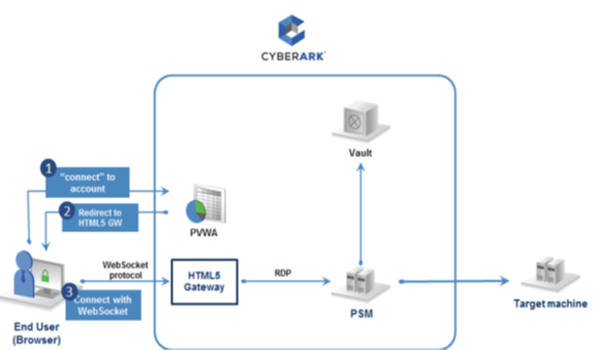
This topic describes how to configure PSM to work through an HTML5 gateway.
Overview
You can configure PSM to provide secure remote access to a target machine through an HTML5 gateway. The HTML5 gateway tunnels the session between the end user and the PSM proxy machine using a secure WebSocket protocol (port 443). This eliminates the requirements to open an RDP connection from the end user’s machine. Instead, the end user only requires a web browser to establish a connection to a remote machine through PSM.
HLD
Secure access through HTML5 requires integrating an HTML5 gateway on a Linux server. The gateway uses a software called Apache Guacamole.
Each PSM Server can be configured to work with an HTML5 gateway. Multiple PSM Servers can work with the same gateway or with different gateways. When an end user connects with an account, the PVWA redirects the connection through the gateway that is configured for the PSM server.
LLD
System Requirements
- A Web service, such as Tomcat, that can support Java 1.6 or above, The PSM Gateway supports Tomcat v 7 or above.
- Hardware specifications
Small + Mid-range implementation (1-50 concurrent RDP/SSH sessions) Mid-range + Large implementation (51-100 concurrent RDP/SSH sessions) Very large implementation (101-200 concurrent RDP/SSH sessions) 2 core processors (Intel compatible) 4 core processors (Intel compatible) 8 core processors (Intelcompatible) 4 GB RAM 8 GB RAM 16 GB RAM
Software Prerequisites
- Red Hat Enterprise Linux 7.x versions
Required libraries :
- libpng
- libjpeg
- libcairo
- OpenSSL v1.0.x
The Gateway does not support :
- Local drives mapping
- Smart card redirections
- Printers redirections
- File copy paste
- Connections to target systems where NLA is enabled on the PSM server
Install the HTML5 Gateway
This section describes how to install the PSM HTML5 Gateway.
- Deploy the HTML Webapp
- Download Tomcat.
https://tomcat.apache.org/ -
Set CATALINA_HOME to be the root folder for Tomcat. In the examples below, we use /opt/tomcat as the root folder (All scripts assume that /opt/tomcat is the root folder. If you use a different root folder, you must change these scripts.)
Command : export CATALINA_HOME=/opt/tomcat -
Run the following commands to configure Tomcat to run as a low privileged user/group
- Create a new group called tomcat:
Command : groupadd tomcat - Create a new tomcat user with a home directory of /opt/tomcat and a group of tomcat Command : useradd -M -s /bin/nologin -g tomcat -d $CATALINA_HOME tomcat
- Extract the contents of the Tomcat archive that you downloaded to /opt and rename apache-tomcat- to tomcat.
Command : cd /opt
tar -xvf apache-tomcat-.tar.gz
mv apache-tomcat- tomcat - Set up ownership
Command : chown -R tomcat:tomcat $CATALINA_HOME - Set permissions for the Tomcat server configuration file
Command : chmod 600 $CATALINA_HOME/conf/server.xml - Set up the Tomcat service script in RHEL 7.x
In the /etc/systemd/system folder, create the tomcat.service script.
[Unit] Description=Apache Tomcat Web Application Container After=syslog.target network.target [Service] Type=forking Environment=JAVA_HOME=/usr/lib/jvm/jre Environment=CATALINA_PID=/opt/tomcat/temp/tomcat.pid Environment=CATALINA_HOME=/opt/tomcat Environment=CATALINA_BASE=/opt/tomcat Environment=’CATALINA_OPTS=-Xms128M -Xmx765M -server -XX:+UseParallelGC’ Environment=’JAVA_OPTS=-Djava.awt.headless=true -Djava.security.egd=file:/dev/./urandom’
ExecStart=/opt/tomcat/bin/startup.sh ExecStop=/bin/kill -15 $MAINPID
User=tomcat Group=tomcat - Set the script permissions
chmod +x /etc/systemd/system/tomcat.service chown root:root /etc/systemd/system/tomcat.service -
Start the Tomcat service and enable it to start on boot
systemctl daemon-reload systemctl start tomcat systemctl enable tomcat
- Create a new group called tomcat:
- Secure the connection between the end user and Tomcat
- Generate a new keystore :The keystore is used for the SSL configuration. You can place it in a folder of your choice.
Self-signed certificate
- Run the following command :
keytool -genkey -alias -keyalg RSA -keystore -ext san=dns: - At the prompt, enter the keystore password and other requested information.
- Accept using the same password.
