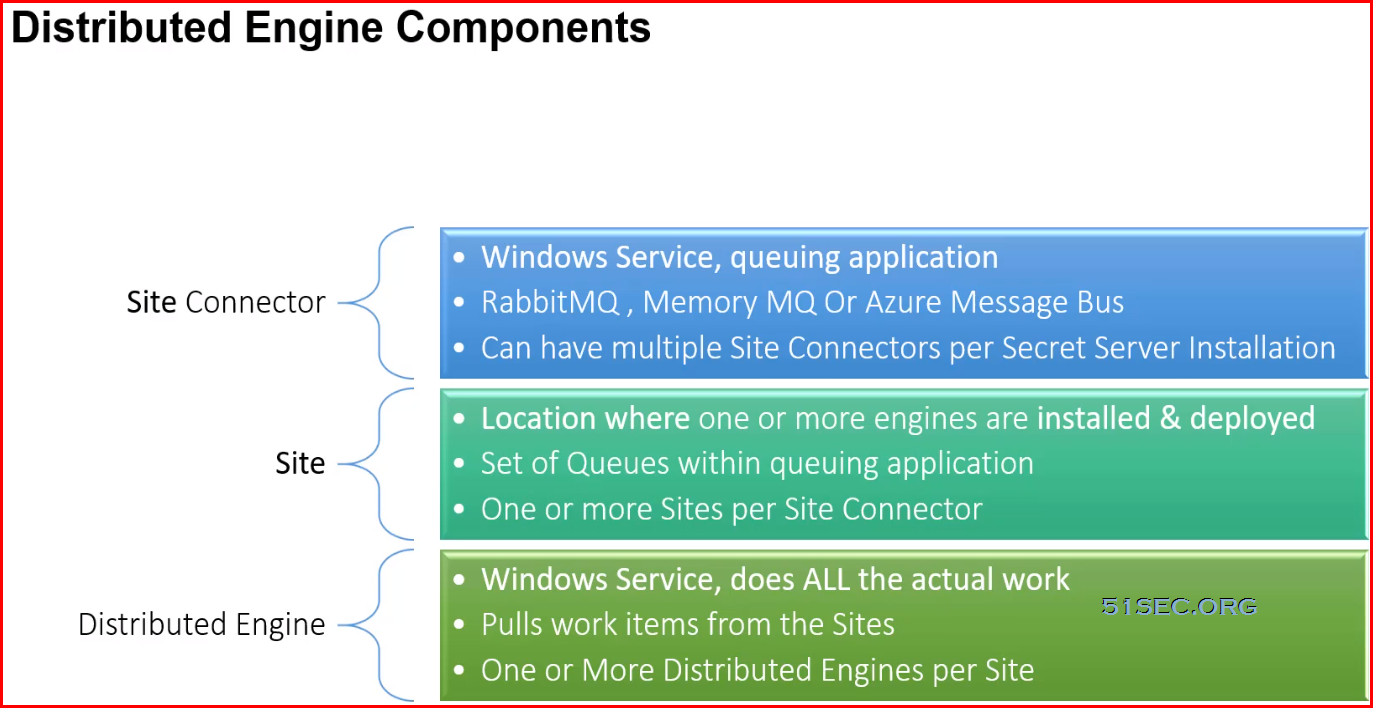
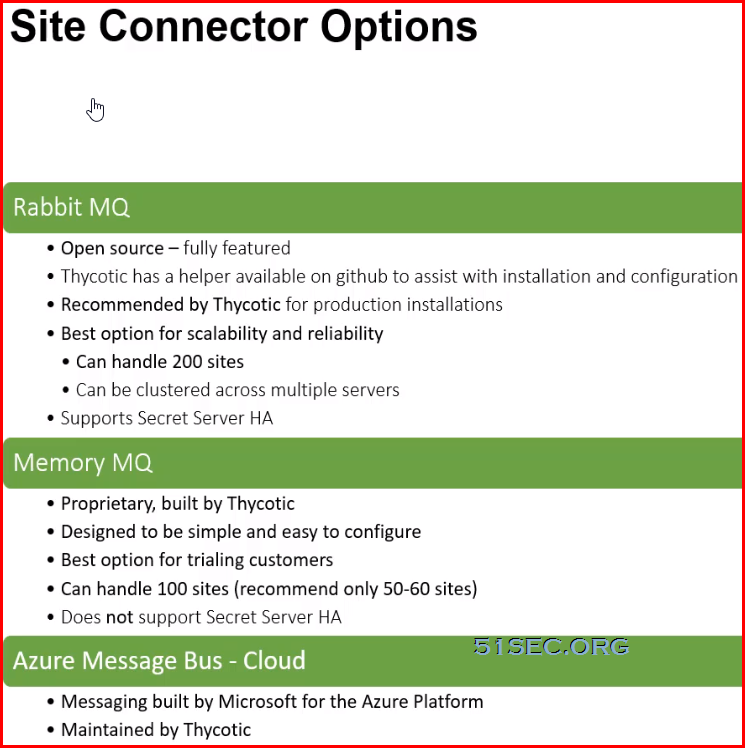
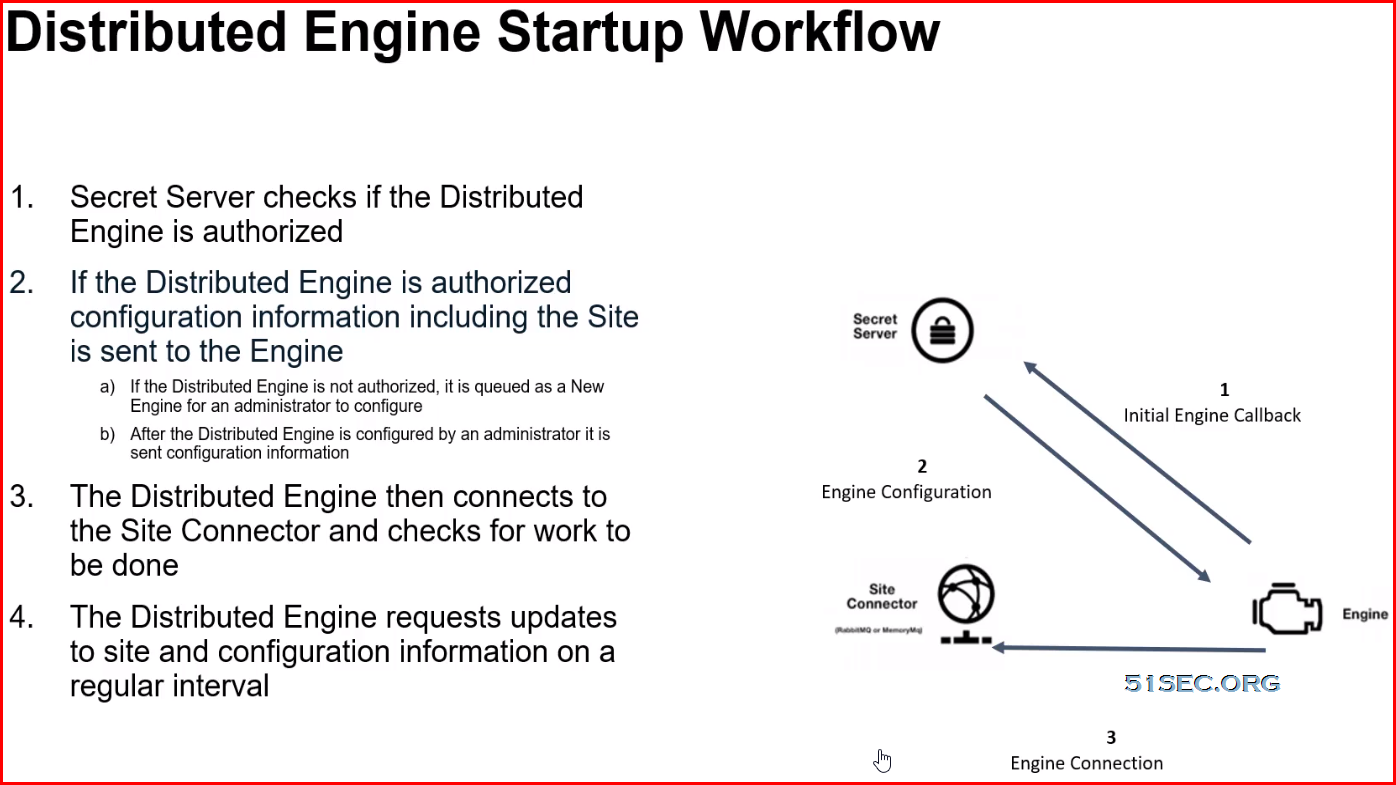
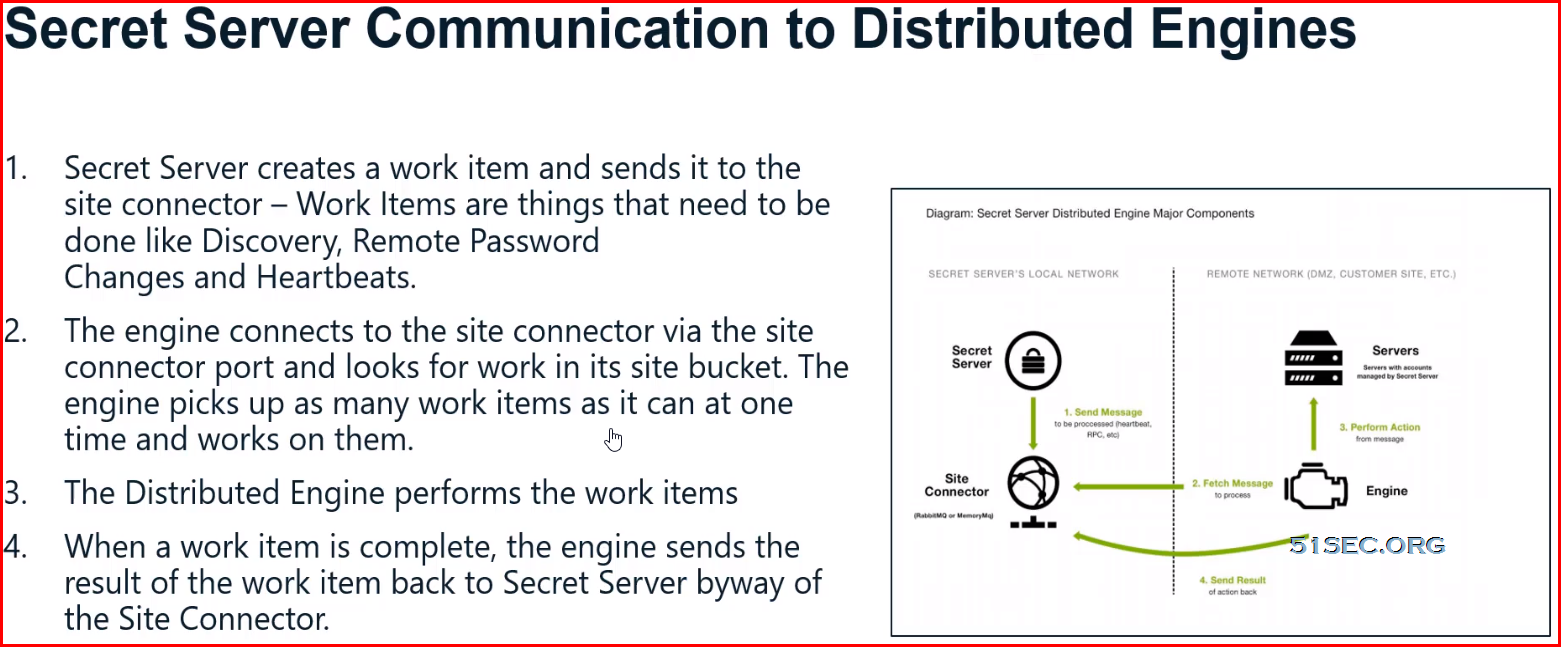
This post summarizes some Thycotic SS knowledges which considered as advanced level.
Distributed Engines provide scalability for large or distributed organizations
- Leverage Secret Server for Privileged Account Management at remote offices & locations
- Large environments (50k+ endpoints) require more processing power from Secret Server
- Organization wants to manage remote networks (private cloud or DMZ)
Distributed Engine supports:
- Discovery
- Active password rotation (on-demand & scheduled)
- Active Directory Integration
- Heartbeat
- Proxying
Unix Protection
SSH Key management
SS Unix Protection – Allowed Command Menus
• Restrict!ßommands per user or group
- On the Secret or by Policy
• Launched Sessions only have access to the menu
• Format
name = command variables
- Name
The name the user will type to execute the menu option
May not contain white space characters .
- Command
- Command sent through SSH to the remote server
- Must be a command that is accessible by the user
Variables
- Variables that are passed into the command run on the remote server
- Names are to help what is expected.
