This post describes how to configure a Branch Office VPN (BOVPN) between WatchGuard Firebox on Prem and a Check Point device at my home which is behind my home router.
There are some configuration I found interesting which I mentioned in the following. Local network setting is confusing me although I got it working. It might be because of the specialty of Firebox
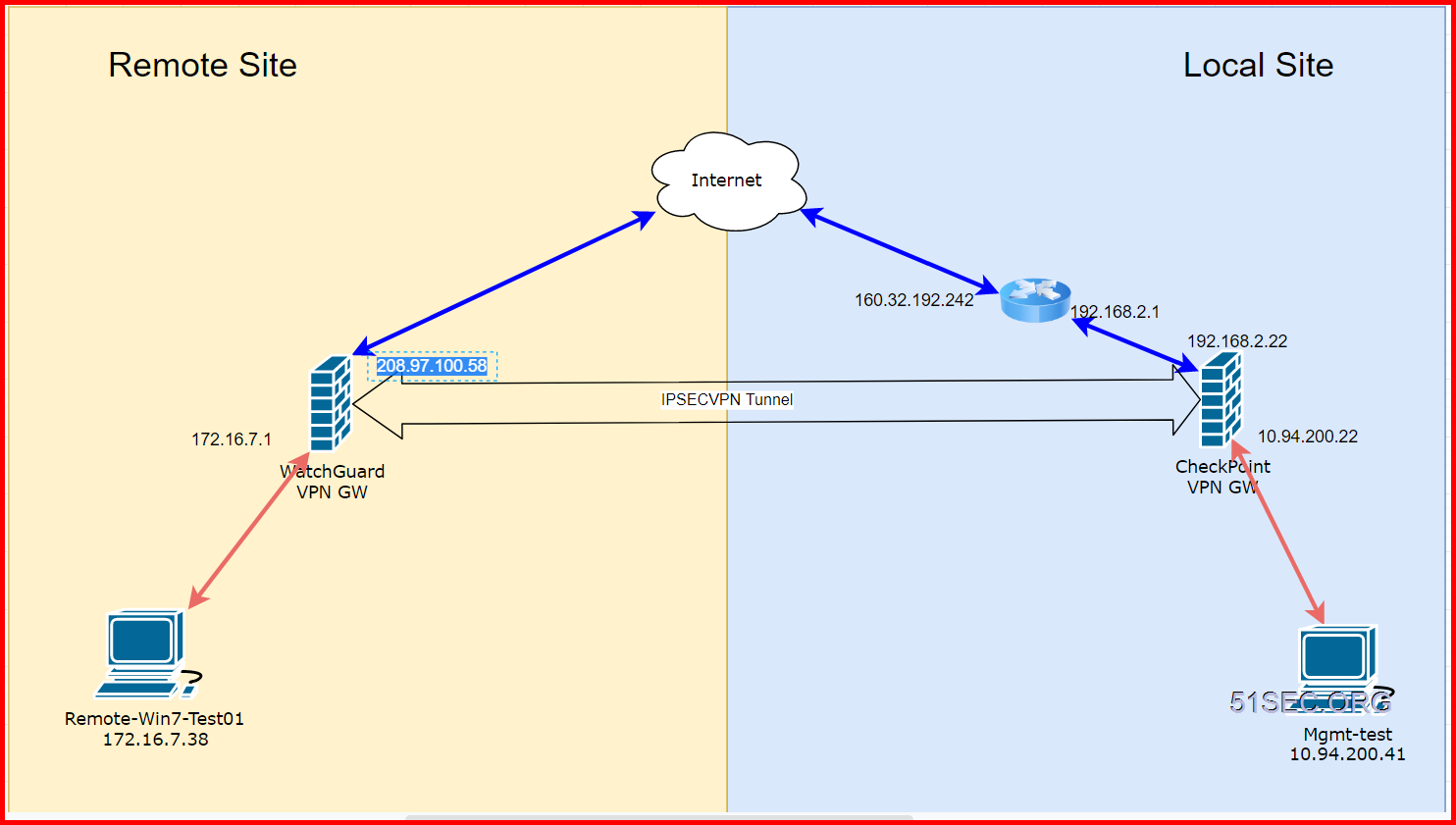
Topology
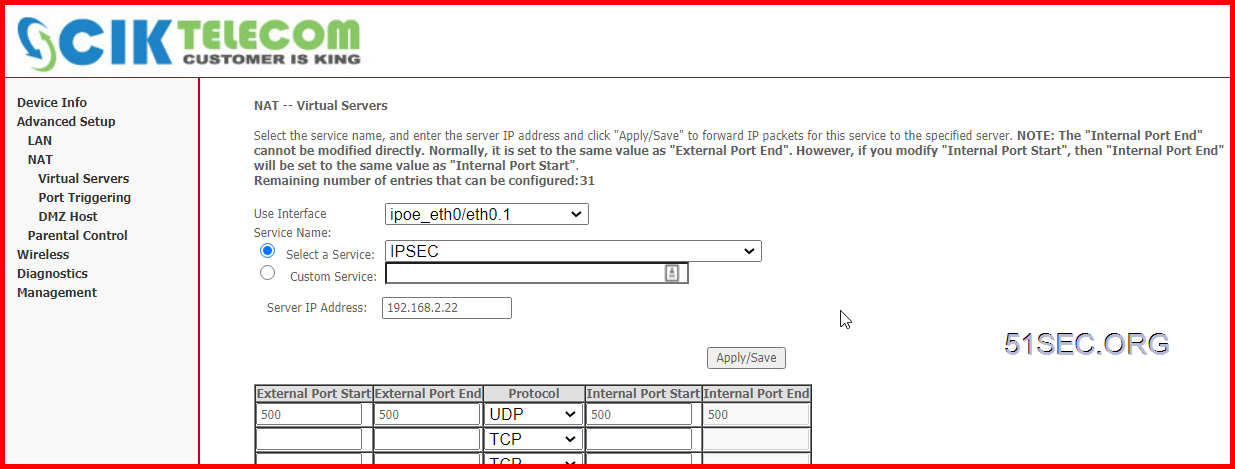
Make Sure Firewalls UDP500 Expose to Internet
UDP500 is IPSEC Protocol.
Since in local site, I am having a home router in front of Checkpoint firewall 