Microsoft 365 Security Administrators proactively secure Microsoft 365 enterprise and hybrid environments, implement and manage security and compliance solutions, respond to threats, and enforce data governance.
Take one Exam to get Microsoft 365 Security Administrator Associate.
Exam MS-500: Microsoft 365 Security Administration (Skills Measured)
Implement and manage identity and access (30-35%)
Secure Microsoft 365 hybrid environments
– plan Azure AD authentication options
– plan Azure AD synchronization options
– monitor and troubleshoot Azure AD Connect events
Secure Identities
– implement Azure AD group membership
– implement password management
– configure and manage identity governance
Implement authentication methods
– plan sign-on security
– implement multi-factor authentication (MFA)
– manage and monitor MFA
– plan and implement device authentication methods like Windows Hello
– configure and manage Azure AD user authentication options
Implement conditional access
– plan for compliance and conditional access policies
– configure and manage device compliance for endpoint security
– implement and manage conditional access
Implement role-based access control (RBAC)
– plan for roles
– configure roles
– audit roles
Implement Azure AD Privileged Identity Management (PIM)
– plan for Azure PIM
– implement and configure Azure PIM roles
– manage Azure PIM role assignments
Implement Azure AD Identity Protection
– implement user risk policy
– implement sign-in risk policy
– configure Identity Protection alerts
– review and respond to risk events
Implement and manage threat protection (20-25%)
Implement an enterprise hybrid threat protection solution
– plan an Azure ATP solution
– install and configure Azure ATP
– monitor and manage Azure ATP
Implement device threat protection
– plan a Microsoft Defender ATP solution
– implement Microsoft Defender ATP
– manage and monitor Microsoft Defender ATP
Implement and manage device and application protection
– plan for device and application protection
– configure and manage Windows Defender Application Guard
– configure and manage Windows Defender Application Control
– configure and manage Windows Defender Exploit Guard
– configure Secure Boot
– configure and manage Windows device encryption
– configure and manage non-Windows device encryption
– plan for securing applications data on devices
– implement application protection policies
Implement and manage Office 365 ATP
– configure Office 365 ATP
– monitor Office 365 ATP
– conduct simulated attacks using Attack Simulator
Implement Azure Sentinel for Microsoft 365
– plan and implement Azure Sentinel
– configure playbooks in Azure Sentinel
– manage and monitor Azure Sentinel
– respond to threats in Azure Sentinel
Implement and manage information protection (15-20%)
Secure data access within Office 365
– implement and manage Customer Lockbox
– configure data access in Office 365 collaboration workloads
– configure B2B sharing for external users
Manage Azure information Protection (AIP)
– plan an AIP solution
– configure Sensitivity labels and policies
– deploy the RMS connector
– manage tenant keys
– deploy the AIP client
– integrate AIP with Office 365 Services
Manage Data Loss Prevention (DLP)
– plan a DLP solution
– create and manage DLP policies
– create and manage sensitive information types
– monitor DLP reports
– manage DLP notifications
Implement and manage Microsoft Cloud App Security
– plan Cloud App Security implementation
– configure Microsoft Cloud App Security
– manage cloud app discovery
– manage entries in the Cloud app catalog
– manage apps in Cloud App Security
– manage Microsoft Cloud App Security
– configure Cloud App Security connectors and Oauth apps
– configure Cloud App Security policies and templates
– review, interpret and respond to Cloud App Security alerts, reports, dashboards and logs
Manage governance and compliance features in Microsoft 365 (25-30%)
Configure and analyze security reporting
– monitor and manage device security status using Microsoft Endpoint Manager Admin Center
– manage and monitor security reports and dashboards using Microsoft 365 Security Center
– plan for custom security reporting with Graph Security API
– use secure score dashboards to review actions and recommendations
– configure alert policies in the Security & Compliance admin center
Manage and analyze audit logs and reports
– plan for auditing and reporting
– perform audit log search
– review and interpret compliance reports and dashboards
– configure audit alert policy
Manage data governance and retention
– plan for data governance and retention
– review and interpret data governance reports and dashboards
– configure retention policies
– define data governance event types
– define data governance supervision policies
– configure Information holds
– find and recover deleted Office 365 data
– configure data archiving
– manage inactive mailboxes
Manage search and investigation
– plan for content search and eDiscovery
– search for personal data
– monitor for leaks of personal data
– delegate permissions to use search and discovery tools
– use search and investigation tools to perform content searches
– export content search results
– manage eDiscovery cases
Manage data privacy regulation compliance
– plan for regulatory compliance in Microsoft 365
– review and interpret GDPR dashboards and reports
– manage Data Subject Requests (DSRs)
– administer Compliance Manager
– review Compliance Manager reports
– create and perform Compliance Manager assessments and action items
Learning Path:
Protect identity and access with Azure Active Directory
The Identity and Access learning path covers the latest identity and access technologies, tools for strengthening authentication, and guidance on identity protection within your organization. Microsoft access and identity technologies enable you to secure your organization’s identity, whether it is on-premises or in the cloud, and empower your users to work securely from any location. This learning path can help you prepare for the Microsoft 365 Certified: Security Administrator Associate and Microsoft 365 Certified: Enterprise Administration Expert certifications.
