To view Firewall Configuration Essentials 101 Course, please login to the Palo Alto Networks Learning Center.
[Updating]
1. Palo Alto Networks Platforms
The PA-500, PA-200, and VM-Series firewalls do not support virtual systems. High Availability and Aggregated interfaces are also only supported on higher models of the product.
The even-numbered platforms are older platforms. The PA-4000 is End-of-Sale. The PA-3000 and PA-5000 models use superior hardware, such as Cavium chips and SSD for logging. The PA-7050 is a chassis architecture.
The Control Plane has its own dual core processor, RAM, and hard drive. This processor is responsible for tasks such as management Ul, logging, and route updates.
The Data Plane contains three types of processors that are connected by high speed 1Gbps busses:
- Signature Match Processor: Performs vulnerability and virus detection
- Security Processors: Multi-core processors, which handle security tasks such as SSL decryption
- Network Processor: Responsible for routing, NAT, and network layer communication
- Connect a serial cable from your computer to the Console port and connect to the firewall using terminal emulation software (9600-8-N-1). Wait a few minutes for the boot-up sequence to complete; when the device is ready, the prompt changes to the name of the firewall, for example PA-500 login .
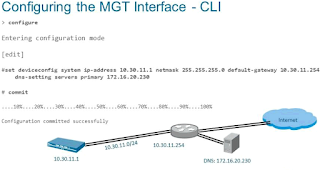
- Connect an RJ-45 Ethernet cable from your computer to the MGT port on the firewall. From a browser, go to https://192.168.1.1 . Note that you may need to change the IP address on your computer to an address in the 192.168.1.0 network, such as 192.168.1.2, in order to access this URL.
2.2 Configuration Management
- Candidate Config: When you change a configuration setting and click OK, the current or “candidate” configuration is updated; not the active or “running” configuration.
- Running Config: Clicking Commit at the top of the page applies the candidate configuration to the running configuration, which activates all configuration changes since the last commit.
2.3 Licensing and Software Updates
2.4 Account Administration
2.5 Administrative Controls
CLI Mode:
- Operational Mode
- Configuration Mode
CLI Tools:
- ?
- Find command keyword fpga
- show
- ping
3. Basic Interface Configuration
3.1 Security Zones
3.2 Interface Types
- Tap Mode
- Decryption Mirror
- Virtual Wire Interface
- Layer 2
- Layer 3 (Virtual Router, IP Addressing, DHCP, Interface Management Profile)
3.3 IPv4 and IPv6
3.4 DHCP
3.5 Interface Management
- Loopback
- Aggregrate
4. Security and NAT Policies
4.1 Security Policy Overview
4.2 Security Policy Administration
Security Zone Rules – Three types
- Intrazone
- Interzone
- Universal
4.3 Network Address Translation (NAT)
Source NAT
- Static IP
- Dynamic IP
- Dynamic IP/Port (DIPP)
Destination NAT
5. Basic App-ID
Application Identification (App-ID)
App-ID Overview
Application Groups and Filters
6. Basic Content-ID
Content-ID Overview
Security Profiles
Security Profile Administration
Zone Protection Profile
7. Decryption
Certificate management
Outbound SSL Decryption
Inbound SSL decryption
Other Decryption Topics
8. Basic User-ID
Configuring User-ID
Mapping Users to Group
Working with the Windoes User-ID Agent
Mapping Users to IP Addresses: Syslog Integration
9. Site-to-Site VPNs
Site-to Site and Client VPNs
Site-to-Site VPN
Configuring Site-to-Site Tunnels
IPSec Troubleshooting
10. Management and Reporting
Dashboard
Basic Logging
Viewing and Filtering Logs
Basic Reports
11. Active/Passive High Availability
Active/Passive High Availability Overview
Active/Passive Configuration
Managing Split Brain
Monitoring
Active/Active Overview
12. Panorama
Panorama Overview
Centralized Configuration and Deployment
Centralized Logging and Reporting
Role-Based Access Control
- Types of roles