Secret Server: SSH Endpoint
• Allows access to secrets through an SSH session
- • Find existing secrets
- • View existing secrets
- • Launch an SSH æoxy session using a secret
• Uses a Linux like commands
• Eases access to secret server from Unix/Linux machine
SSH Key Dependencies
API’s and Scripting
SECRET SERVER REST API
REST API documentation for Thycotic Secret Server
- Documentation for REST API using tkarer token authentication
- Documentation tor token authentication
- Documentation for REST API using Windows integrated authentication
REGULAR EXPRESSION ARE USED THROUGHOUT THYCOTIC PRODUCTS
Secret Server
- • Remote Password Changing
- • Creating Rules in Discovery
- • Ticket Integration
- • Dependencies
- • Web Password Filler
Privilege Manager
- . Filters
- . Policies
Software Development Kit (SDK)
SDK Client Command-Line Tool
- Retrieve Secret values from Secret Server programmatically
- Integrate with scripts and build tools
- Fine-grained access control
- Secure configuration storage
- Available in Secret Server 10.4
- Supports Windows, Linux, MacOS
SDK Client Example Scenarios
• Accessing authenticated resources from within a script
• Deploying build artifacts from a CI/CD process
• Deploying credentials to client machines using a configuration management tool
• Building containers with credentials baked in
SS and Service Now Integration
Troubleshooting Basic Configurations in SS
This module will cover: Users, Groups, Roles, and Role Permissions Best Practices
User – Named account used to login to Secret Server.
Groups — Organize users to efficiently assign privileges in Secret Server
Role — Controls what a user can do within the Secret Server application.
Role Permissions — Individual permissions assigned to a Role. Without permission a role is powerless.
Troubleshooting Summary
Basic Configuration
- Roles, Groups, and Users should be reviewed regularly
- Use Event Subscriptions to alert on any changes made to Basic Configurations
- Always review default settings and confirm if they can be customized
- Using the Hybrid approach will minimize consequences if users are incorrectly synced to Secret Server
Troubleshooting Secrets and Secret Template
Troubleshooting Summary
Secrets and Secret Templates
- Secrets are created from Secret Templates
- Templates can be configured by Administrators or Template Owners
- Changes to Templates effect all Secrets leveraging the Template
- Setup event subscriptions for changes made to Templates
Troubleshooting Auditing and Reporting
Reports are on Demand or Scheduled:
• Dozens of Out-Of-The-Box Reportb
• Create Custom Reports with SQL
Reports answer a specific question — What Secrets or Folders can a user see..etc
Troubleshooting Summary
Auditing and Reporting
- By default, Secret Server does not delete any audit data
- Data deletion occurs automatically at 2:00 am EST every Sunday
- Do not configure automatic record deletion for compliance or other important data
- Unlimited Admin role doesn’t include audit data retention management
Troubleshooting Discovery
Troubleshooting Summary
Discovery
- Always review Secret Server Discovery logs for reoccurring errors
- Be aware of logs that exist outside of Secret Server such as Engine Logs
- Schedule Reports accounts that failed b or are pending an import so you can resolve issues as soon as possible
- Always review most up-to date permissions needed to perform Discovery with Secret Server
Troubleshooting Remote Password Changing
Secret Server has the ability to automatically change passwords
- Bulk on demand — When an employee is leaving the organization or a breach is detected
- On a schedule — TO meet compliance mandates or enforce security best practices
Troubleshooting Launchers
Troubleshooting Summary
Launchers
- Launchers can be customized to work with any command-line-started application
- Always confirm applications are mapped properly for all client machines that will be leveraging Custom Launchers
- Don’t forget to add the program folder in the PATH environment variable
- Each custom Launcher will have unique requirements — Review the support portal for most up to date configuration steps
Troubleshooting Session Recording
Recording and Monitoring Sessions initiated within Secret Server or from the Target System:
- Produces a screen capture (pic) every second, rolls it up into video
- Allows for real-time monitoring and creates a video audit trail
- Allows for Live messaging & session termination
Troubleshooting Summary
Session Recording and Monitoring
- Schedule Reports Session Recording Errors so you can resolve issues as soon as possible
- Always review most up-to date system requirements needed to record sessions with Secret Server
- Understand unique configuration options that can be configured within Secret Server’s configuration files
- Remember to restart IIS after making changes to Secret Server architecture components
Troubleshooting Distributed Engine
Troubleshooting Summary
Distributed Engine
- Always review Secret Server logs for reoccurring errors
- Beoware of logs that exist outside of Secret Server such as Engine Logs
- Schedule Reports that show engine status in your environment
- Always review most up-to date Roles/Features needed to use Distributed Engine in Secret Server
Troubleshooting SS Upgrading
Troubleshooting Summary
Distributed Engine
- Always review Secret Server logs for reoccurring errors
- Beaware of logs that exist outside of Secret Server such as Engine Logs
- Schedule Reports that show engine status in your environment
- Always review most up-to date Roles/Features needed to use Distributed Engine in Secret Server
References
from Blogger http://blog.51sec.org/2021/06/thycotic-secret-server-advanced.html