Define identity and access management in Azure Active Directory
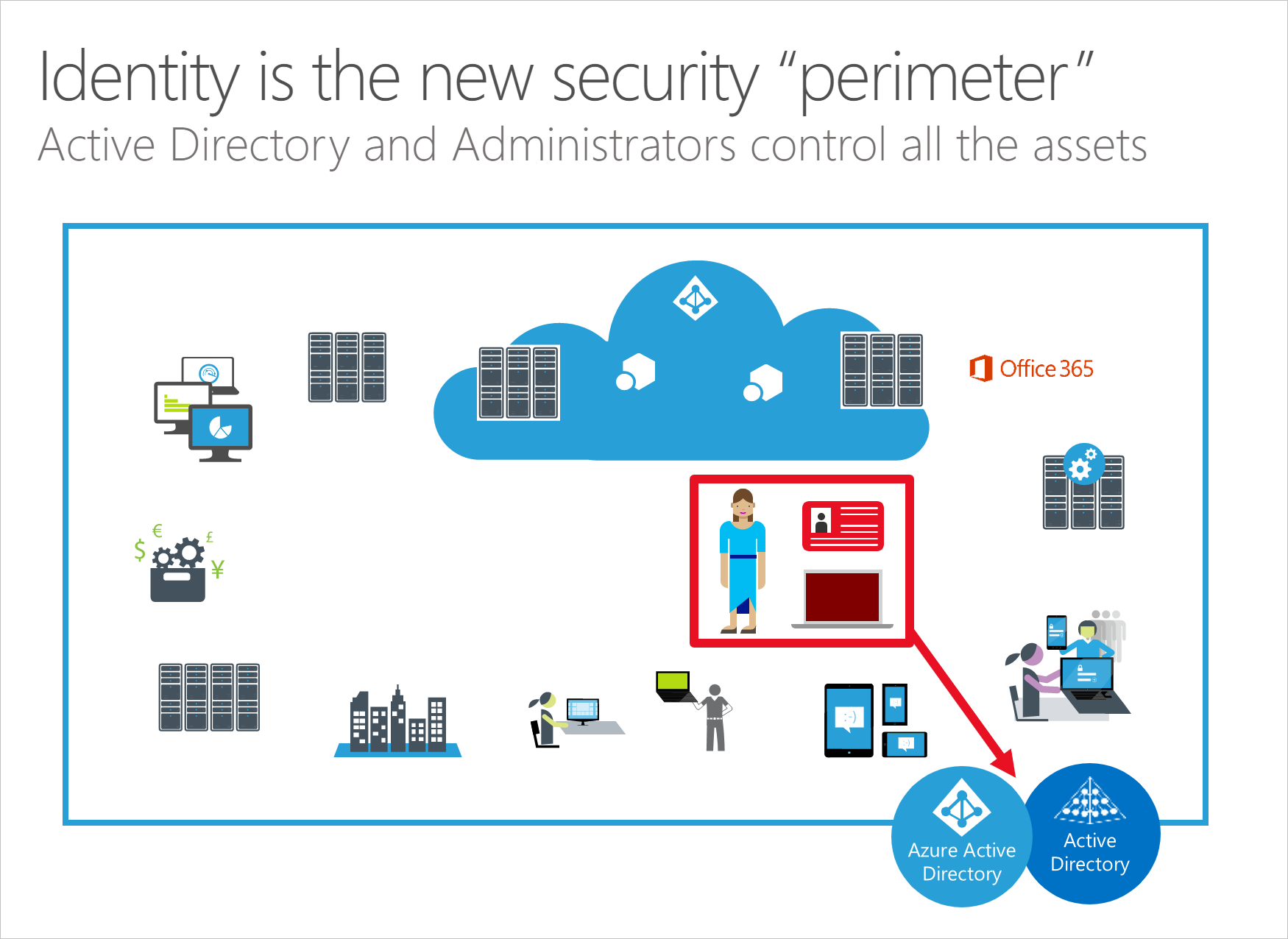
While the network perimeter keeps a basic security role, it can no longer guide the security defense strategy because:
- Adversaries have demonstrated a consistent and ongoing ability to penetrate network perimeters using phishing attacks.