192.168.2.22, I will have to open UDP 500 port to checkpoint firewall gateway.
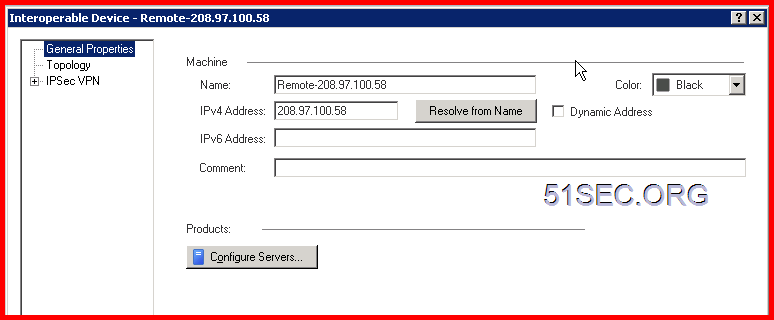
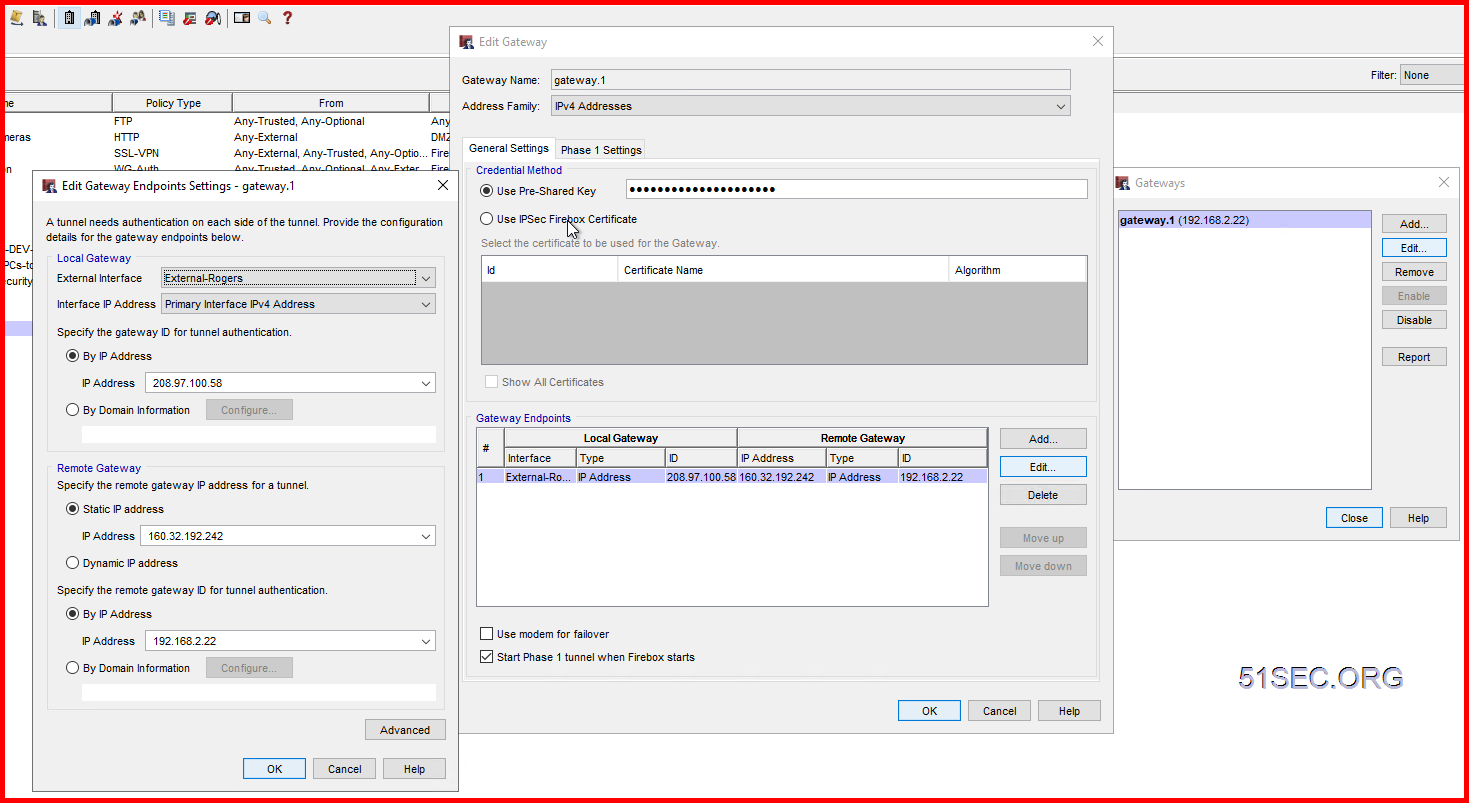
Create Gateway on each site
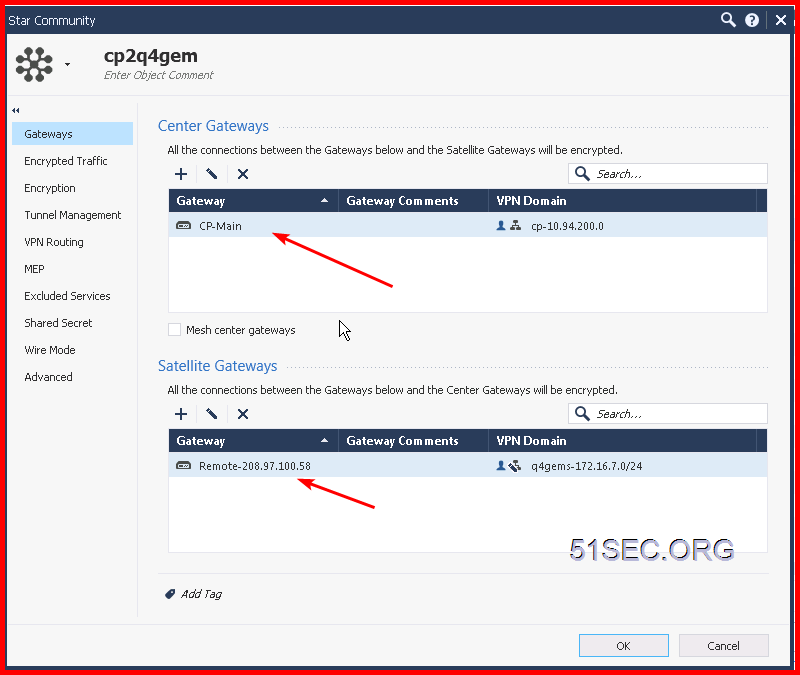
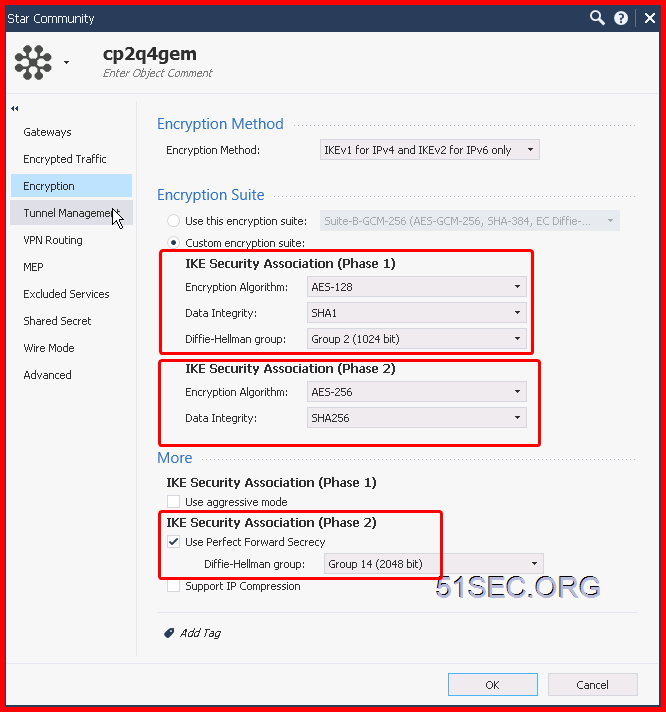
