This post summarizes how we can use Microsoft 365 to modernize our IT security.
If you are doing it correctly, Microsoft 365 could be your coolest and most practical and cost effective ($20/user/month) IT security and management systems
This is part 2.
- IT Security Modernization with Microsoft 365 – Part 1
- IT Security Modernization with Microsoft 365 – Part 2
Microsoft 365 Disaster Recovery and Business Continuity
Traditional ways:
- Weak/Untested or Nothing
- 3rd party service
Modernized ways:
- Microsoft 365 is 100% cloud
- Disaster Recovery is free
- Business Continuity is free
- Managed by Microsoft
- Geographically redundant datacenters
- 99.9% uptime SLA
Phone system business continuity
Traditional ways:
- On-Premise Phone system
- 3rd party hosted non-integrated phone system
Modernized ways:
- Microsoft Teams Phone System
- Complete Business Continuity
- Managed by Microsoft
- Geographically redundant datacenters
- 99.9% uptime SLA
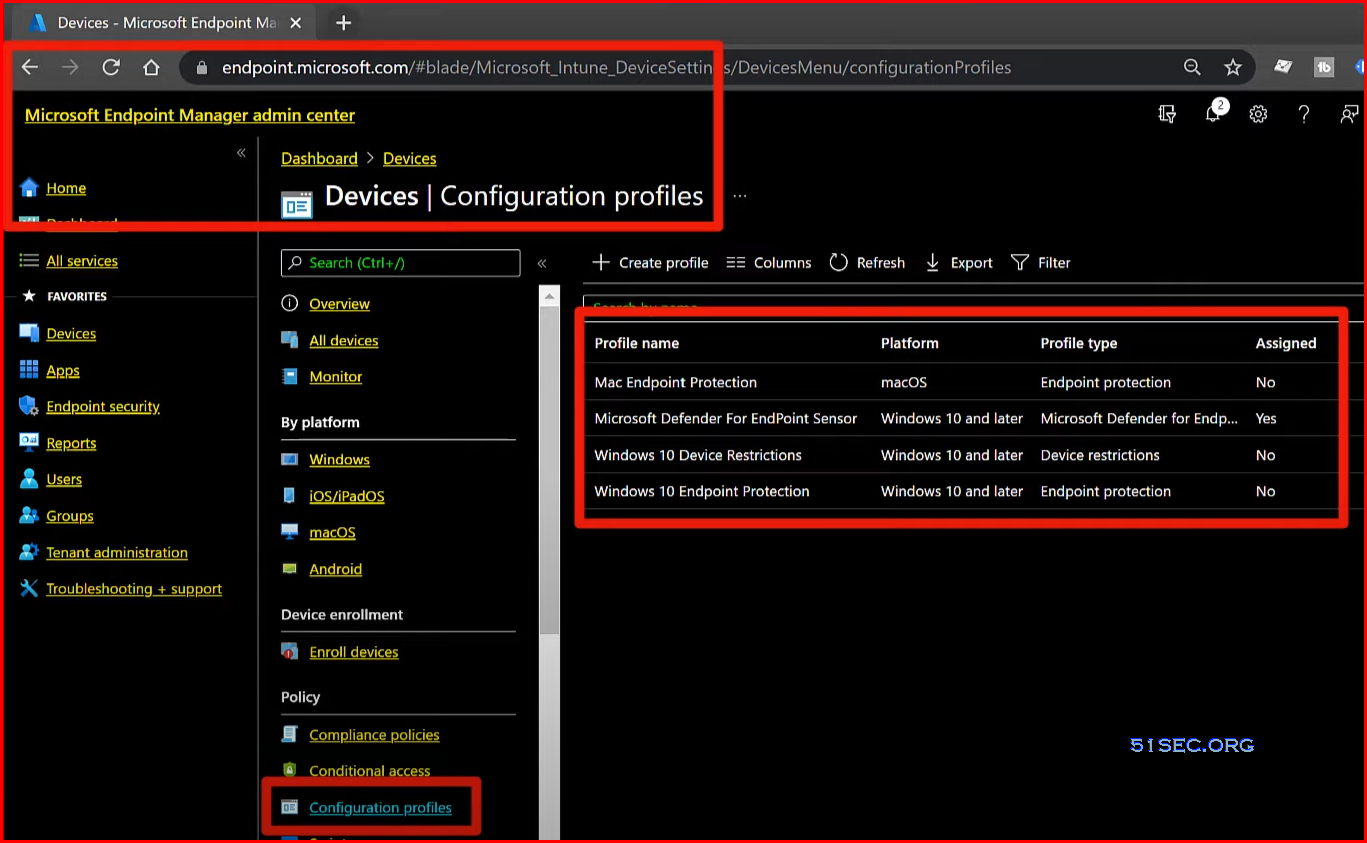
Microsoft 365 Computer Setups and Group Policies | Microsoft Endpoint Manager (formerly Microsoft Intune) Configuration Policies
Traditional ways:
- Manual end-user computer configuration
- Image-based end-user computer configuration
