This post is a summary for those basic IBM Guardium configuration. The IBM Guardium products provide a simple, robust solution for preventing data leaks from databases and files, helping to ensure the integrity of information in the data center and automating compliance controls.
These are the key functional areas of Guardium’s database security solution:
- Vulnerability assessment. This includes not just discovering known vulnerabilities in database products, but also providing complete visibility into complex database infrastructures, detecting misconfigurations, and assessing and mitigating these risks.
- Data discovery and classification. Although classification alone does not provide any protection, it serves as a crucial first step toward defining proper security policies for different data depending on its criticality and compliance requirements.
- Data protection. Guardium addresses data encryption at rest and in transit, static and dynamic data masking, and other technologies for protecting data integrity and confidentiality.
- Monitoring and analytics. This includes monitoring of database performance characteristics and complete visibility in all access and administrative actions for each instance. On top of that, advanced real-time analytics, anomaly detection and security information and event management (SIEM) integration can be provided.
- Threat prevention. This refers to methods of protection from cyberattacks such as distributed denial-of-service (DDoS) or SQL injection, mitigation of unpatched vulnerabilities and other database-specific security measures.
- Access management. This goes beyond basic access controls to database instances. The rating process focused on more sophisticated, dynamic, policy-based access management capable of identifying and removing excessive user privileges, managing shared and service accounts, and detecting and blocking suspicious user activities.
- Audit and compliance. This includes advanced auditing mechanisms beyond native capabilities, centralized auditing and reporting across multiple database environments, enforcing separation of duties, and tools supporting forensic analysis and compliance audits.
- Performance and scalability. Although not a security feature per se, it is a crucial requirement for all database security solutions to be able to withstand high loads, minimize performance overhead and support deployments in high-availability configurations.
The IBM Security Guardium solution is offered in two versions:
- IBM Security Guardium Database Activity Monitoring (DAM)
- IBM Security Guardium File Activity Monitoring (FAM) – Use Guardium file activity monitoring to extend monitoring capabilities to file servers.
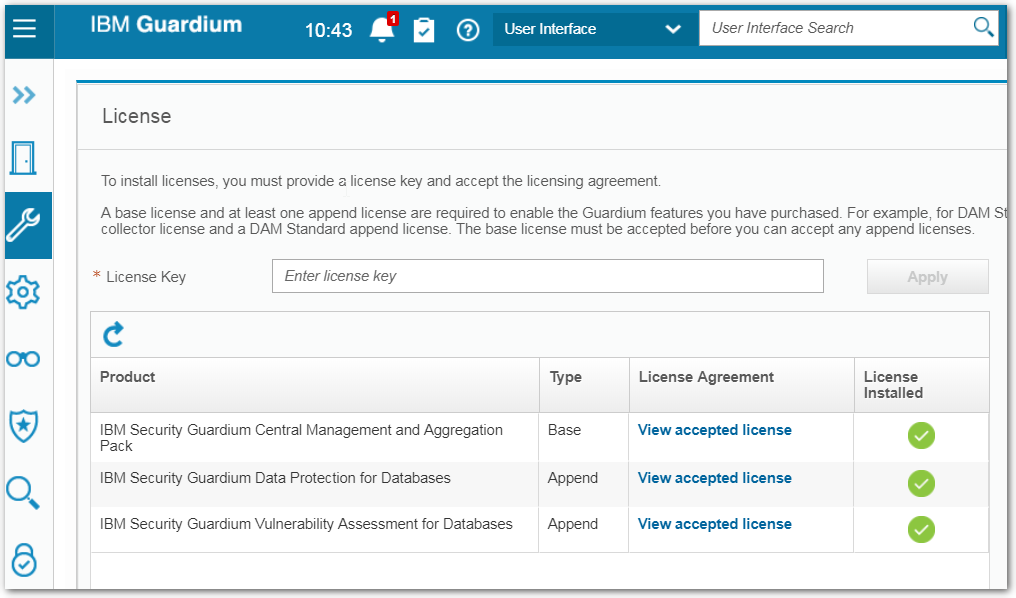
License
NTP:
login as: cli
Pre-authentication banner message from server:
|
| IBM Guardium, Command Line Interface (CLI)
|
End of banner message from server
[email protected]'s password:
Last login: Thu Jul 25 15:22:29 2019 from 10.10.136.2
Welcome cli - your last login was Tue Jul 30 01:30:02 2019
test1-igcm01.51sec.org> show system ntp all
172.21.5.10
172.21.5.11
51Secsrv11.51sec.org
51Secsrv10.51sec.org
Enabled
ok
test1-igcm01.51sec.org> show system ntp
USAGE: show system ntp <arg>, where arg is:
all, diagnostics, server, state
test1-igcm01.51sec.org> show system ntp state
Enabled
ok
test1-igcm01.51sec.org>
System Patch:
