Part 1: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 1 (Local User Authentication)
Part 2: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 2 (AD Authentication)
Part 3: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 3 (Certs and Two Factor Authentication)
Part 4: Enable Checkpoint SSL VPN Remote Access: Step by Step Part 4 – Two Factor Authentication (AD and SMS)
In previous lab Part 1 “Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 1 (Local User Authentication)“, it shows the first part how to enable Checkpoint SSL VPN with local user authentication and how to add a native application. In this second part of lab, it will show the integration with Active Directory accounts for remote ssl vpn access.
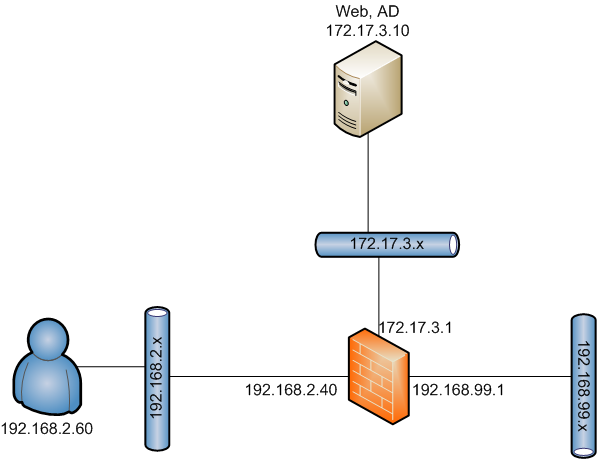
Topology:
Steps:
1. Enable Identity Awareness Blade in Check Point gateway properties to start Identity Awareness Configuration wizard:
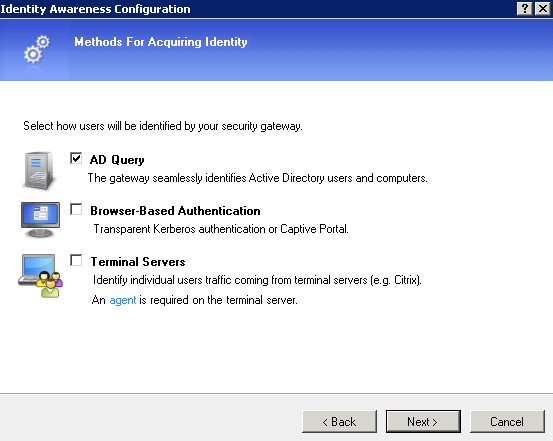
2. Choose AD Query at Methods for Acquiring Identity window.
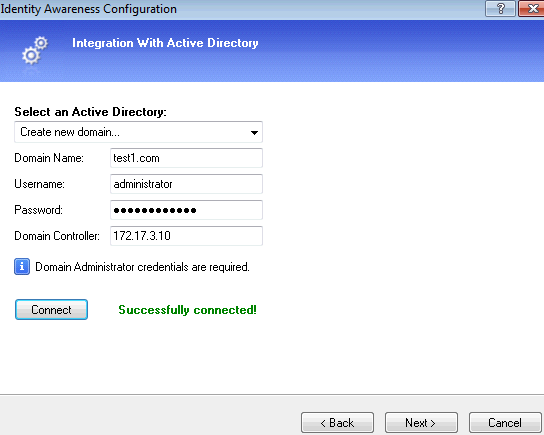
3. Add new Active Directory
4. Finish the configuration wizard
5. Add AD Group into Mobile Access Policy as show in the rule No. 2.
6. Use AD account ‘test’ to do test
After log in, it only shows Native Application Section to connect. If account is not defined in the any mobile access rule, the login window will show “User is unauthorized” although there is account in the AD.