- Organizational data, devices, and users often exist and operate outside traditional network boundaries (whether sanctioned by IT or not).
- Port and protocol definitions and exceptions have failed to keep up with the complexity of services, applications, devices, and data.
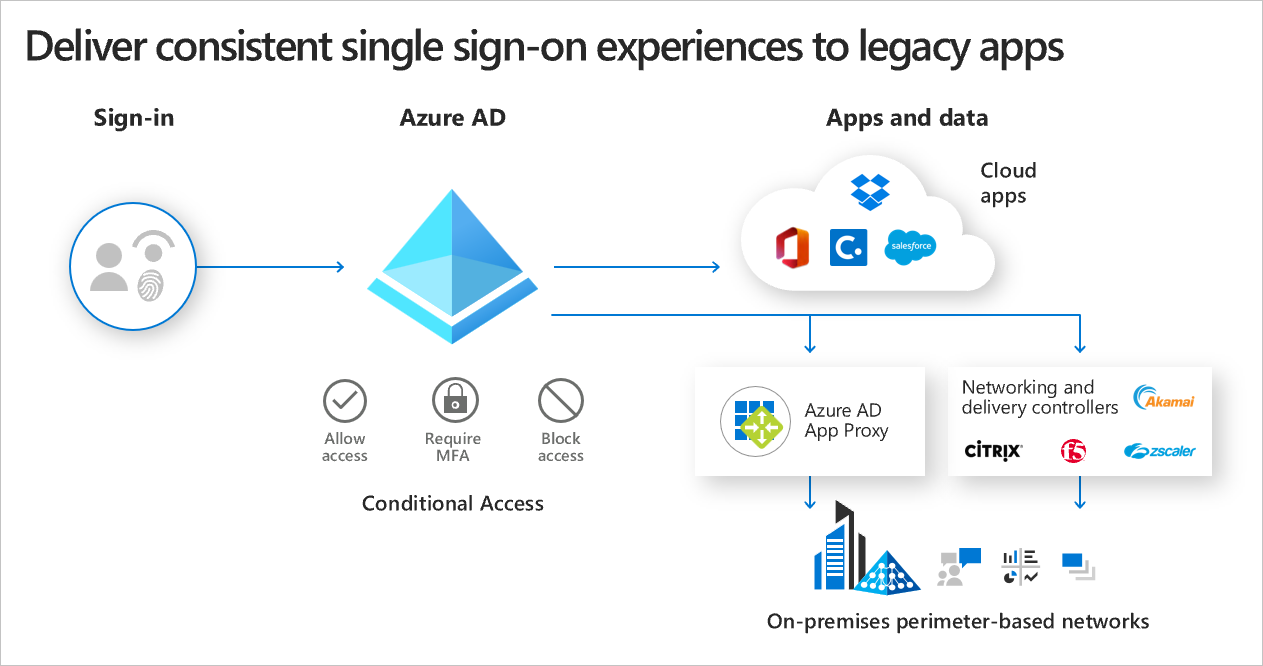
Simplify access and identity provisioning with Azure Active Directory
Sign on seamlessly to all connected apps
Configure single sign-on
Be proactive with identity governance

Azure AD Identity Governance helps manage access using the following capabilities:
- Ensuring that only authorized users have access based on policies.
- Providing employees and guest users with workflows to request access.