test1-igcm01.51sec.org> show system patch installed
P# Who Description Request Time Status
600 CLI Guardium Patch Update (GPU) for 2019-06-13 11:10:02 DONE: Patch installation Succeeded.
9997 CLI Health Check for GPU installati 2019-06-13 14:34:13 DONE: Patch installation Succeeded.
620 CLI Update Bundle for v10.0 GPU 600 2019-06-13 14:35:15 DONE: Patch installation Succeeded.
ok
test1-igcm01.51sec.org> show system patch ava
Attempting to retrieve the patch information. It may take time. Please wait.
P# Description Version Md5sum Dependencies
9997 Health Check for GPU installation (Apr 11 201 10.0 67dcb683682db202551ad16dd3312a95
620 Update Bundle for v10.0 GPU 600 (Apr 25 2019) 10.0 e6cd80e4b4af11a5bac132a49169f97c 600
ok
test1-igcm01.51sec.org>
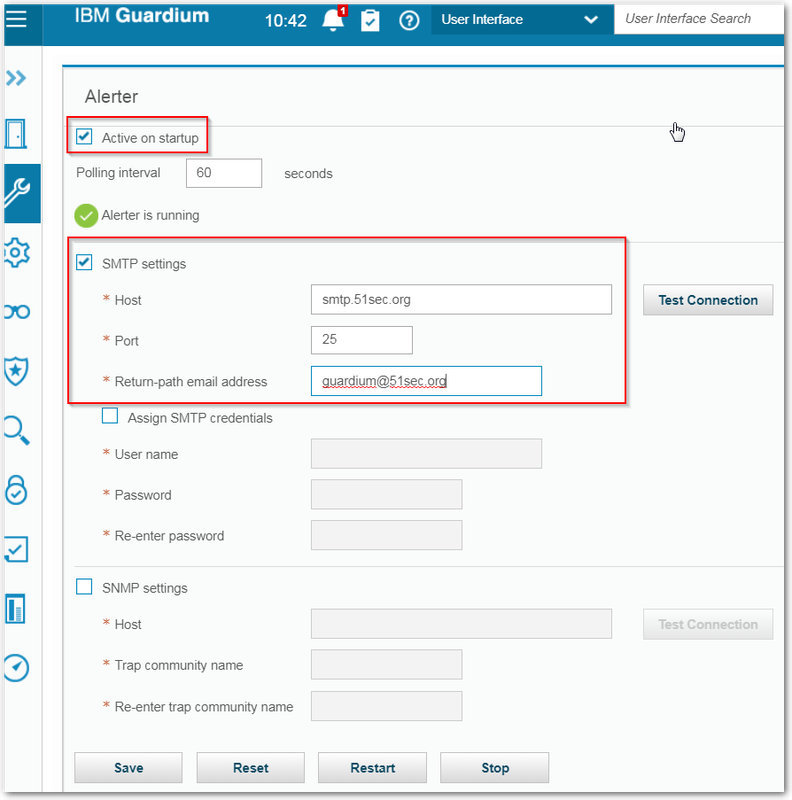
Alert – SMTP Settings
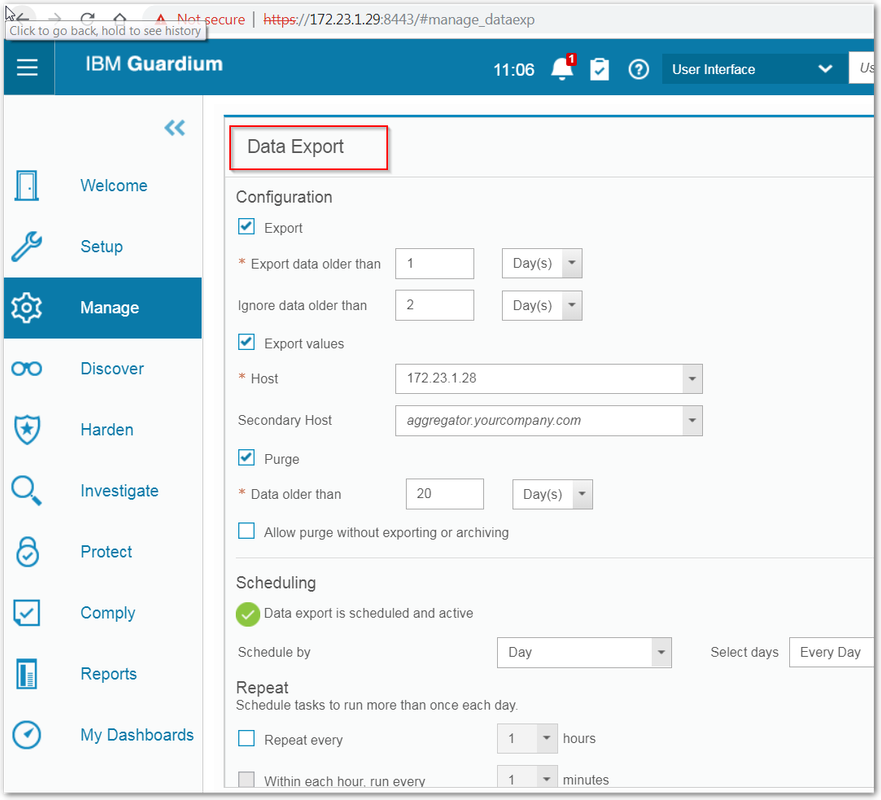
Data Export (On Collector)