You also can create a VPN Community to add both gateways into settings:
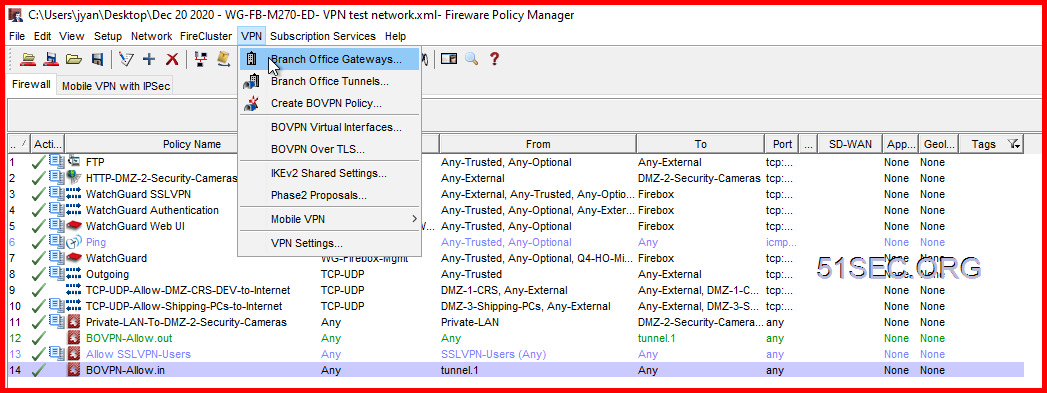
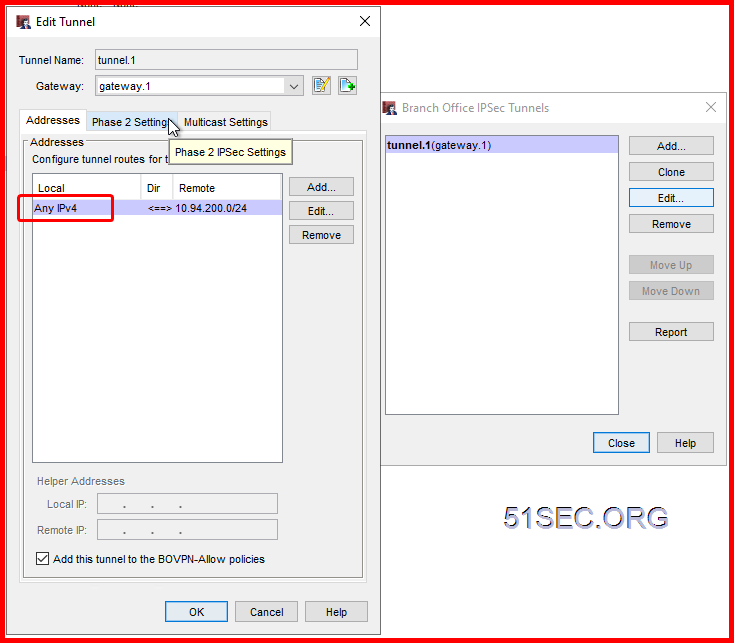
2 On WatchGuard, create a new Branch Office Gateway:
Under the Credential Method section, select Use Pre-Shared Key and enter a same key as you entered in the Checkpoint firewall.