- Establishing regular access reviews to validate if access if still needed.
- Establishing effective controls with time-limited access for privileged roles assignments.
Video: Enable B2B Collaboration in Azure AD : Share resources security with guest user, Manage Guest Users Permissions, specify a delegated administrator at an external organization.
Strengthen authentication (conditional access) with Azure Active Directory
Enforce multi-factor authentication. Azure MFA and Conditional Access policies give you the flexibility to enable MFA for users during specific sign-on events.
Block Legacy Auth
Enable modern authentication.
Explore and implement password alternatives.
Azure AD sign-in logs can be used to determine if you’re using legacy authentication.
-
Navigate to the Azure portal > Azure Active Directory > Sign-ins.
-
Add the Client App column if it is not shown by clicking on Columns > Client App.
-
Filter by Client App > check all the Legacy Authentication Clients options presented.
-
Filter by Status > Success.
To create a Conditional Access policy to block legacy authentication, perform the following steps:
-
Create a new Conditional Access policy.
-
Target the users and groups who can be blocked.
-
Select All Cloud apps.
-
Under Conditions, select Client apps (preview), set Configure to Yes, and check only the boxes Mobile apps and desktop clients > Other clients.
-
Finally, under Access controls, select Grant > Block.
- Enable modern authentication.
- Update applications.
- Enable Exchange Online modern authentication
- Enable Skype for Business Online modern authentication.
- Block legacy authentication on your mobile device applications.
Secure administrator accounts in Azure Active Directory
Secure devices
First, you need to set up Privileged Identity Management so that users are eligible for privileged roles. In the Azure portal:
-
Open the Azure AD Privileged Identity Management blade.
-
Select Azure AD roles and then Role settings:
-
Select the role you would like to require just in time privileges.
-
Click Edit to identify the tasks required to receive privileges.
-
Provide notification rules, such that the appropriate members of your organization are aware of the permissions users have.
-
Now that you’ve configured and updated the settings for a role, in the Privileged Identity Management pane, add a member to the role by selecting Roles -> + Add Assignments. Then, select the role to be configured and members to assign.
-
Then provide the assignment type:
-
Click assign.
Within your organization, consider creating a Conditional Access policy requiring Azure multi-factor authentication for administrators for quick wins in your journey towards Zero Trust. To create a Conditional Access policy:
-
Within Azure AD, create a new Conditional Access policy with Directory roles targeted.
-
If your organization has a “break-glass” global administrator account, remember to add the account to the Exclude section. In the following screenshot, the global administrator role is selected. Consider also adding these roles:
- Authentication Administrator
- Billing administrator
- Conditional Access administrator
- Exchange administrator
- Helpdesk administrator
- Password administrator
- Security administrator
- SharePoint administrator
- User administrator
- For Cloud apps or actions, select All cloud apps:
-
Then under Conditions > Client apps (Preview), select Yes to also target apps that don’t use Modern Authentication:
-
Under Access controls, set Grant Access to Require Multi-factor authentication:
To create an Intune Mobile Application Management (MAM) without enrollment policy to protect organization data on mobile devices:
-
Within the Intune portal, select Client Apps -> App protection policies -> + Create policy -> your targeted platform:
-
After naming the policy, select from the list of available applications:
-
Under Data protection, select the controls you would like to implement. If the applications are already being used on mobile devices, consider limiting the amount of controls to reduce the amount of help-desk calls.
For iOS devices, consider the following settings:
- Blocking backup of org data to iTunes
- Restricting data sharing to only policy-managed apps
- Preventing “save as” of org data (by restricting save as functionality to OneDrive for Business or SharePoint)
- Restricting cut/copy/paste to policy-managed apps with paste in.
Policy-managed apps are the ones selected in the previous step.
-
Under Access requirements, you can configure a PIN or sign-in for accessing the targeted applications, as well as a timeout to recheck for the PIN/sign-in:
-
Finally, configure conditional launch settings that further protect the data on the device. Consider leaving the default options.
Defend against threats with Microsoft Threat Protection
Protect enterprise information with Microsoft 365
Manage security with Microsoft 365
Learn how Advanced Threat Protection (ATP) helps safeguard your organization against unknown malware, viruses, and harmful email links and attachments.