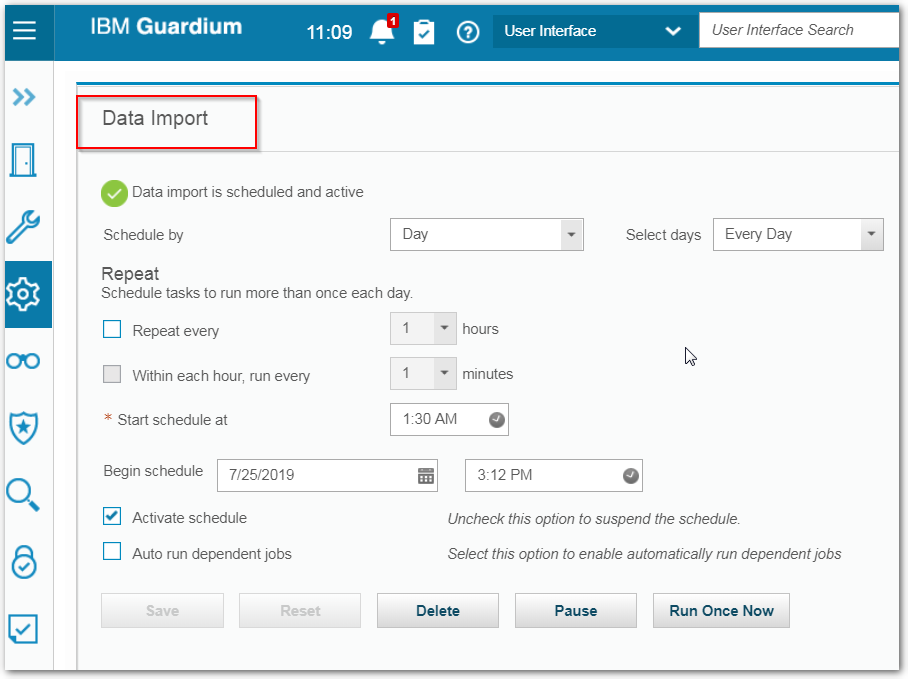
Data Import (On Aggregator or Central Manager)
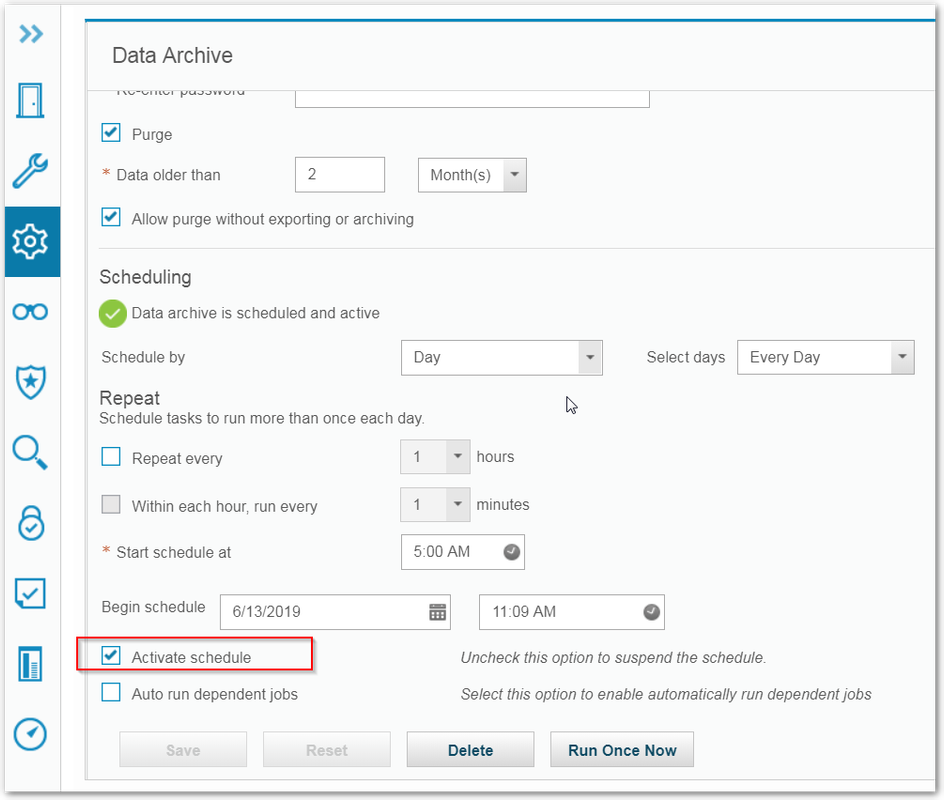
Data Archive (On Aggregator)
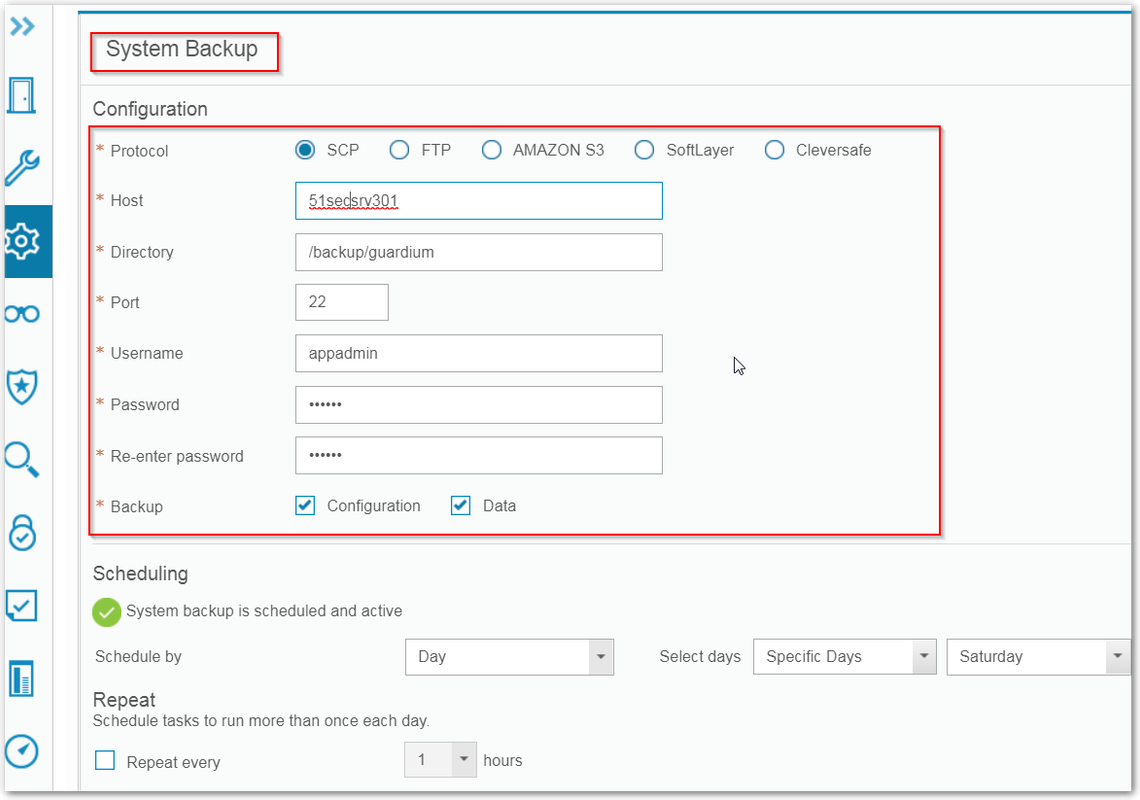
System backup (On Aggregator)
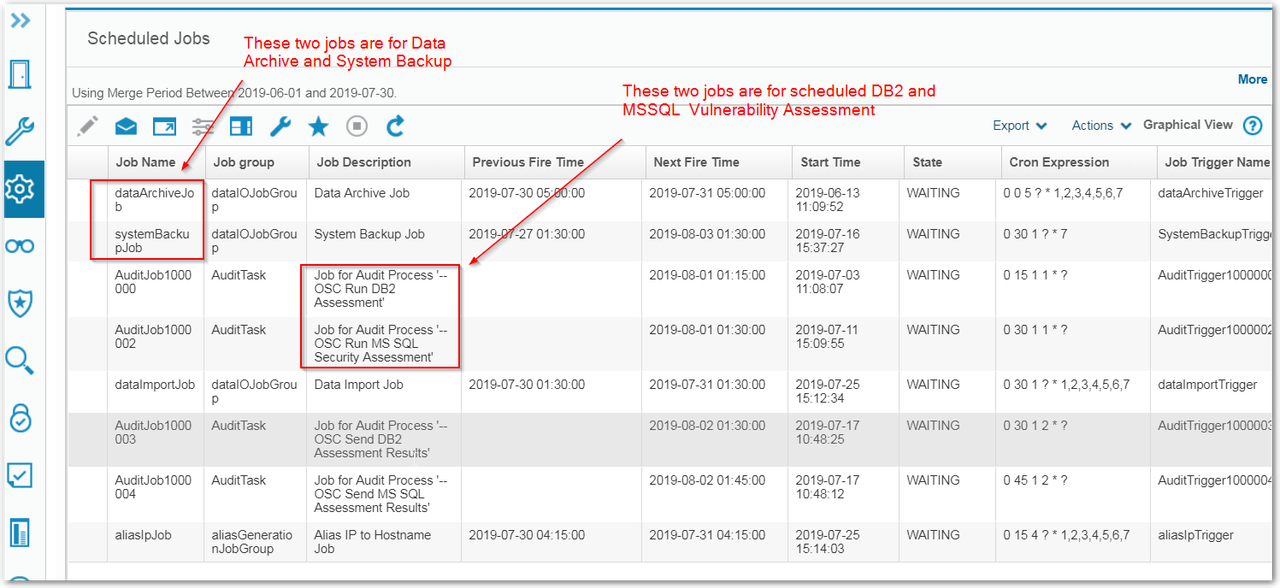
Scheduled Jobs
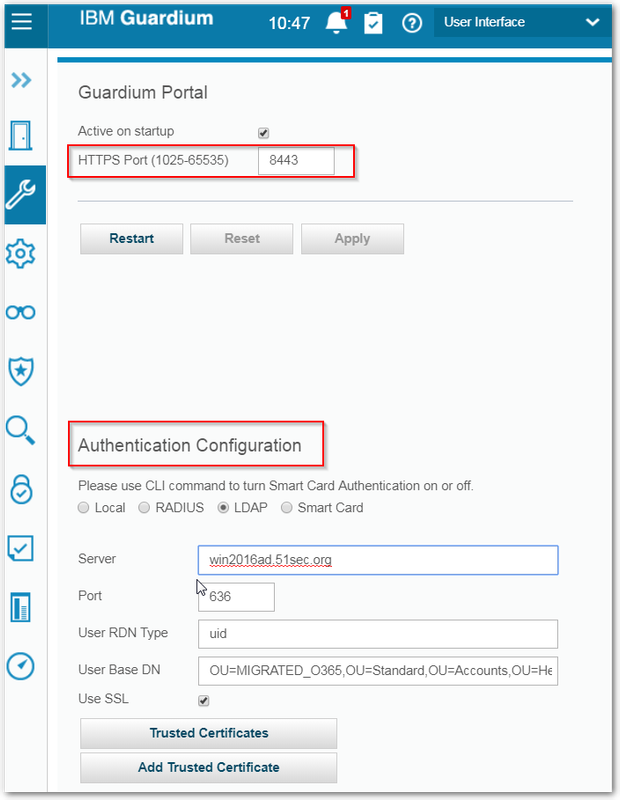