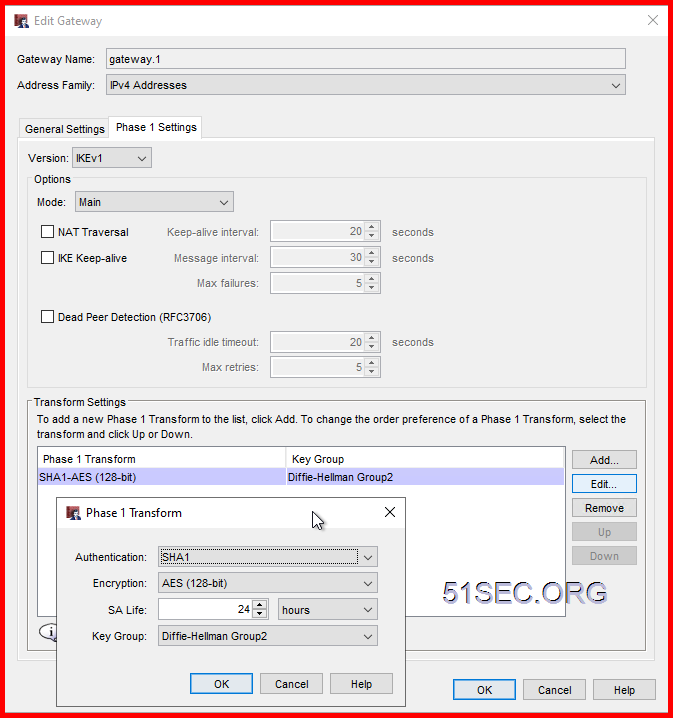
Create Phase 1 (Main) Policy
In this Lab, I am using SHA1 and AES128 with DH Group 2.
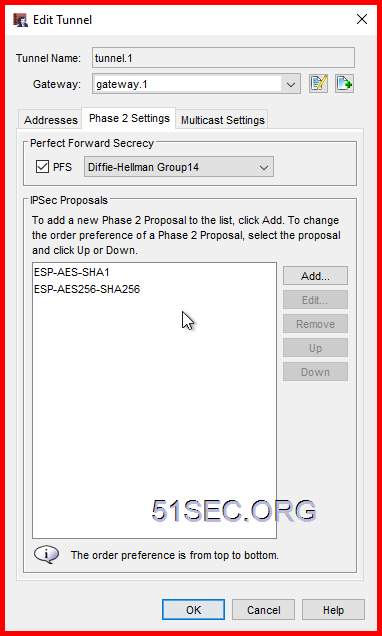
Create Phase 2 (Quick) Policy
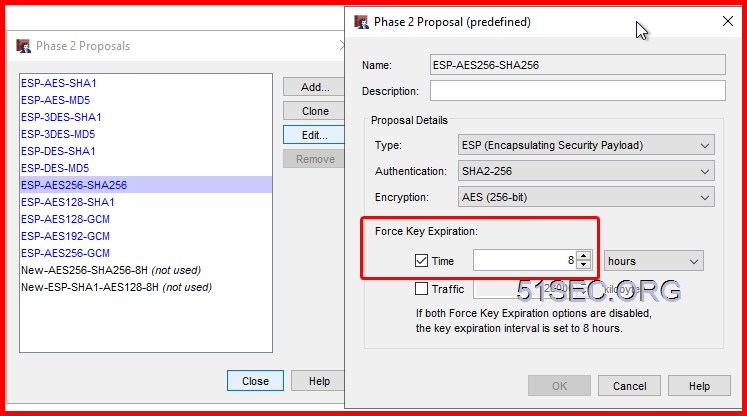
In this Lab, I am using SHA256 and AES256 with DH Group 14.
Default Phase2 Proposal can be changed at VPN menu -> Phase 2 proposals page.
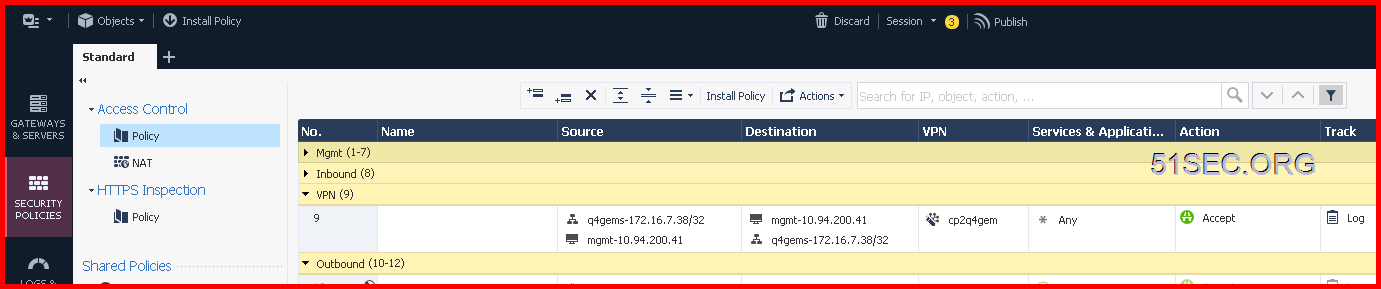
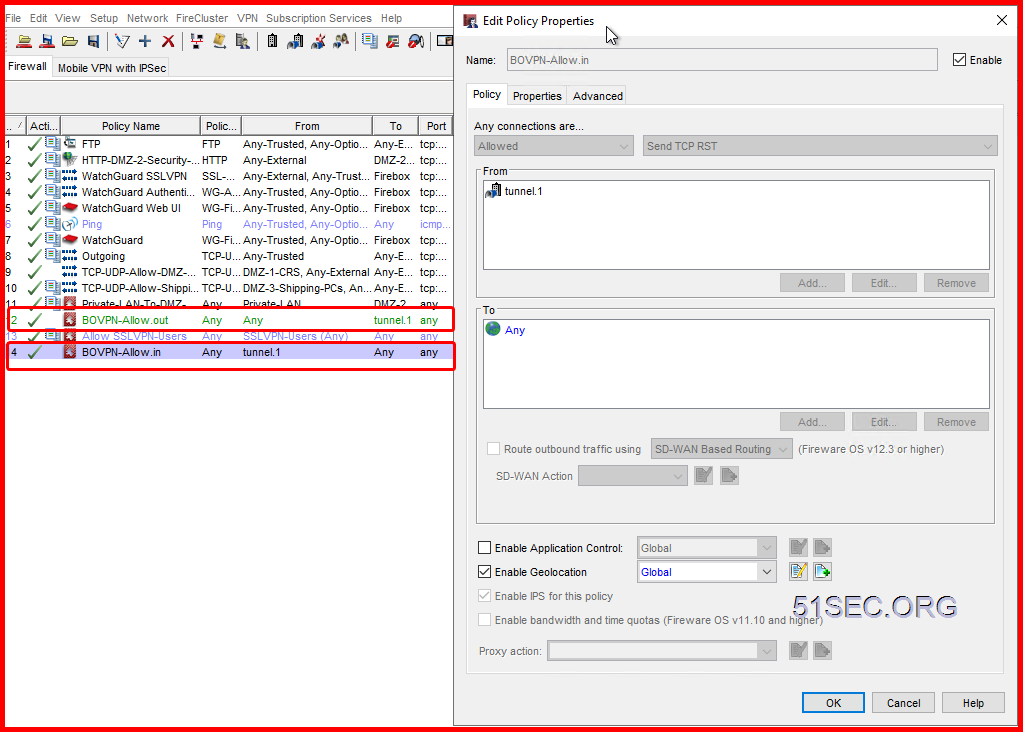
Create Firewall Policy to Allow VPN Traffic
2 On WatchGuard, it will automatically add two BOVPN rules for inbound and outbound traffic:
Test and Troubleshooting
- Ping, tracert, VPN tu, and tcpdump -nni any host <Remote VPN Gateway Public IP>