- Windows server AD Group policies
Modernized wayssss:
- Microsoft Endpoint Manager (intune)
- Configuration profiles
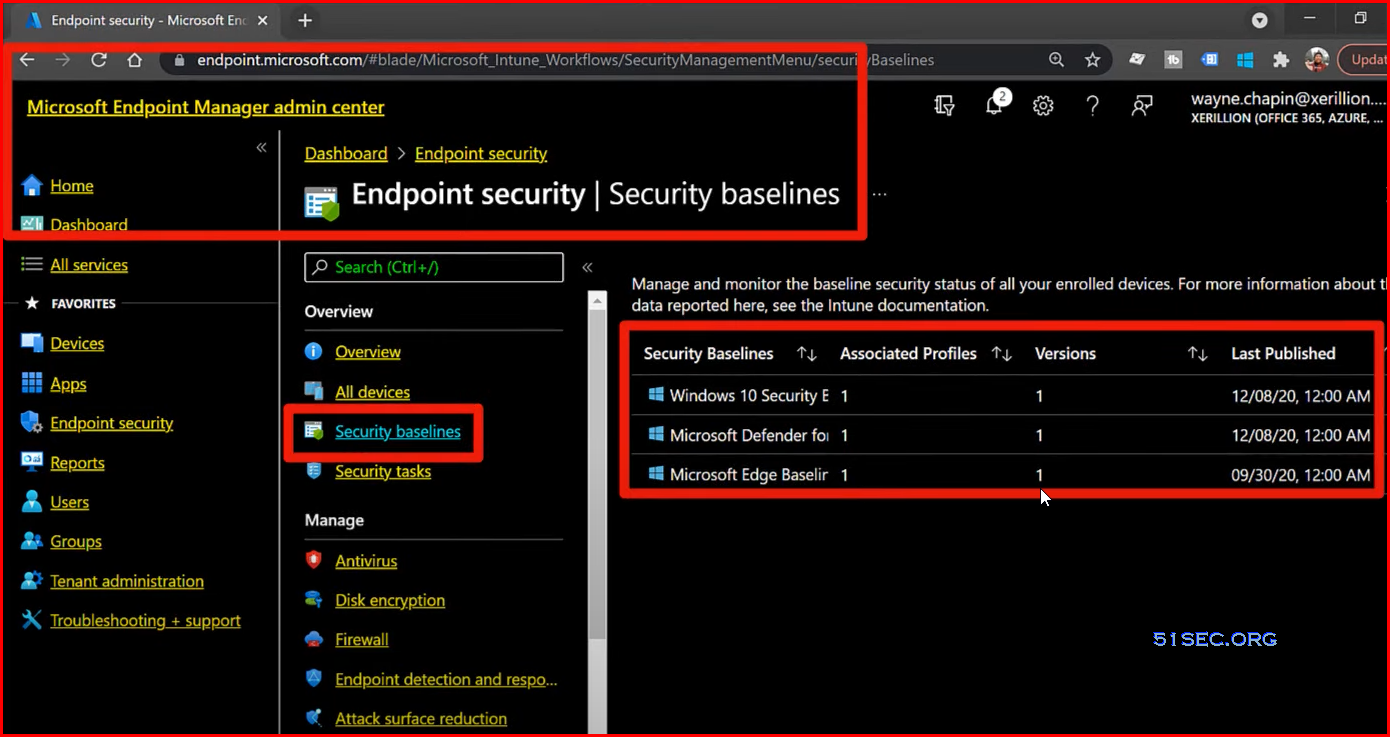
Microsoft Endpoint Manager Advanced: Security Baselines
Optimized Modernization of Endpoint Manager:
- Security Baselines
Microsoft Defender Antivirus
Traditional ways:
- 3rd party antivirus
Modernized ways:
- Microsoft Defender Antivirus – included with Windows 10
Microsoft Defender for Endpoint (advanced antivirus)
Optimized modernization:
- Microsoft Defender for endpoint – behavioral based monitoring, blocking and containment
- Best practice from Microsoft Baseline template is available
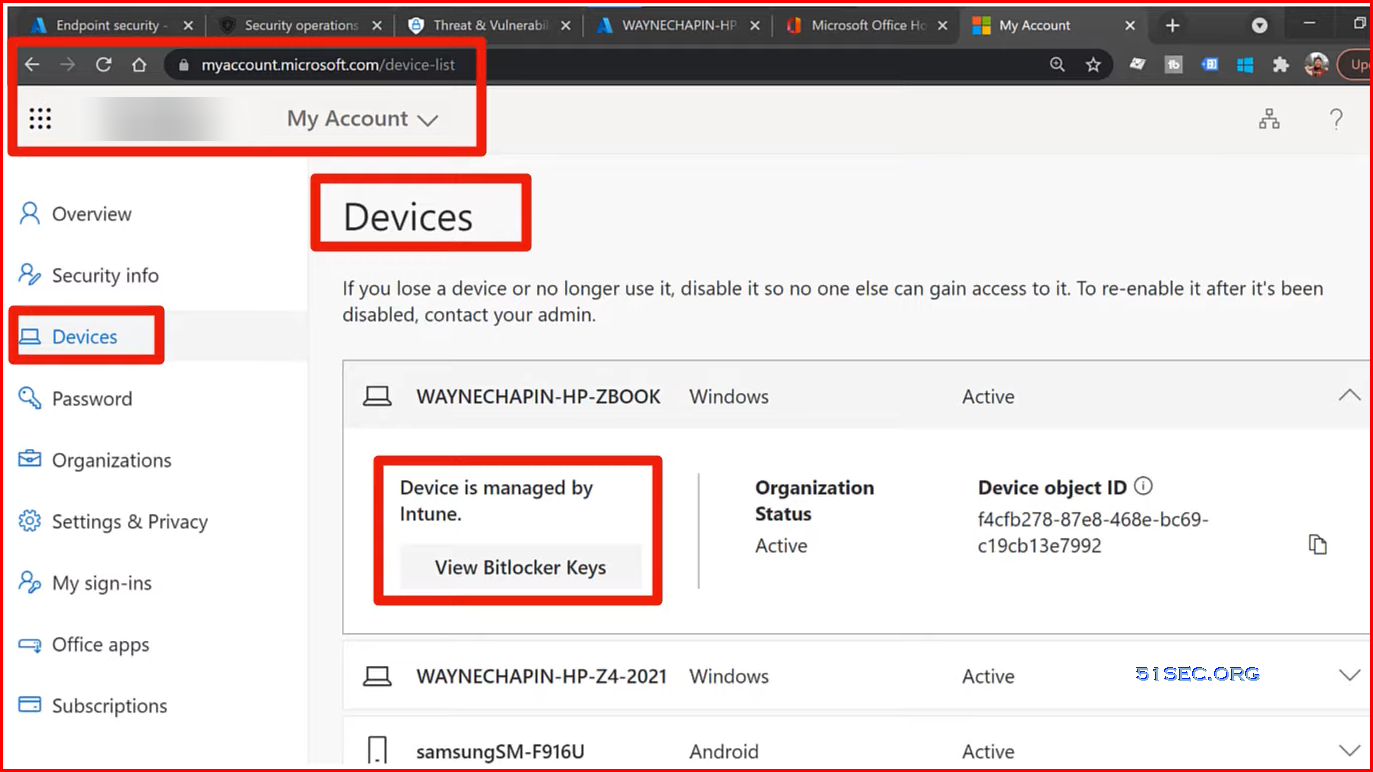
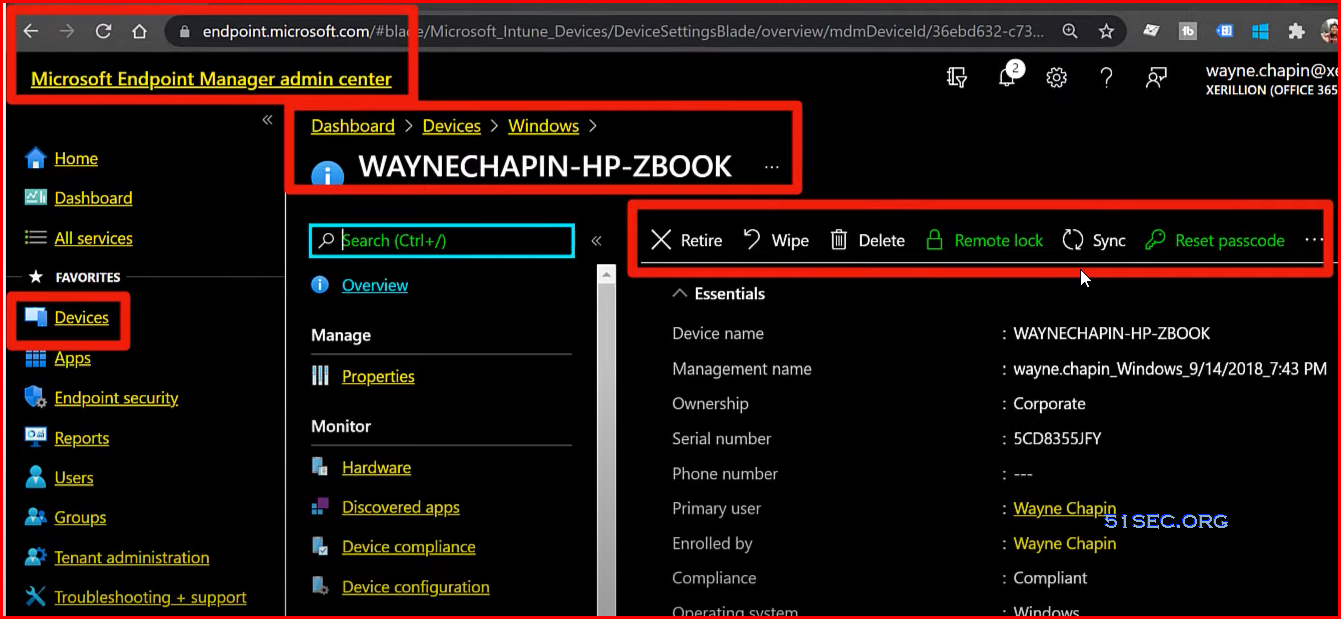
Microsoft 365 lost or stolen computer protection | Bitlocker disk encryption | Remote Wipe | Remote Lock
Traditional ways:
- Nothing
Modernized ways:
- Microsoft Bitlocker included with Win10+
- Azure AD Bitlocker Recovery Key Sync (Azure AD P1)
- Microsoft Endpoint Manager Remote Wipe
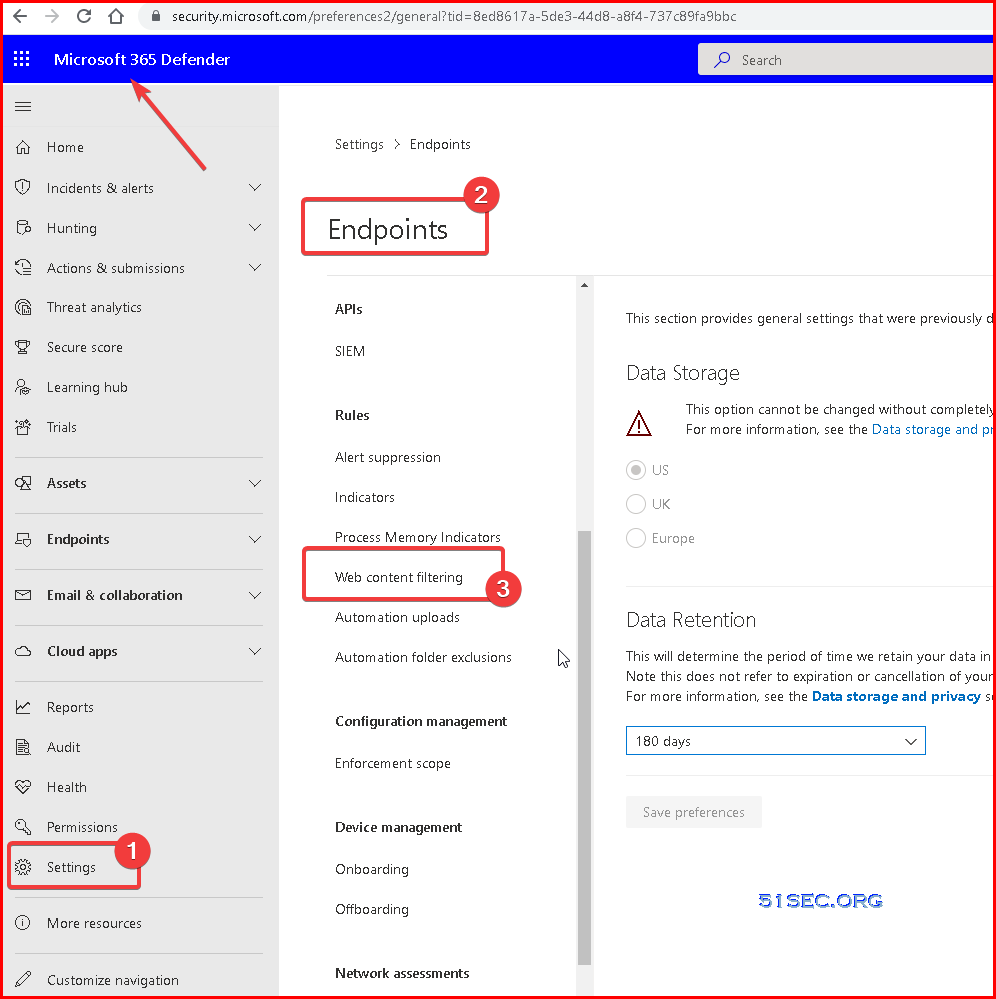
Microsoft 365 web browsing protection | Web threat protection | Web content filtering
Traditional ways:
- Nothing
Modernized ways:
- Microsoft 365 Defender for Endpoint
- Web Threat Protection
- Web Content Filtering
Web threat protection: Advanced | Microsoft Edge standardization | Microsoft Endpoint Manager Security Defaults for Microsoft Edge
Traditional ways:
- Whatever web browser the user wants
- No web browsing security controls at all
Modernized ways:
- Standardize on Microsoft Edge
- Web App Virtual Containers
- Microsoft Defender for endpoint
- Microsoft Endpoint Manager Security Defaults for Microsoft Edge (Baseline template)
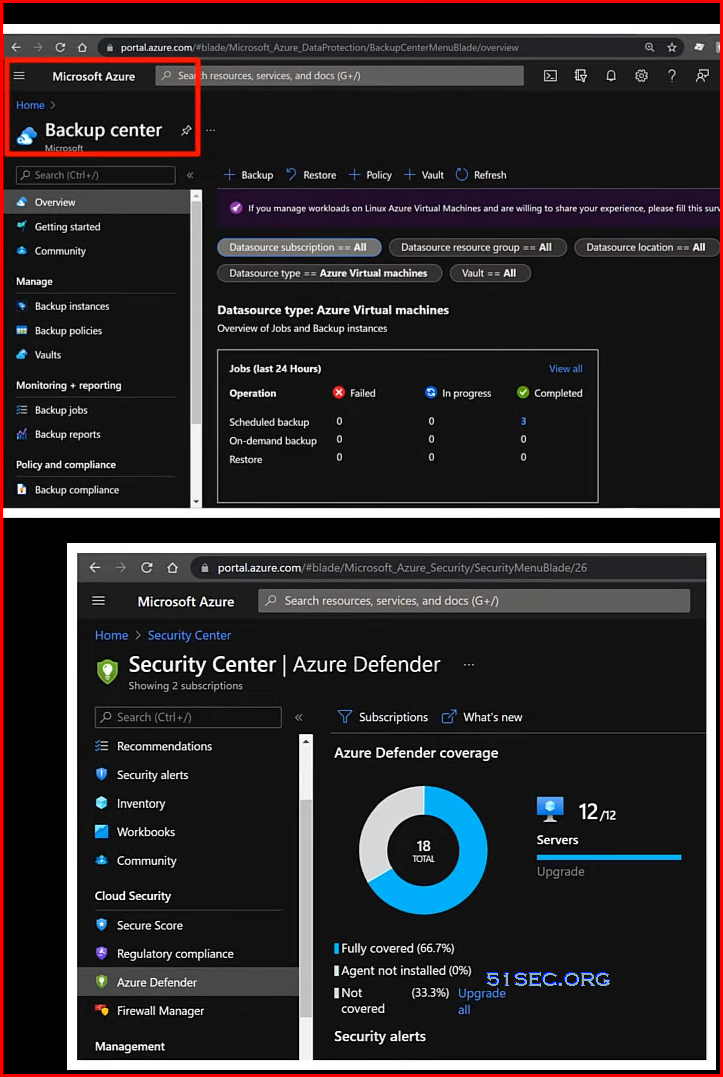
Legacy Server backup and security with Microsoft Azure | Azure Backup | Azure Defender
Usually involving a MS SQL Server.