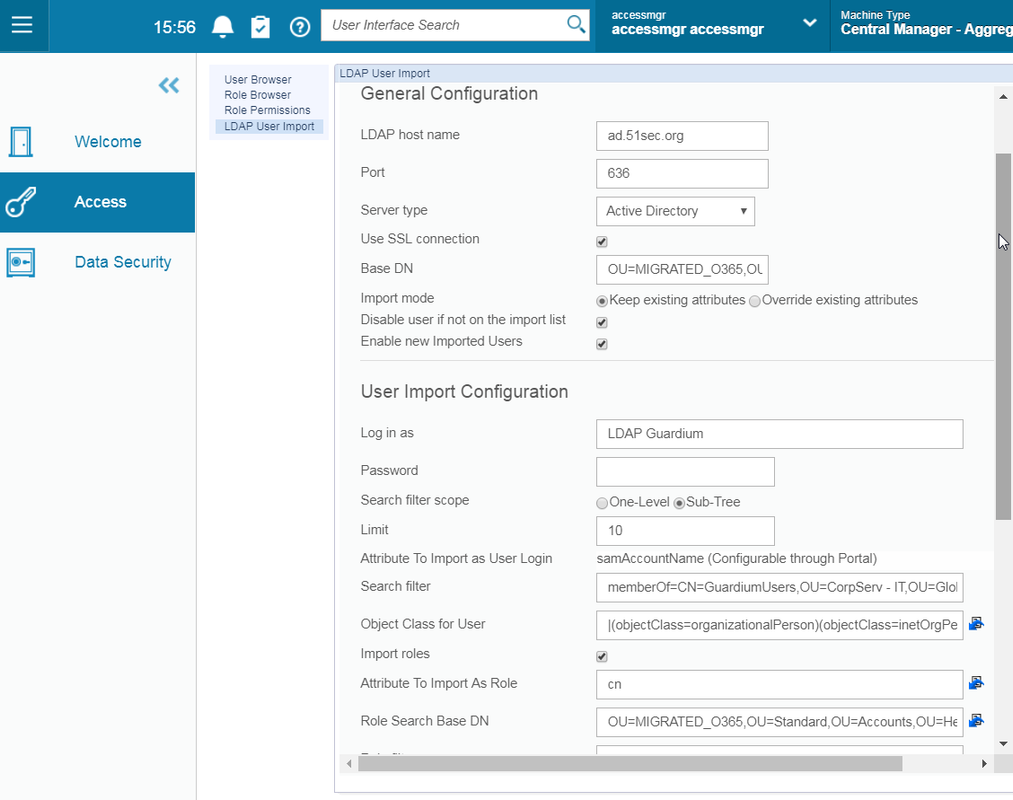
System Portal and LDAP Authentication Integration
AD Explorer from Windows Sysinternals can greatly help you find out right DN settings and filter configuration if you AD admin is not sure how to help you connect a Linux machine with Windows AD.