- Logs to search <Remote VPN Gateway Public IP>
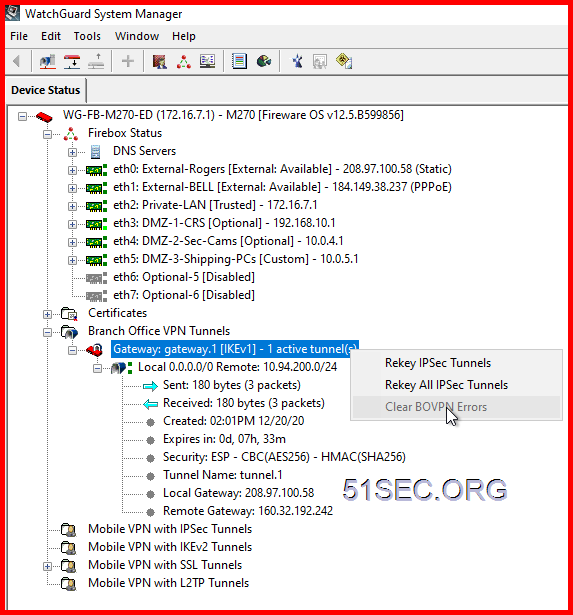
2 On WatchGuard,
WatchGuard System Manager to reset key and clear error message
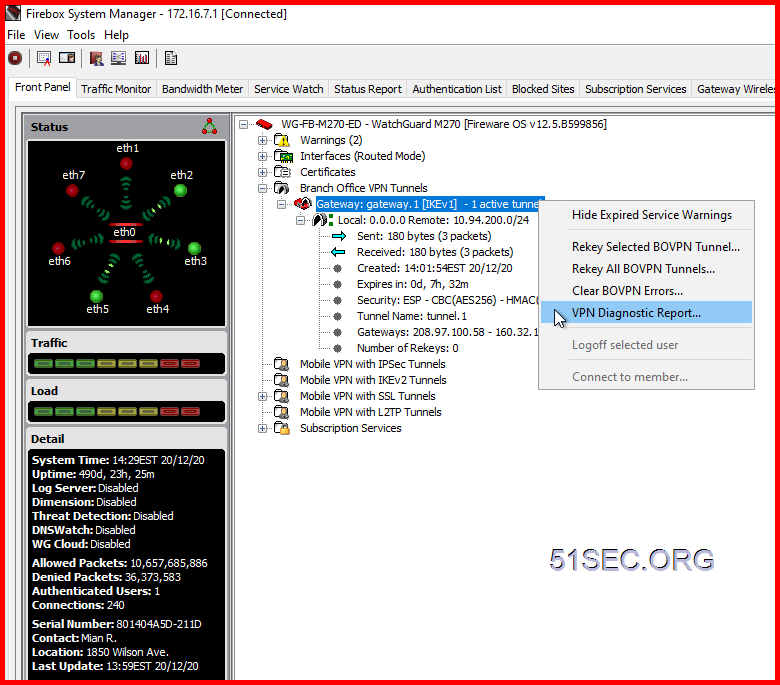
Firebox System Manager – Right Click Menu on Gateway – VPN Diagnostic Report
System Manager – Traffic Monitor
References
from Blogger http://blog.51sec.org/2020/12/create-vpn-tunnel-between-checkpoint.html