- Generate a self-signed certificate and PEM file by running the following command:
openssl req -x509 -nodes -days 365 -newkey rsa:4096 -keyout -out
For example: openssl req -x509 -nodes -days 365 -newkey rsa:4096 -keyout /opt/tomcat/key.pem -out /opt/tomcat/cert.crt When prompted, provide the requested information.
- Run the following command :
- If you have other certificates used during communication between the client and Tomcat, for each certificate do the following :
- Import the certificate using the following command:
keytool -import -alias -keystore -trustcacerts -file
For example: keytool -import -alias newkey -keystore /opt/tomcat/keystore -trustcacerts -file /opt/tomcat/cert.crt - When prompted, enter the password of the keystore you generated above.
- Accept the import of the certificate to the keystore.
- Import the certificate using the following command:
- Configure Tomcat to work with SSL and the keystore you generated in the previous step :
- In $CATALINA_HOME/conf/, open server.xml. Add the relevant connector:
- Tomcat version 9.x.x
<Connector port=”8443″ protocol=”org.apache.coyote.http11.Http11NioProtocol” maxThreads=”150″ SSLEnabled=”true” scheme=”https” secure=”true” clientAuth=”false” sslProtocol=”TLS” keystoreFile=”” keystorePass=”” /> - Locate Connector port=”8443″ and change the keystore attributes to those of your generated keystore.
Attribute Description keystoreFile The keystore path keystorePass The keystore password - Delete any additional Connector sections.
- Restart the Tomcat server. Service tomcat restart
- Generate a new keystore :The keystore is used for the SSL configuration. You can place it in a folder of your choice.
- Configure the reverse proxy for Tomcat, based on your OS.
Open the Tomcat default ports in the RHEL7 firewall (firewalld): firewall-cmd –permanent –add-forward-port=port=443:proto=tcp:toport= firewall-cmd –reload - Test the basic connection: link to https://. The Tomcat default webApp success page should appear.
- Deploy the HTML5 service
This step deploys the HTML5 service, and starts a new daemon called guacd on the system. The paths on which the HTML5 service is deployed cannot be configured.- Copy the psmgwparms.sample to /var/tmp/psmgwparms: cp /psmgwparms.sample /var/tmp/psmgwparms
- Edit the psmgwparms file: vi /var/tmp/psmgwparms
- Configure the psmgwparms as follows :
Parameter Description Value AcceptCyberArkEULA Accept the CyberArk EULA Yes WebAppsDir The name of your web application directory. For example:
/webappsWebApplicationServerUser
WebApplicationServerGroupThe name of the group and user that the web server is deployed with For example:
User: tomcat
Group: tomcatEnableJWTValidation Enable or disable JWT validation to authenticate the requests to the HTML5 gateway For details, see JWT validation Yes EndPointAddress The address of the API that generates the token for JWT validation. For example, https:///passwordvault
If EnableJWTValidation=no, there is no need to add this option to the command For details, see JWT validation - Install the RPM.
This installs the required daemon files and webapp files.
Run the following command as root: rpm -i CARKpsmgw-.rpm - Run the following command to verify that the guacd daemon service is up and running: /etc/init.d/guacd status
- Run the following command to verify that the web service is up and running: service tomcat restart
This step describes how to deploy an HTML Webapp on the server. We describe deploying the Tomcat web service.
Configure the PVWA
The following procedure describes how to configure the PVWA to work with the HTML5 Gateway server.
Add PSM HTML5 Gateway server- Log into the PVWA with an administrative user.
- Go to Administration > Options
- Right click on Privileged Session Management and select Add Configured PSM Gateway Servers.
- Select the newly added gateway server and enter a unique ID for the PSM HTML5 Gateway.
- Expand the newly created gateway server. Enter the following in the Connection Details page:
Parameter Value Address Fully qualified domain name (FQDN) of the server on which the gateway is installed, or the Virtual IP (VIP) of an HTML5 Gateway Server farm.
The address should in be the fully qualified domain name (FQDN) format and should match the SSL certificate of the PSM HTML5 Gateway machine.Port 443
Configure the PSM server to use the HTML5 gateway
Multiple PSM Servers can work with the same gateway or with different gateways. Repeat steps 3-4 for each PSM server you want to set to use the PSM Gateway.
- Log into the PVWA with an administrative user.
- Go to Options > Privileged Session Management > Configured PSM Servers.
- Select the PSM server entry that you want to set to use the PSM Gateway.
- Right click Connection Details and select Add PSM Gateway and enter the following:
Parameter Value ID The ID of the PSM Gateway that you created in Add PSM HTML5 Gateway server. Enable Yes
Use a single account for both RDP file and HTML5-based sessions
The use of shared privileged accounts often means that the same account is used by both an external third-party vendor and an internal privileged employee. While the external vendor’s access is frequently through an HTML5 browser-based session, the internal employee may prefer to connect with an RDP-file based session.
Users can use either an HTML5-based or RDP-file connection method when connecting to the remote server. The following procedures describe how to configure the PVWA so that users can select either method.
Perform this procedure for every connection component for which both connection methods should be available.
- Log in to the PVWA with an administrative user.
- Go to Options > Connection Components > {Connection Component} > User Parameters.
- Add AllowSelectHTML5. For details, refer to Connection Components.