Syslog
It supports, CEF, LEEF and others.
From Command line, following commands will add / remove syslog host in the Guardium system.
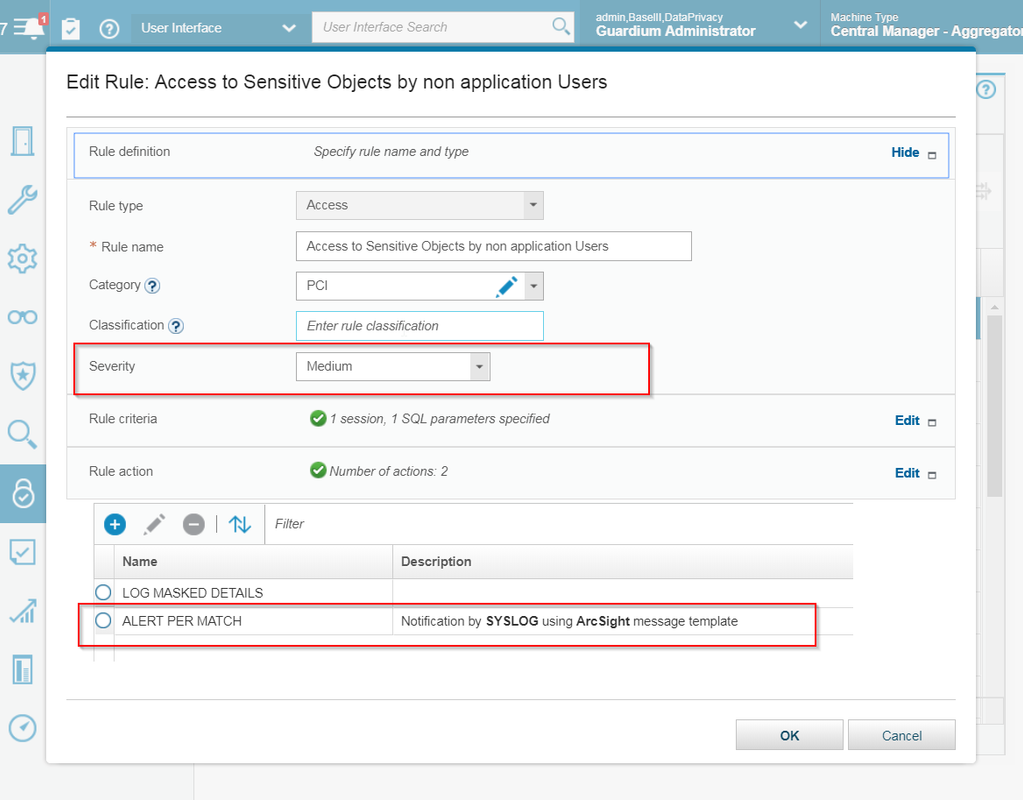
= High severity in policy
= Med severity in policy
= low severity in policy
51sec-igcm01.51Sectest.dev> store remotelog clear 10.25.14.1
Update the configuration file and restart the service.
ok
51sec-igcm01.51sectest.dev> show remotelog host
Not configured.
ok
51sec-igcm01.51sectest.dev>
store remotelog add non_encrypted daemon.alert 10.2.14.132 udp
store remotelog add non_encrypted daemon.err 10.2.14.132 udp
store remotelog add non_encrypted daemon.warning 10.2.14.132 udp
Restarting syslog server.
ok
51sec-igcm01.51sectest.dev> show remotelog host
Remote syslog is in non-encrypted mode.
Remote syslog format is default.
local7.=alert @10.2.14.132
ok
Last step is to configure policy or alert to send syslog to SIEM server, such as Qradar, ArcSight or LogRhythm.
Check the messages log for syslogs sent out
Log into Collector , not aggregator. Alert sent to Syslog server always from Collector.
References: