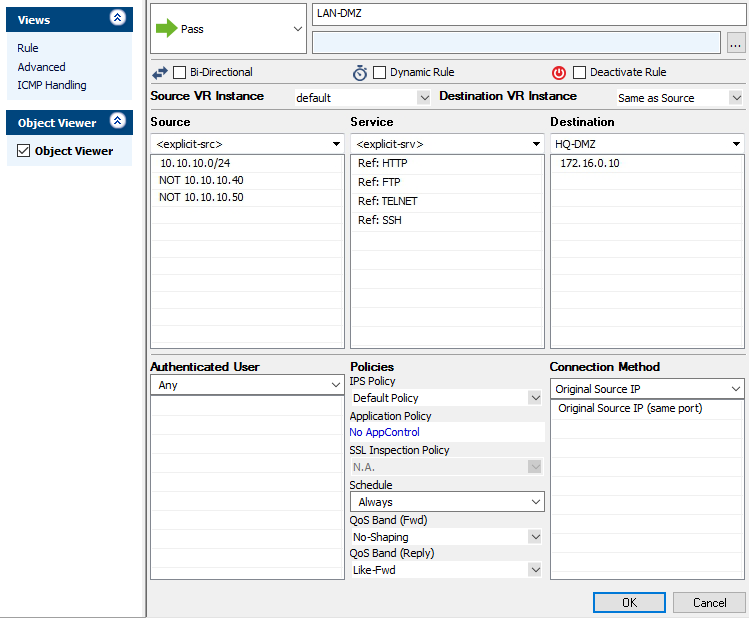
Traffic Criteria
|
Setting |
Description |
|
Bi-Directional |
If the rule must |
|
Source |
The source IP addresses of the traffic. |
|
Service |
The IP protocol used |
|
Destination |
The destination IP addresses/netmask of the traffic. |
|
Authenticated User |
The the Name column in the rule overview window. |
Rule Activation
|
Setting |
Description |
|
Dynamic Rule |
If the rule must |
|
Deactivate Rule |
To deactivate the rule, select To hide inactive rules in the rule set, click the Show/Hide Inactive Rules icon |
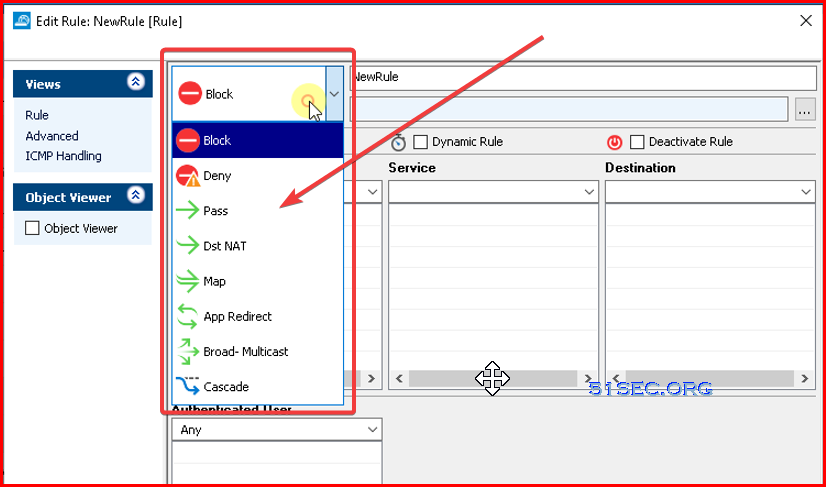
Action and Connection
- Block
- Deny
- Pass
- DST NAT
- MAP
- App Redirect
- Broad-Multicast
- Cascade
|
Action |
Description |
|
Block |
Ignores the traffic and does not answer any matching packets. |
|
Deny |
Dismisses traffic and sends the following: • TCP-RST (for TCP requests) • ICMP Port Unreachable (for UDP requests) • ICMP Denied |
|
Pass |
Passes the |
|
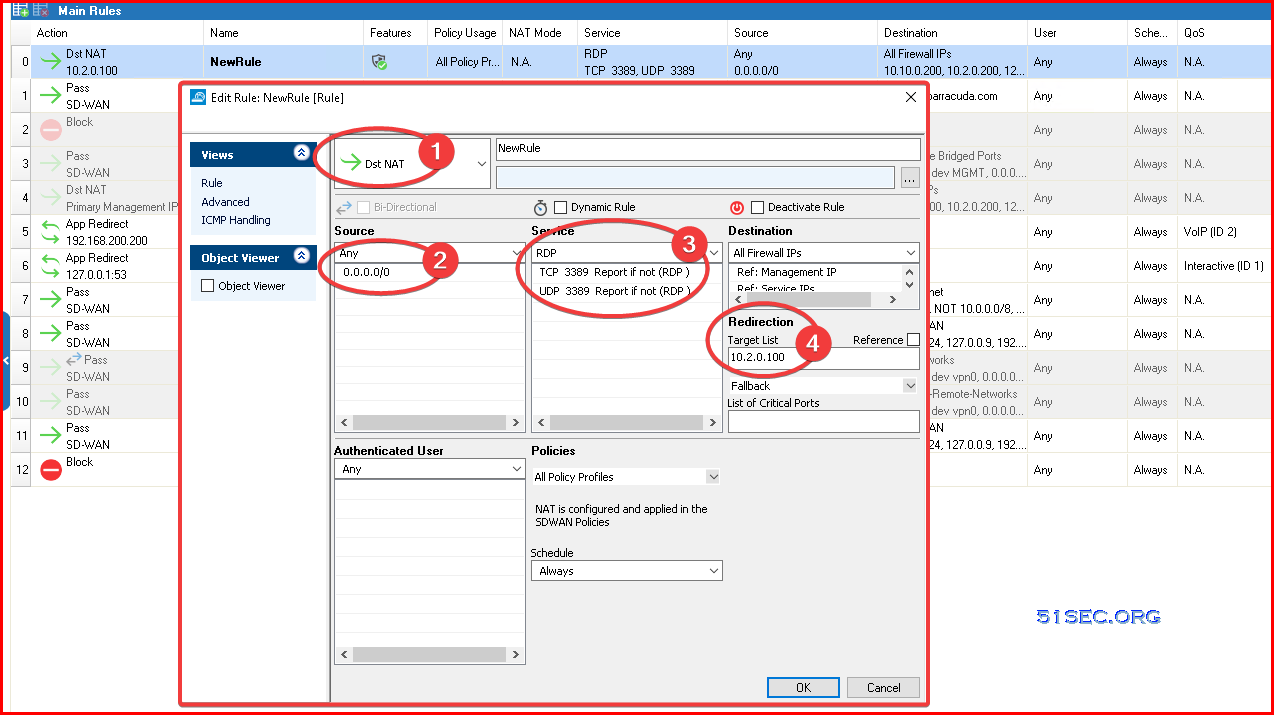
Dst NAT |
Rewrites |
|
Map |
Maps one For this |
|
App Redirect |
Redirects the
Advanced parameters and timeouts of this type |
|
Broad Multicast |
Propagates the traffic to multiple interfaces. This action is only needed |
|
Cascade |
Specifies that the traffic |
|
Cascade Back |
If the traffic does not match any rules in a rule subset specified by a Cascade rule, use this action |
|
Execute |
The traffic is piped into the STanDard IN (STDIN) of a program |
Depending on the Action of the rule, you can select a Connection
Method that specifies how the source,
destination, or service of the traffic is manipulated as it passes the Barracuda
NG Firewall. This setting typically