Traditional ways:
- On-Premise virtual or physical servers
- Server backup and disaster recovery
- No antivirus or 3rd party antivirus
Migrate to Modernized ways:
- Virtual servers in an Azure virtual network
- Azure Backup
- Azure Defender
- Disaster recovery included for free
- 99.9% uptime SLA
- Accessed through
- VPN
- Windows Virtual Desktop
Microsoft 365 VPN
Traditional ways:
- On-Premise firewall appliance hosting vpn
Modernized ways with Microsoft 365
- No VPN needed
- Data is 100% in Microsoft 365 cloud
- All data is encrypted in transit and at rest
- Azure Active Directory is your firewall (Identity protection)
- Only need to consider your endpoint device encryption, enable/configure conditional access
Microsoft 365 firewall
Traditional ways:
- Pricey On-Premise firewall appliance
- 1-3 year license/support renewals
- 5 year hardware refreshes
Modernized ways with Microsoft 365
- Basic NAT firewall or ISP router
- Your IT services are 100% cloud
- Cybercriminals don’t know about your LAN
- Azure Active Directory is your firewall (Identity protection)
Microsoft 365 hardware refreshes
Traditional ways:
- 5 year hardware refresh cycles
- 6th year warranty stretch
Modernized ways with Microsoft 365
- No hardware refreshes forever
- Only left in the on-premise
- Basic firewall
- switches
- wireless access points
- network printers
Microsoft 365 Security Extras
Following features will be considered extras.
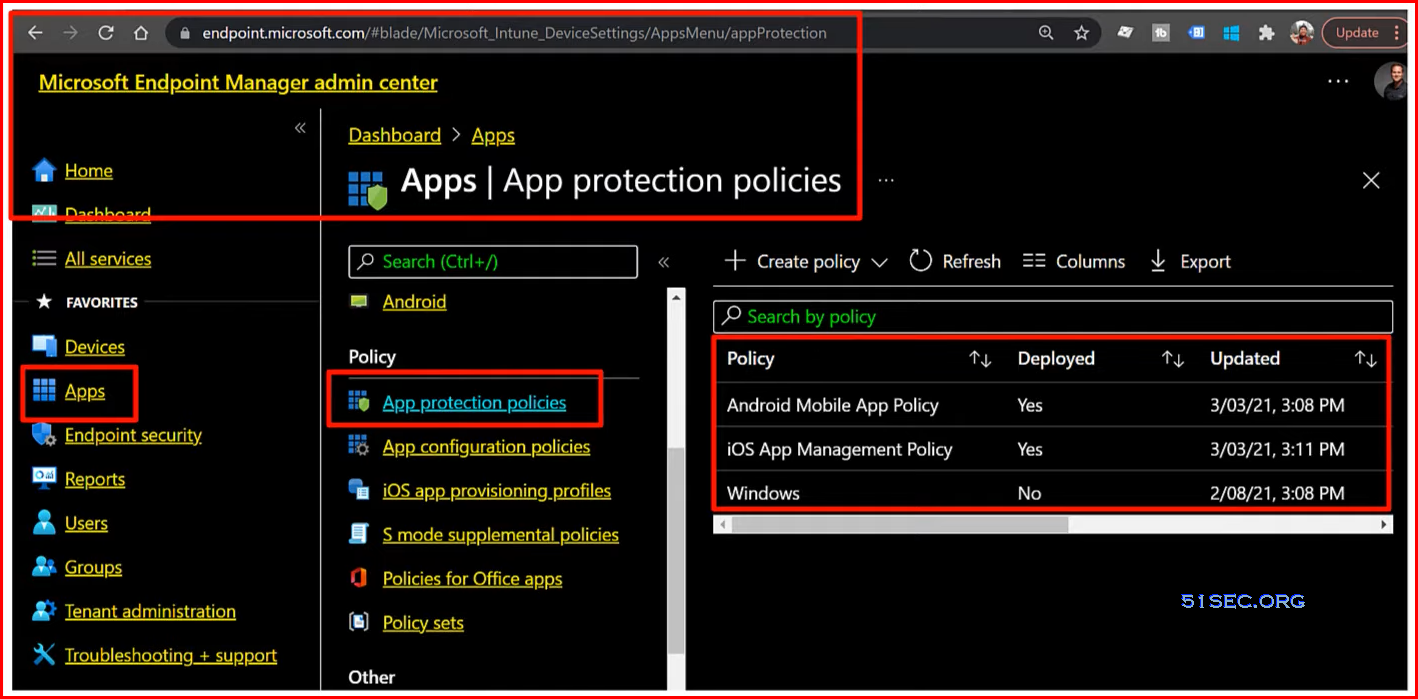
