Layered Security & Defense In Depth
A layered approach to security can be implemented at any level of a complete information security strategy. Whether you are the administrator of only a single computer, accessing the Internet from home or a coffee shop, or the go-to guy for a thirty thousand user enterprise WAN, a layered approach to security tools deployment can help improve your security profile.
In short, the idea is an obvious one: that any single defense may be flawed, and the most certain way to find the flaws is to be compromised by an attack — so a series of different defenses should each be used to cover the gaps in the others’ protective capabilities. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools can each serve to protect your information technology resources in ways the others cannot.
Layered security arises from the desire to cover for the failings of each component by combining components into a single, comprehensive strategy, the whole of which is greater than the sum of its parts, focused on technology implementation with an artificial goal of securing the entire system against threats. Defense in depth, by contrast, arises from a philosophy that there is no real possibility of achieving total, complete security against threats by implementing any collection of security solutions. Rather, technological components of a layered security strategy are regarded as stumbling blocks that hinder the progress of a threat, slowing and frustrating it until either it ceases to threaten or some additional resources — not strictly technological in nature — can be brought to bear.
Layered security and defense in depth are two different concepts with a lot of overlap. They are not, however, competing concepts. A good layered security strategy is extremely important to protecting your information technology resources. A defense in depth approach to security widens the scope of your attention to security and encourages flexible policy that responds well to new conditions, helping ensure you are not blindsided by unexpected threats.
NIST Framework
The NIST Framework for Improving Critical Infrastructure Cybersecurity (NIST Cybersecurity Framework, or CSF) was originally published in February 2014 in response to Presidential Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called for the development of a voluntary framework to help organizations improve the cybersecurity, risk management, and resilience of their systems. NIST conferred with a broad range of partners from
 government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices.
government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices.
The Cybersecurity Enhancement Act of 2014 reinforced the legitimacy and authority of the CSF by codifying it and its voluntary adoption into law, until the Presidential Executive Order on “Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure” signed on May 11, 2017, mandated the use of CSF for all U.S. federal entities.
While intended for adoption by the critical infrastructure sector, the foundational set of cybersecurity disciplines comprising the CSF have been supported by government and industry as a recommended baseline for use by any organization, regardless of its sector or size. Industry is increasingly referencing the CSF as a de facto cybersecurity standard.
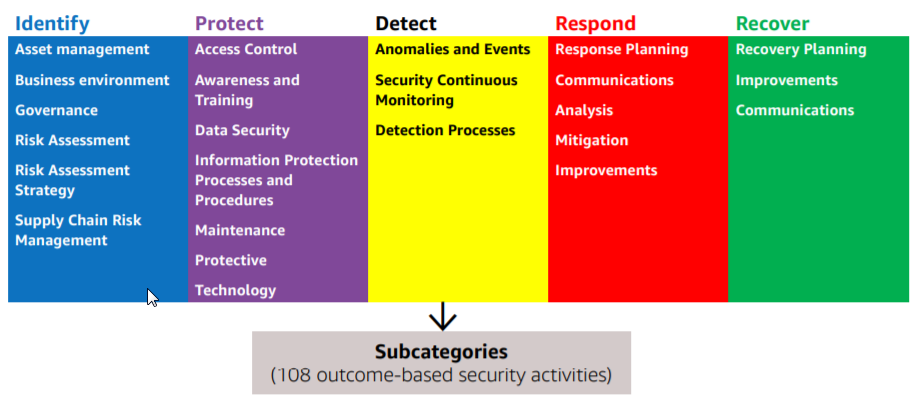
In Feb 2018, the International Standards Organization released “ISO/IEC 27103:2018 — Information technology— Security techniques — Cybersecurity and ISO and IEC Standards.” This technical report provides guidance for implementing a cybersecurity framework leveraging existing standards. In fact, ISO 27103 promotes the same concepts and best practices reflected in the NIST CSF; specifically, a framework focused on security outcomes organized around five functions (Identify, Protect, Detect, Respond, Recover) and foundational activities that crosswalk to existing standards, accreditations and frameworks.
Align NIST CSF in AWS Cloud
NIST Cybersecurity Framework (CSF) Aligning to the NIST CSF in the AWS Cloud
AWS Services and Customer Responsibility
Matrix for Alignment to the CSF
The AWS Services and Customer Responsibility Matrix for Alignment to the CSF spreadsheet assists
customers with mapping their alignment to the NIST CSF. This spreadsheet is located under the Workbooks tab
within the Resources section of the AWS Compliance website