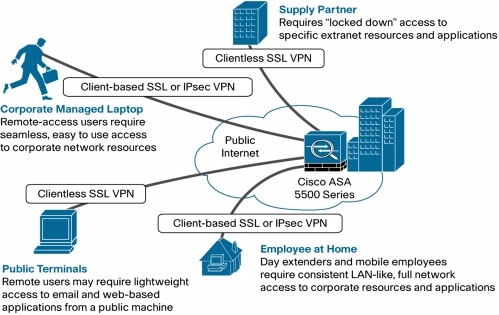
Remote access VPNs let single users connect to a central site through a secure connection over a TCP/IP network such as the Internet. Unlike other common VPN client solutions, the Clientless SSL VPN does not require that a client download and install a VPN client, all communications to the central location (where the ASA is located) are done via Secure Socket Layer (SSL) or its successor, Transport Layer Security (TLS).
This post describes how to build a remote access VPN connection using Clientless SSL VPN feature.
Related posts in this blog:
- Cisco ASA 5500-X Series Software 9.x Configuration Notes (Tips and Tricks)
- Cisco ASA Remote Access VPN Configuration 2 – Anyconnect VPN Configuration
- Cisco ASA Remote Access VPN Configuration 1 – Clientless SSL VPN Configuration
- Cisco ASAv HA Configurations
1. Topology
2. Configuration Steps
2.1 Start VPN Wizards -> Clientless SSL VPN Wizard…
2.2 Set Up SSL VPN Interface
2.3 User Authentication
2.4 Group Policy
2.5 Bookmark List
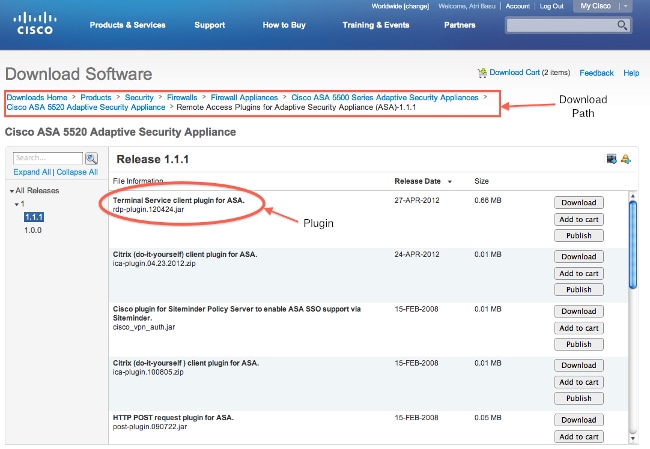
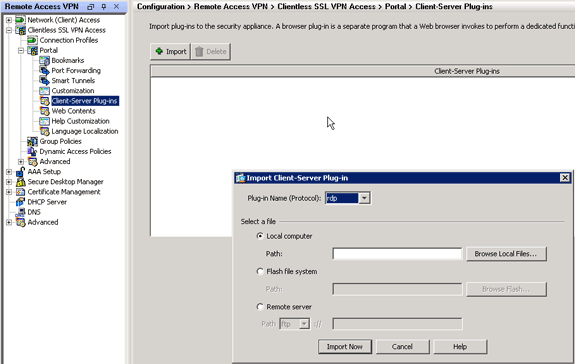
2.6 Import RDP/SSH/VNC Plug-in
2.6.1 Download RDP/SSH/VNC Java Plug-in
2.6.2 Import Plug-in
2.7 Test
3. Configuration
|
ciscoasa# show run
: Saved : : Serial Number: 9ALU3EW6LDF : Hardware: ASAv, 1024 MB RAM, CPU Xeon 5500 series 2294 MHz : ASA Version 9.5(1)200 ! hostname ciscoasa enable password 8Ry2YjIyt7RRXU24 encrypted xlate per-session deny tcp any4 any4 xlate per-session deny tcp any4 any6 xlate per-session deny tcp any6 any4 xlate per-session deny tcp any6 any6 xlate per-session deny udp any4 any4 eq domain xlate per-session deny udp any4 any6 eq domain xlate per-session deny udp any6 any4 eq domain xlate per-session deny udp any6 any6 eq domain names ! interface GigabitEthernet0/0 nameif INTERNAL security-level 100 ip address 10.9.200.12 255.255.255.0 ! interface GigabitEthernet0/1 nameif DMZ security-level 100 ip address 172.17.3.12 255.255.255.0 ! interface GigabitEthernet0/2 shutdown no nameif no security-level no ip address … ! interface Management0/0 management-only nameif MGMT security-level 0 ip address 192.168.2.12 255.255.255.0 ! ftp mode passive dns domain-lookup INTERNAL dns domain-lookup DMZ dns domain-lookup MGMT same-security-traffic permit inter-interface same-security-traffic permit intra-interface pager lines 23 logging enable logging asdm informational mtu INTERNAL 1500 mtu DMZ 1500 mtu MGMT 1500 no failover no monitor-interface service-module icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 user-identity default-domain LOCAL aaa authentication ssh console LOCAL http server enable http 192.168.2.0 255.255.255.0 MGMT no snmp-server location no snmp-server contact crypto ipsec security-association pmtu-aging infinite crypto ca trustpoint _SmartCallHome_ServerCA no validation-usage crl configure crypto ca trustpool policy crypto ca certificate chain _SmartCallHome_ServerCA certificate ca 6ecc7aa5a7032009b8cebcf4e952d491 308205ec 308204d4 a0030201 0202106e cc7aa5a7 032009b8 cebcf4e9 52d49130 0d06092a 864886f7 0d010105 05003081 ca310b30 09060355 04061302 55533117 … 6119b5dd cdb50b26 058ec36e c4c875b8 46cfe218 065ea9ae a8819a47 16de0c28 6c2527b9 deb78458 c61f381e a4c4cb66 quit telnet timeout 5 ssh stricthostkeycheck ssh 192.168.2.0 255.255.255.0 MGMT ssh timeout 5 ssh key-exchange group dh-group1-sha1 console timeout 0 threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept webvpn enable DMZ error-recovery disable group-policy sslvpn_policy1 internal group-policy sslvpn_policy1 attributes vpn-tunnel-protocol ssl-clientless webvpn url-list value test21 dynamic-access-policy-record DfltAccessPolicy username test password P4ttSyrm33SV8TYp encrypted privilege 0 username test attributes vpn-group-policy sslvpn_policy1 webvpn url-list value test21 username admin password eY/fQXw7Ure8Qrz7 encrypted username admin attributes webvpn url-list value test21 tunnel-group SSLVPN1 type remote-access tunnel-group SSLVPN1 general-attributes default-group-policy sslvpn_policy1 ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect ip-options inspect netbios inspect rtsp inspect sunrpc inspect tftp inspect xdmcp inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect esmtp inspect sqlnet inspect sip inspect skinny policy-map type inspect dns migrated_dns_map_1 parameters message-length maximum client auto message-length maximum 512 ! service-policy global_policy global prompt hostname context no call-home reporting anonymous call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email [email protected] destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily profile License destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination transport-method http hpm topN enable Cryptochecksum:933e07d913ddf455a108be19e0e61f9b : end ciscoasa# |
Reference
- ASA 8.x Import RDP Plug-in for use with WebVPN Configuration Example
- ASA Clientless SSLVPN: RDP Plug-in Issues
- Configuring Cisco ASA Clientless SSL VPN