Part 1: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 1 (Local User Authentication)
Part 2: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 2 (AD Authentication)
Part 3: Enable Checkpoint SSL VPN Remote Access: Step by Step Instruction Part 3 (Certs and Two Factor Authentication)
Part 4: Enable Checkpoint SSL VPN Remote Access: Step by Step Part 4 – Two Factor Authentication (AD and SMS)
Check Point has a Mobile Access Blade to provide the SSL VPN featured solution to remote users. In this lab, it will show the step by step instruction with captured screenshots how to enable Checkpoint Remote SSL VPN with Checkpoint Local User Authentication.
Check Point has a number of different remote access solutions to use in different situations. the following table has a quick view on the difference of them.
Remote Access Solution Comparison:
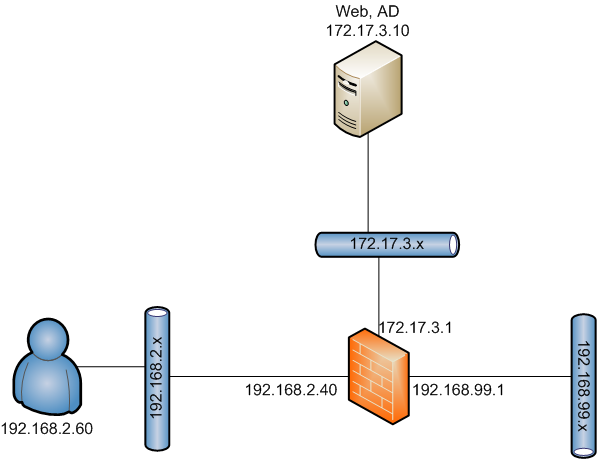
Topology:
Steps to enable Mobile Blade with local Checkpoint user authentication:
1. Check the Mobile Blade from Gateway Properties:
2. Customize your portal URL and Import Certs.
By default, the portal will use Checkpoint Self-signed certificate which will cause your browser warning message.
3. Customize Your Remote Access Applications:
4. Skip the Active Directory Integration.
Local Account will be used in this Part 1. Later certificate and two factor authentication will be added into part 2, part 3 and part 4.
5. Test your customized web application
6. Create Local Test User
7. Finished the activation of Moile Access Blade.
8. Gateway Properties and Mobile Access Policy
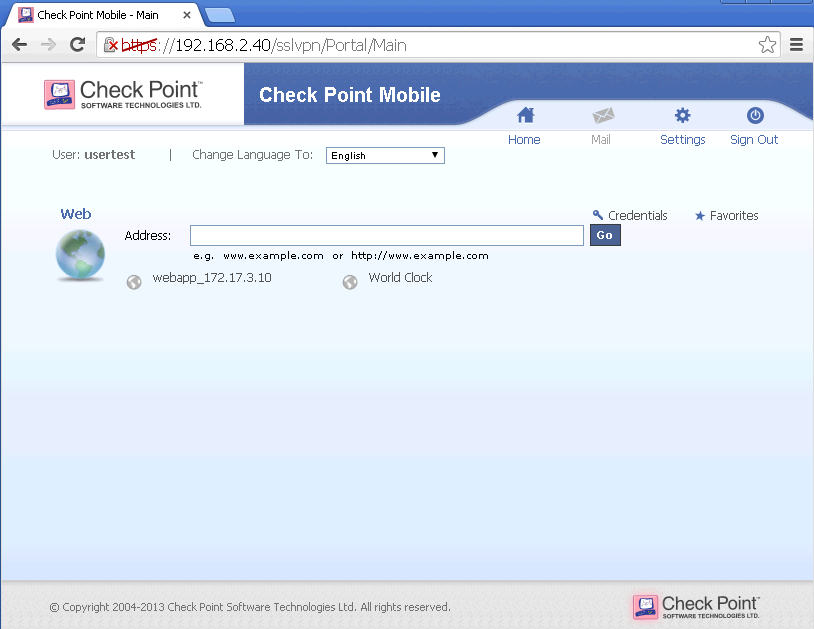
9. Log into Mobile Access Portal:
10. Test the custom web application
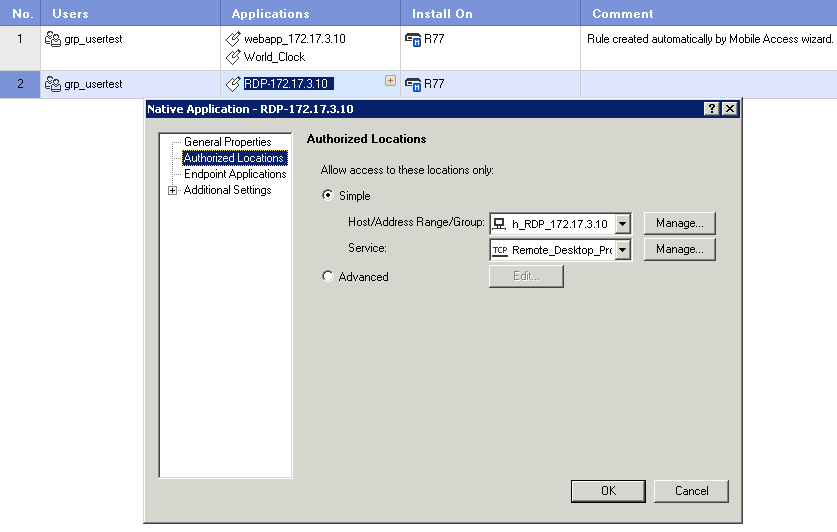
Add a new native application – RDP:
1. New -> Native Application:
2. Choose the predefined host and service
3. Take a look at policy rules and application properties:
4. Web Portal for Native Applications:
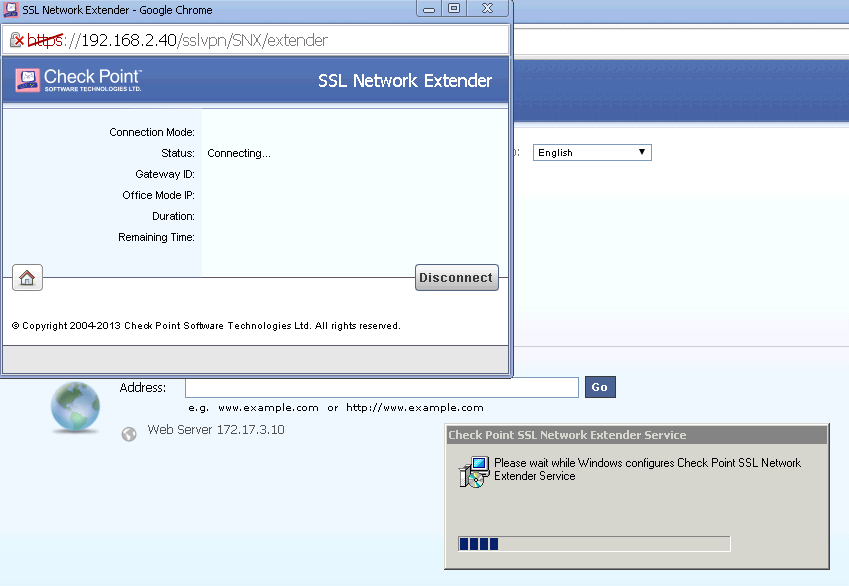
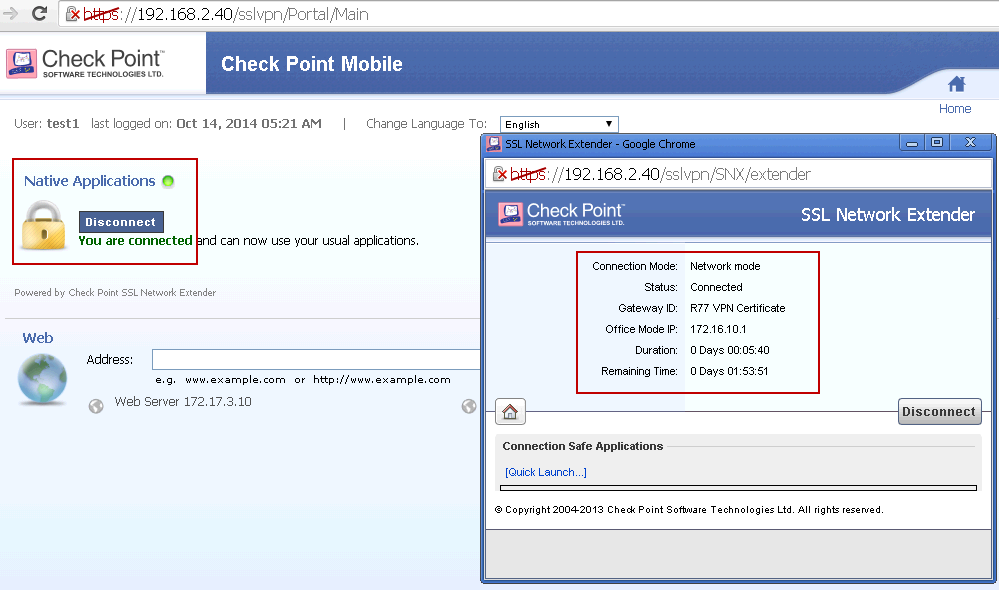
5. Click Connect button you will get some prompted windows such as following:
There is SSL Network Extender Agent will be installed on the first time connection:
6 After Connected