specifies the outgoing source IP address for address translation. The following Connection Method options are available:
|
Connection Method |
Description |
|
<explicit-conn> |
Lets you define the IP address |
|
Dynamic Scr NAT |
Performs |
|
Loopback |
Performs source |
|
No Src NAT |
No source NAT is |
|
Source |
Performs source NAT with the IP address of the specified |
|
Source NAT with VIP |
Performs source |
|
Src NAT 1st Server |
Performs |
|
Src NAT 2nd Server |
Performs |
Traffic Modification and Inspection
These settings specify if the traffic
is modified or inspected:
|
Setting |
Description |
|
Redirect Target |
This setting |
|
|
You can select |
|
|
• |
|
|
IPS Policy – The traffic is inspected by the IPS engine according to the selected |
|
|
IPS policy. |
|
|
• |
|
|
Application Policy – The traffic is inspected according to the selected application |
|
|
policy. For more information, see |
|
Policy |
• |
|
|
Time Objects – If Dynamic |
|
|
• |
|
|
QoS Band (Fwd) – |
|
|
selected QoS Band. For more information, |
|
|
• |
|
|
QoS Band (Reply) – Traffic in the reverse direction is handled according to the |
|
|
selected QoS Band. |
Configure Pass Forwarding Firewall Rule
Configure Destination NAT Firewall Rule
A Dst NAT access rule redirects traffic that is sent to an external IP address to a destination in the internal network. The following example shows a Dst NAT rule allowing HTTP and HTTPS access from the Internet to a server in the DMZ (172.16.0.10). The redirect target can be a single IP address or hostname, or a network object. Hostnames and IP addresses can be appended with a port number to redirect the traffic to a different port.
Note: https://campus.barracuda.com/product/cloudgenfirewall/doc/79462926/how-to-create-a-destination-nat-access-rule/
Video