Control company data on employee personal devices | Microsoft Endpoint Manager App Protection Policies
Traditional ways:
- Company emails and files sync’d to employee personal cell phones
- No control over where company email and files copied
- No data loss prevention control
Modernized ways with Microsoft 365
- Microsoft Endpoint Manager App Protection Policies
- Control security with the mobile app, not the employee’s personal cell phone
- Control copy/sync/share on mobile app
- Remote Wipe
- Auto-Wipe
Microsoft 365 Single Sign On
Traditional ways:
- Employees juggling multiple login accounts
- Azure AD
- Windows Server AD
- Financial Web App
- Sales Web APP
- Operations Web APP
- Accounts use company email address and same/similar passwords
- Security risk
Modernized ways with Microsoft 365
- Azure Active Directory Single Sign-On
- Azure AD account used as the single identity to access all company cloud systems
- One identity to create when an employee starts
- One identity to disable when an employee leaves
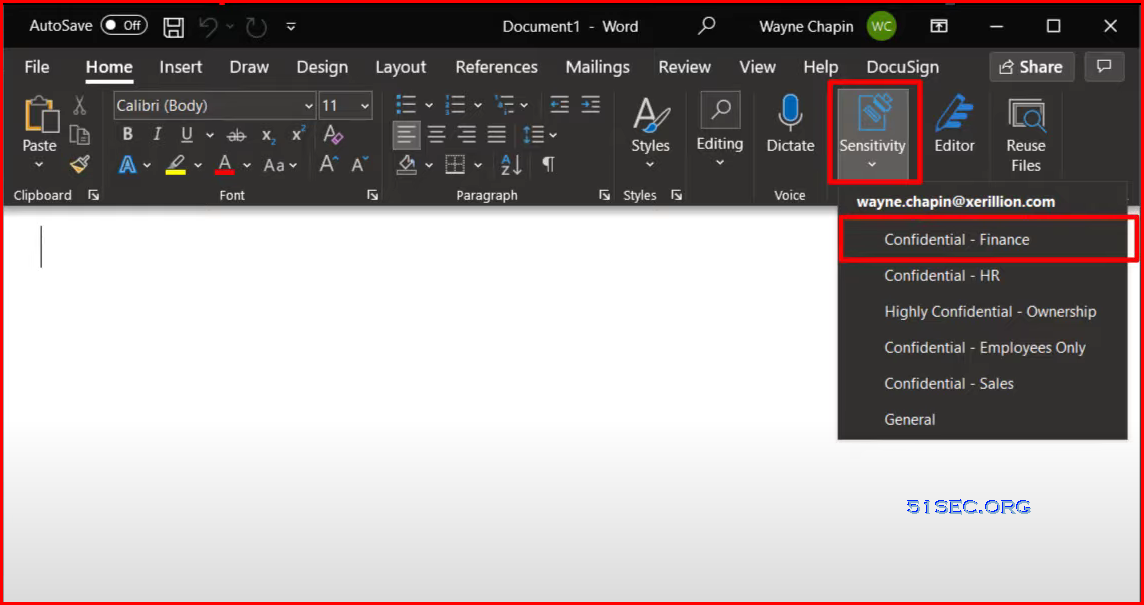
Securing files and emails anywhere in the world | Microsoft 365 Sensitivity Labels
Traditional ways:
- Folder-based security controls
- Security applied at the folder level
- File/email has no protection once it is taken out of the folder
Modernized ways with Microsoft 365
- Microsoft 365 Sensitivity Labels
- ability to apply a security group directly to a file or email
- Security stays with the file or email no matter where it goes or who has it.
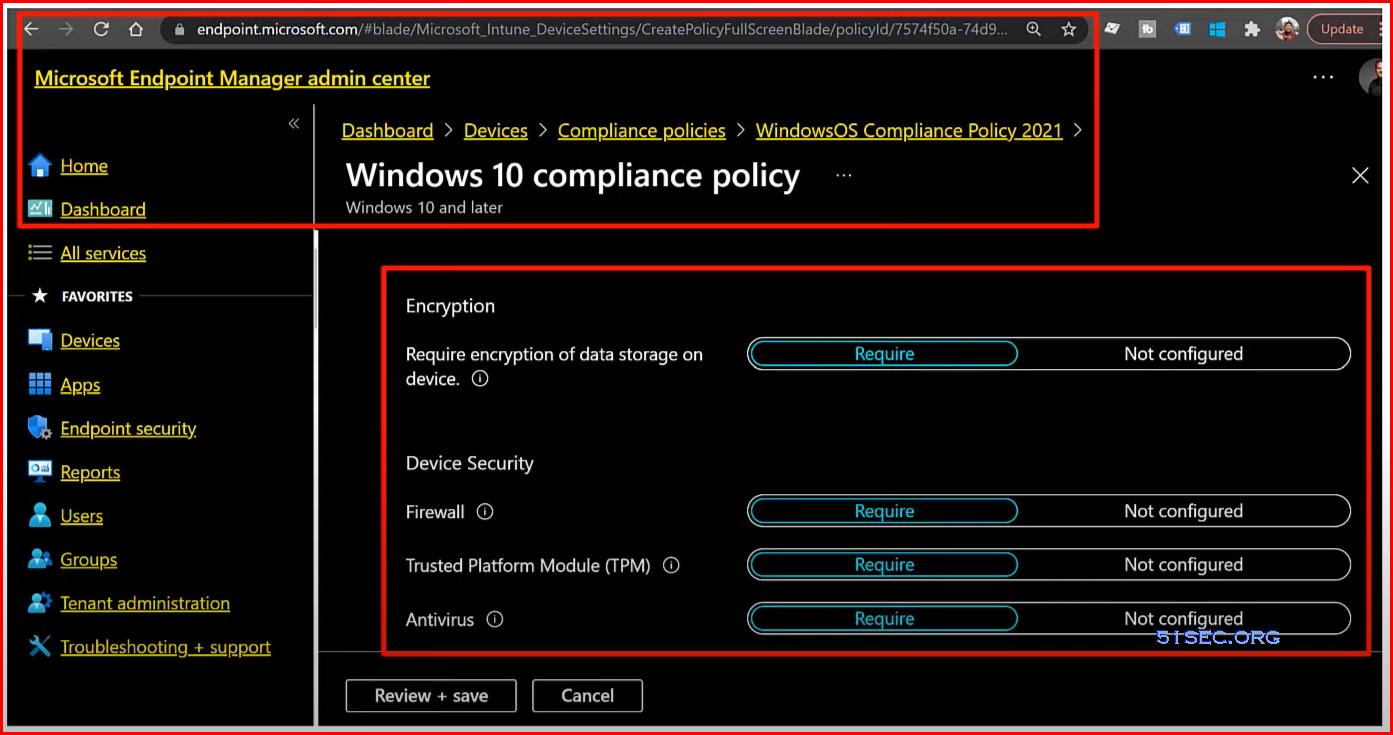
Microsoft 365 Device Compliance Policies
Traditional ways:
- Connect to Microsoft 365 without regard to device security
Modernized ways with Microsoft 365
- Microsoft Endpoint Manager
- Device Compliance Policies – Users’ devices must meet our security requirements
Maintaining Microsoft 365 cloud services
Traditional ways:
- IT Manager / Director manage hardware and software updates
- Login to servers to check and remediate IT system
- If system is running, call it good?
Modernized ways with Microsoft 365
- Microsoft manages hardware and software updates
- You login to portals to check and remediate IT system
- You configure processes around alerts and auto-remediation
Microsoft 365 Secure Score
Traditional ways:
- No objective IT security scoring metric
- No guided path
- No industry best practices checklist
Modernized ways with Microsoft 365
- Microsoft 365 Secure score
- scoring metric for your entire Microsoft 365 tenant
- Current score and score trending
- Provides prioritized technical checklist
Microsoft 365 Compliance Manager | Data Protection Baselines
Traditional ways:
- Compliance is an ambiguous goal nobody on your team has real experience with
- compliance requirements looks ridiculously bureaucratic
- No industry best practices, NIST, ISO, Fedramp, GDPR
- No guidance or integration with Microsoft 365
Modernized ways with Microsoft 365
- Microsoft 365 compliance Manager
- Data protection Baselines
- Comes with all versions of Microsoft 365
- Beyond technical implementation in M365 secure score
- Documentation, policies, procedures
- Microsoft best practices mixed with industry compliance NIST, ISO, Fedramp, GDPR
- Provides prioritized checklist
- Current score and score trending
Subscriptions and pricing
Typical setup:
Microsoft 365 Business Premium: $20/user/month (300 users) -> Enterprise version ($32/user/month)
+Microsoft 365 E5 security add-on : $12 / user / month (id protection, behavior AI learning protection)
+Microsoft Phone System : $20/user/month
Total = $52/user/month (300 user limit)